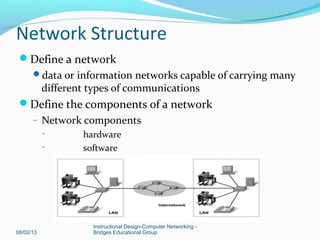
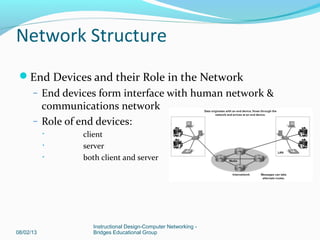
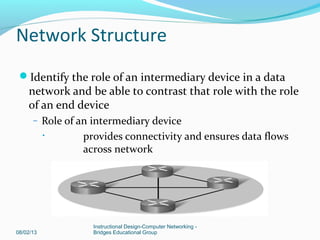
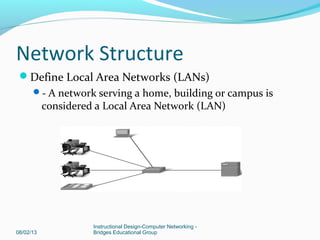
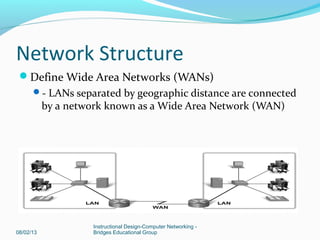
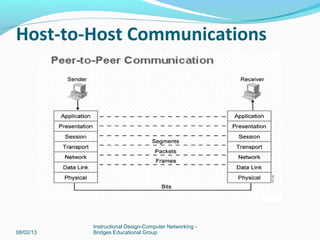
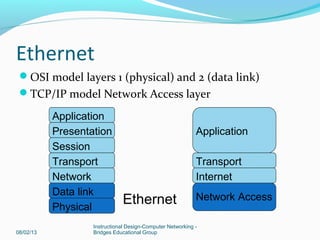
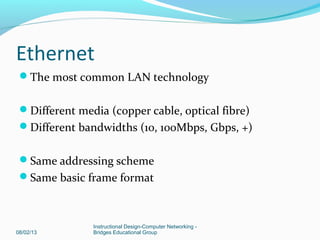
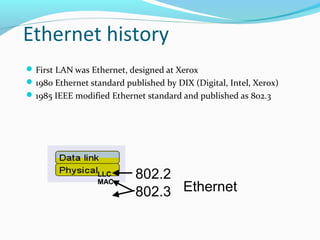
This document provides instructions on building a simple computer network. It describes how networking works from host-to-host communication using the OSI model. It defines the components of a network including hardware, software, end devices, and intermediary devices. It also discusses network structures such as local area networks (LANs) and wide area networks (WANs), Ethernet standards, and the roles of hubs and switches. The document concludes with an overview of the Cisco Internetwork Operating System used to configure and manage Cisco networking devices.











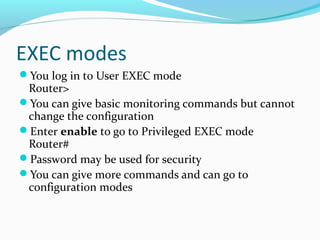
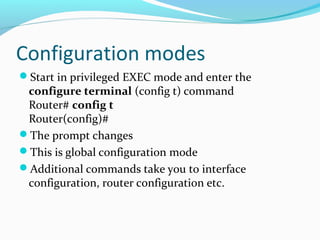



![Back up to TFTP server
Start TFTP server software on host
Paris#copy running-config tftp
Remote host []? 172.16.1.1
Name of configuration file to write [Paris-config]?
Paris12Oct07
Write file Paris12Oct07 to 172.16.1.1? [confirm] y
Writing Paris12Oct07 ! ! ! ! ! ! [OK]](https://image.slidesharecdn.com/lesson1slideshow-130802082521-phpapp02/85/Lesson-1-slideshow-31-320.jpg)