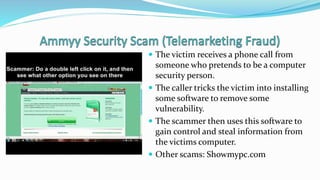
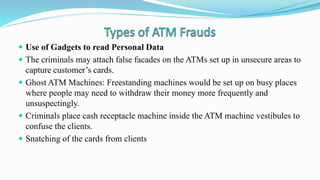
Fraud and identity theft take many forms in the cyber world. Cybercriminals may steal identities by hacking into systems to access personal information, employ social engineering to trick victims into giving away information, or use malware to gain control of devices and networks. Common scams include phishing emails designed to steal login credentials or money transfer scams promising a share of a large sum in exchange for upfront fees. Individuals can protect themselves by using strong passwords, updating security software, backing up data securely, and limiting what personal information they share online or with unknown parties. New forms of cybercrime are constantly emerging, so vigilance is important.