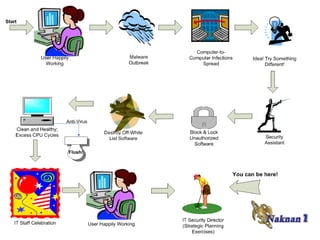
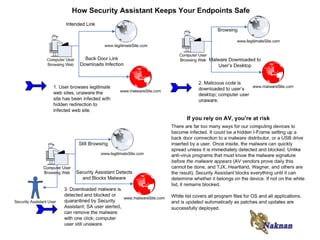
Please contact Noklek Finley or Doug Finley to discuss Naknan's endpoint security solutions. Naknan offers integrated whitelisting, patch management, and other controls to prevent malware execution and enforce compliance. Their solutions audit endpoints, update whitelists automatically during patching, and provide command/control of individual systems. Naknan differentiates itself through automated whitelist maintenance and its ability to schedule commands remotely.










![Critical Infrastructure
FERC Critical Infrastructure Protection Requirements -- CIP-007-2
R3. Security Patch Management — establish, document and implement a security patch
management program for tracking, evaluating, testing, and installing applicable cyber
security software patches for all Cyber
Assets within the Electronic Security Perimeter(s).
R3.1. document the assessment of security patches and security upgrades
R3.2. document the implementation of security patches.
R4. Malicious Software Prevention — use anti-virus software and other malicious
software (“malware”) prevention [and removal] tools
R4.1. implement anti-virus and malware prevention tools.
R4.2. implement a process for the update of anti-virus and malware prevention
“signatures.”
Similar requirements in other CIP documents.](https://image.slidesharecdn.com/endpointsecurityshiftingparadigms5-12494239825947-phpapp01/85/Endpoint-Security-Shifting-Paradigms-5-13-320.jpg)





