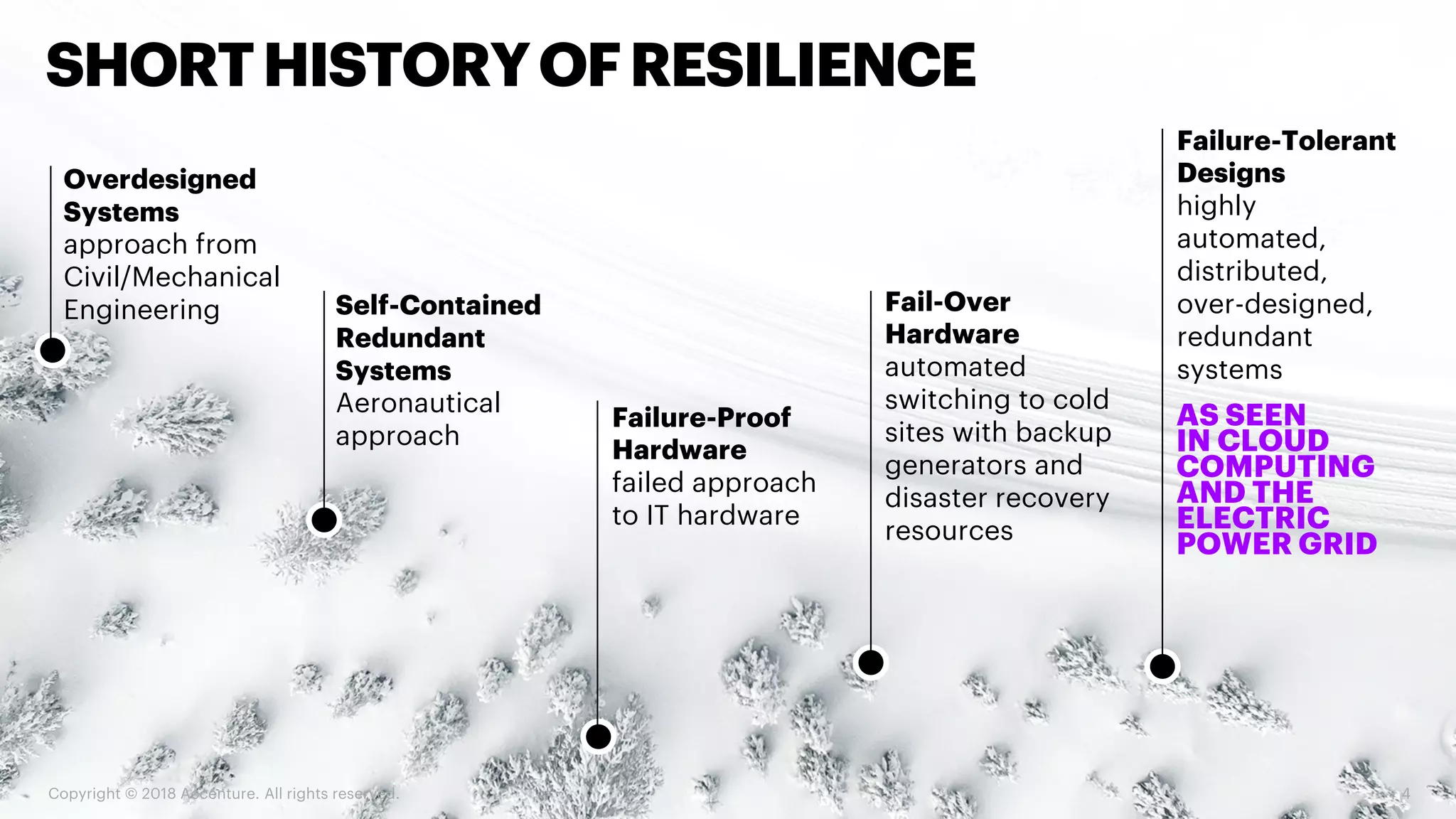
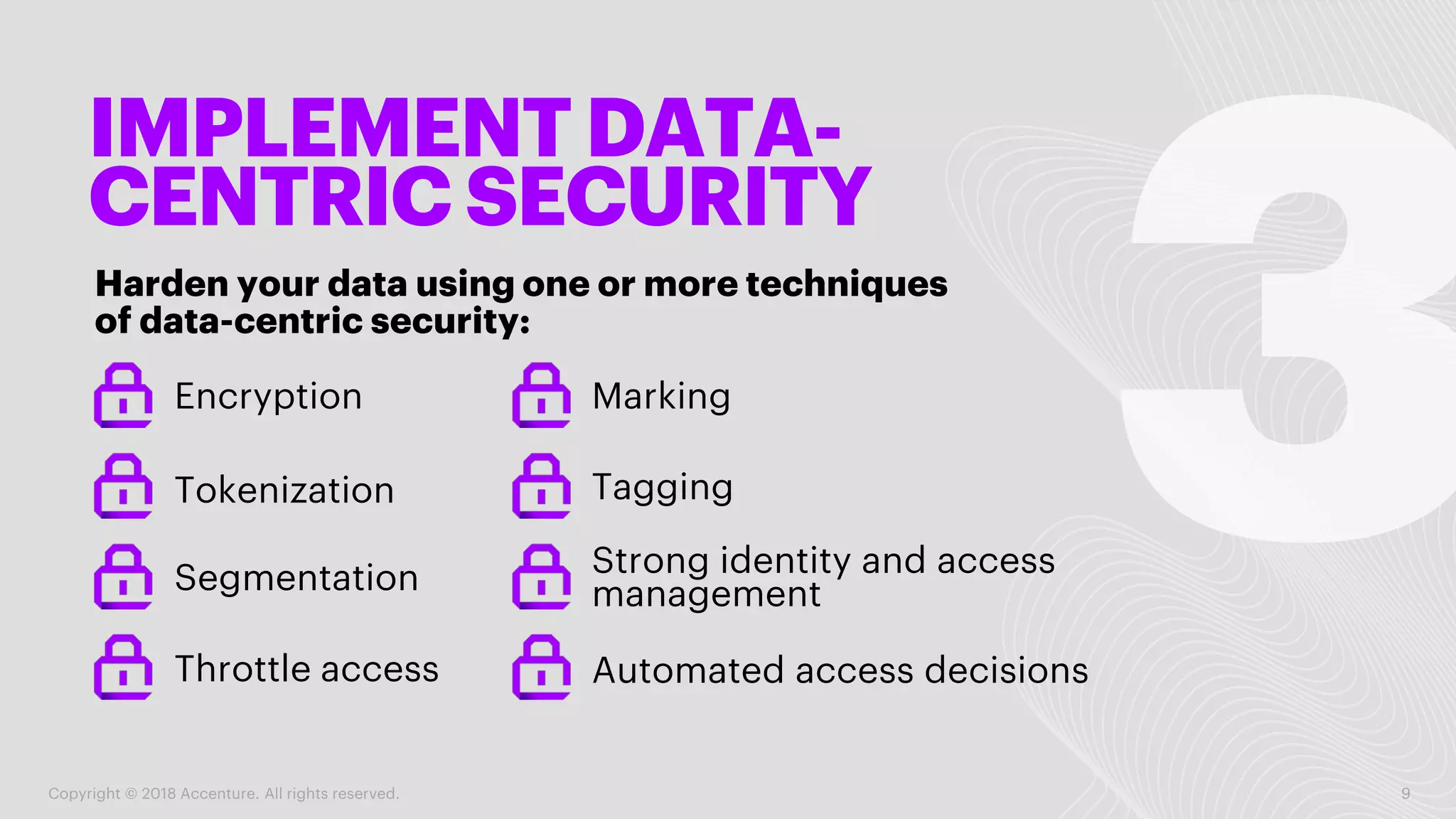
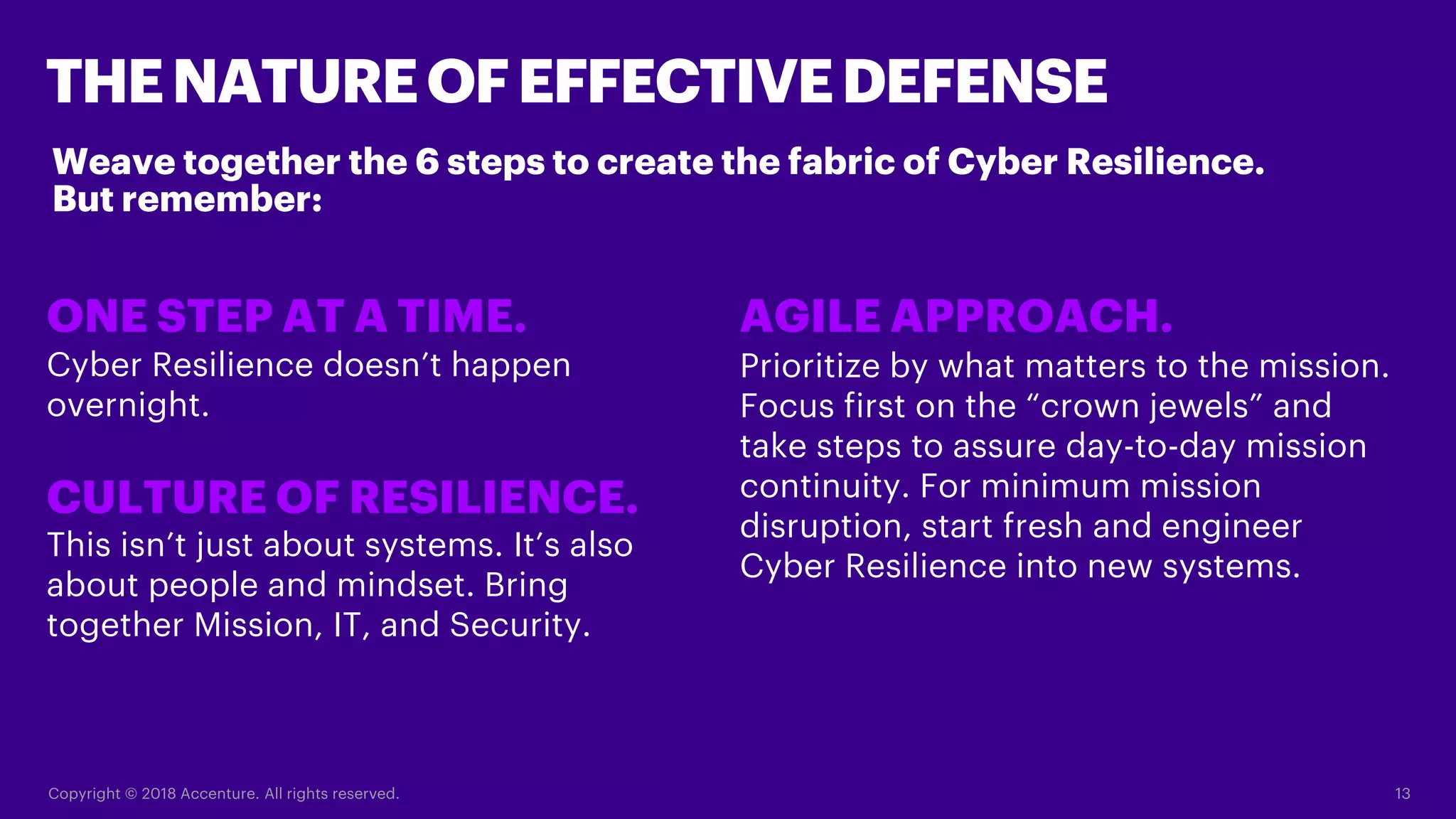
The document emphasizes the shift from traditional cybersecurity to a more proactive approach known as cyber resilience, which focuses on maintaining system functionality despite cyber threats. It outlines several strategies including adopting cloud security, implementing data-centric security measures, and fostering a culture of resilience within organizations. Additionally, it encourages anticipating attacks and integrating security throughout the development process to minimize vulnerabilities.