Embed presentation
Download to read offline

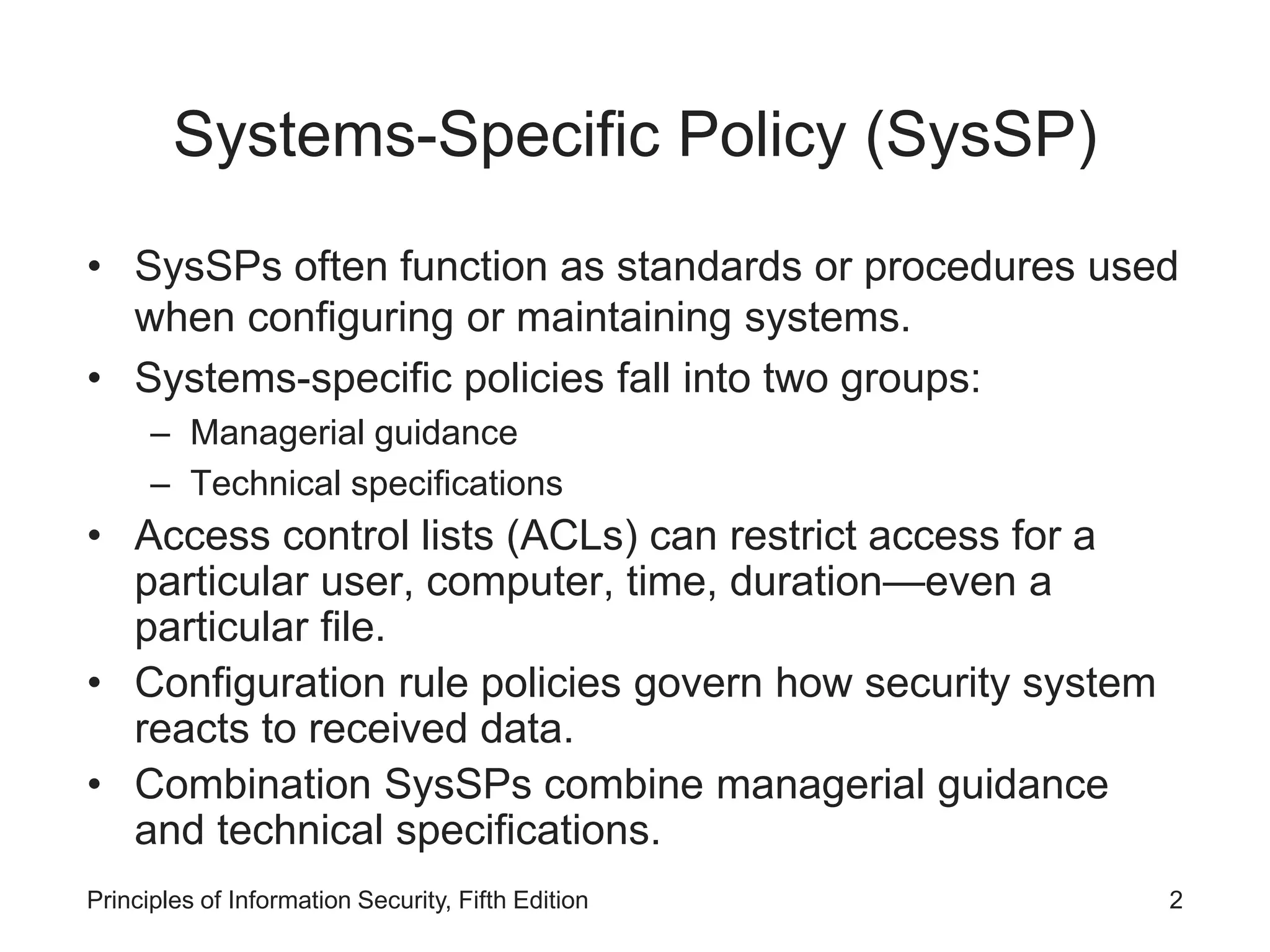



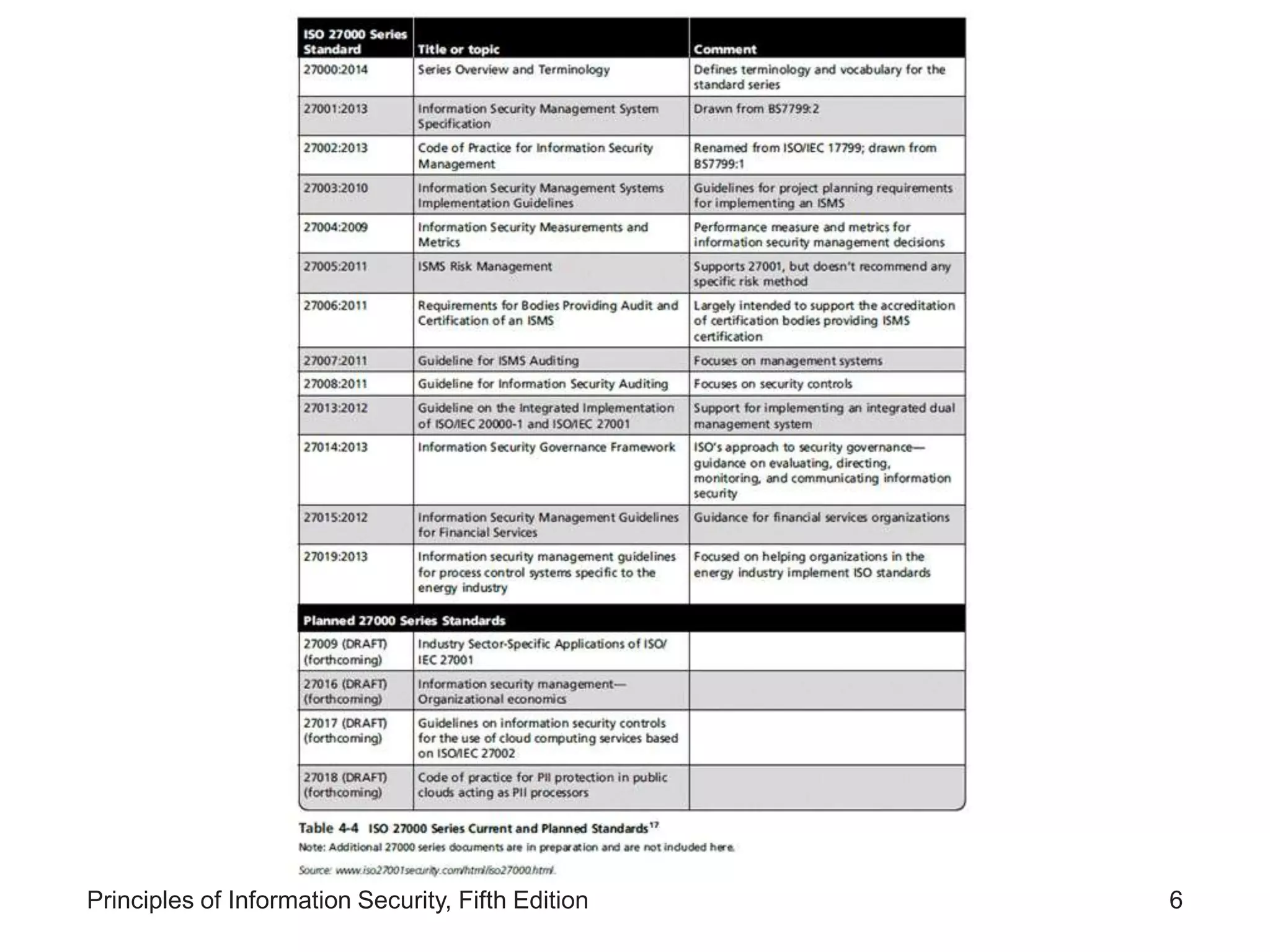
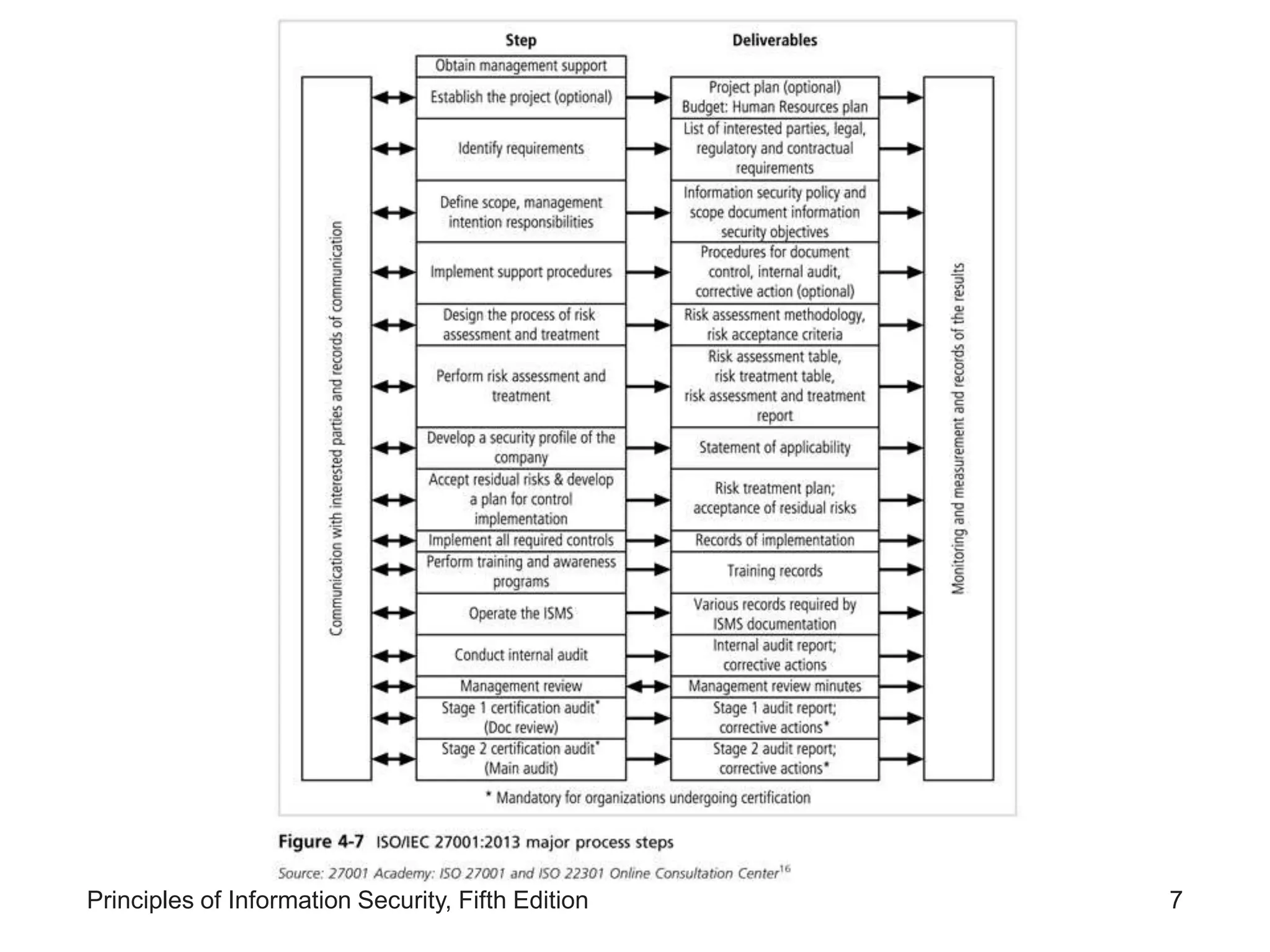
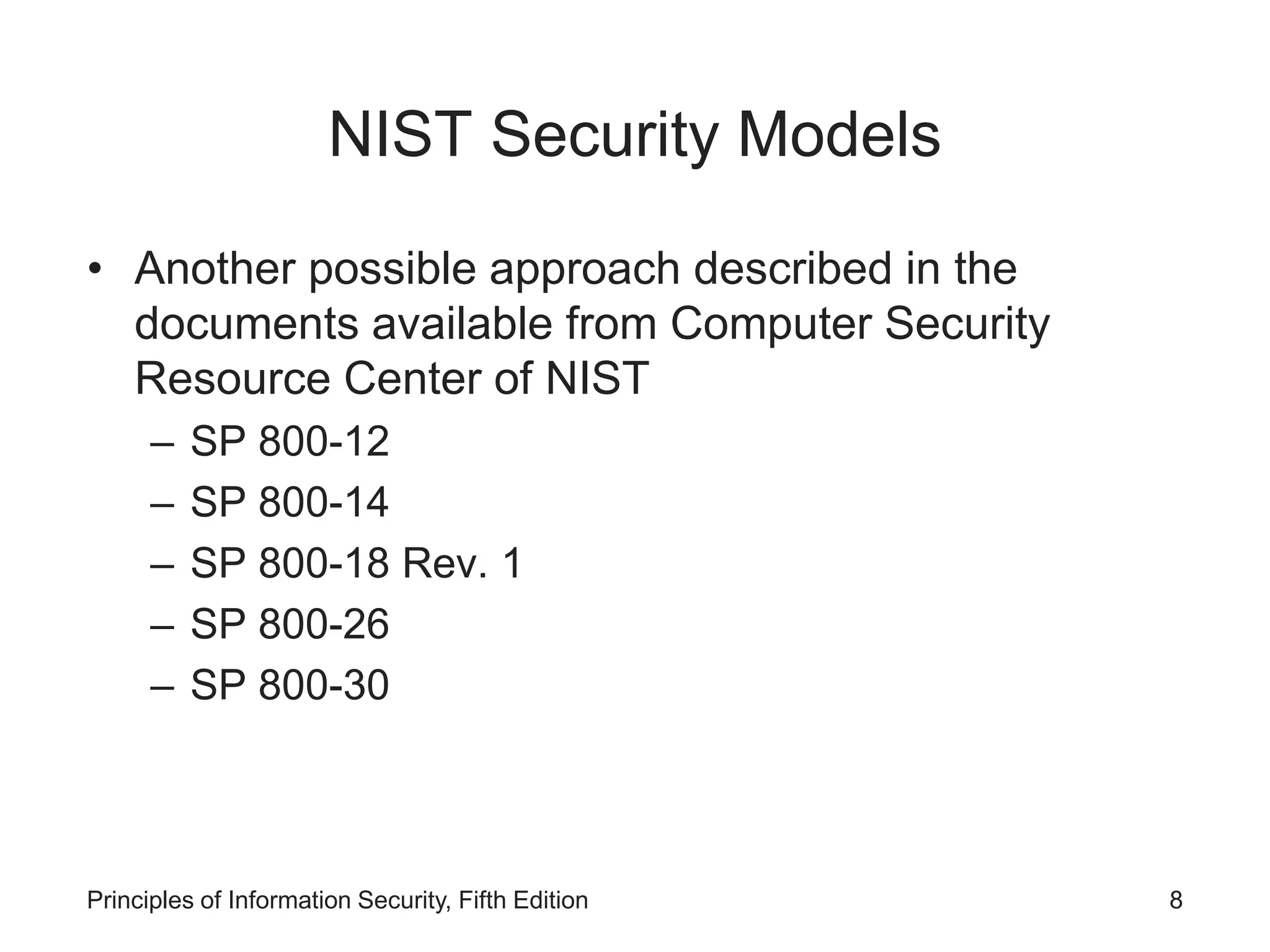




The document discusses systems-specific policies (SysSPs) which provide guidance and technical specifications for configuring and maintaining systems. SysSPs fall into managerial guidance or technical specifications categories. Access control lists and configuration rule policies are examples of technical specifications. Effective policy management requires a responsible manager, regular reviews, and an issuance process. Security frameworks like the Information Security Blueprint, ISO 27000, and NIST publications provide guidance for developing comprehensive organizational security policies and programs.











