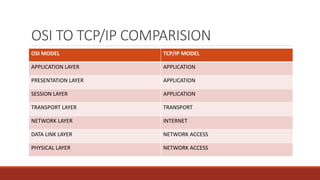
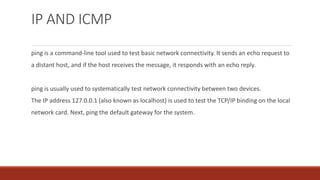
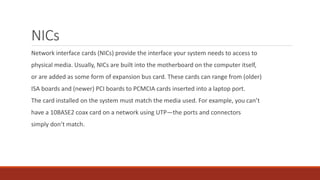
The document provides an overview of networking concepts including:
1) A network consists of devices that exchange data over media, with hosts having logical addresses. Common host types include workstations, servers, and routers.
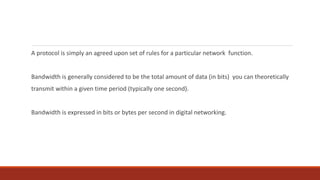
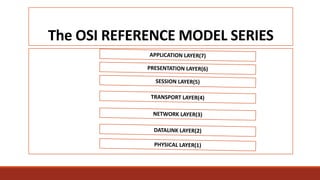
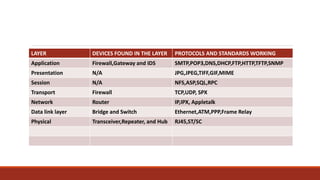
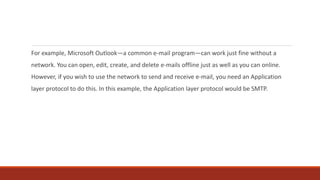
2) Protocols establish rules for network functions, while bandwidth refers to the amount of data that can be transmitted in a given time period.
3) Network topologies determine how devices are physically connected, with common types being bus, star, and ring configurations.
4) Networks are generally local area networks (LANs) or wide area networks (WANs) connecting multiple LANs across a wide geographic region.