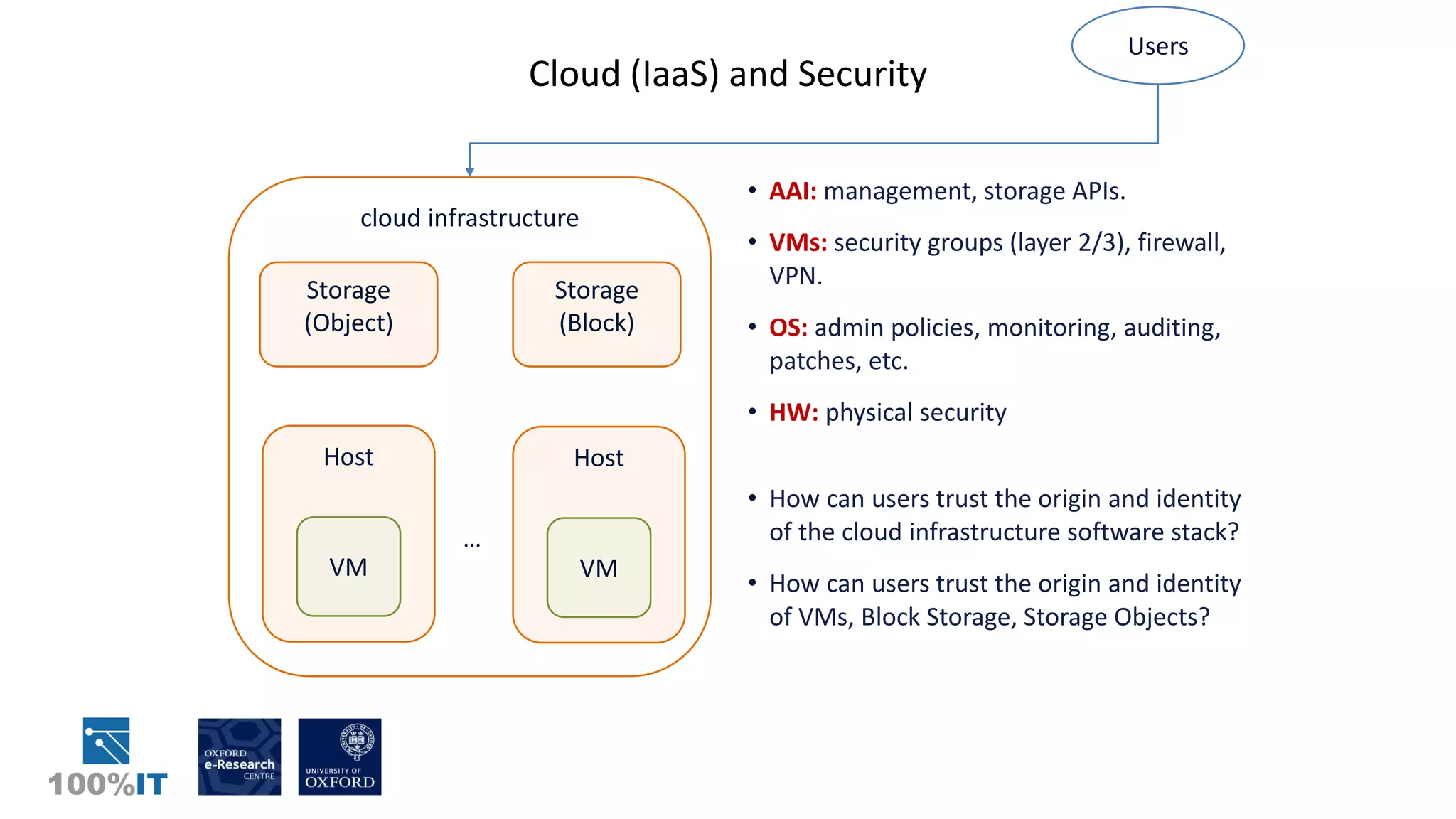
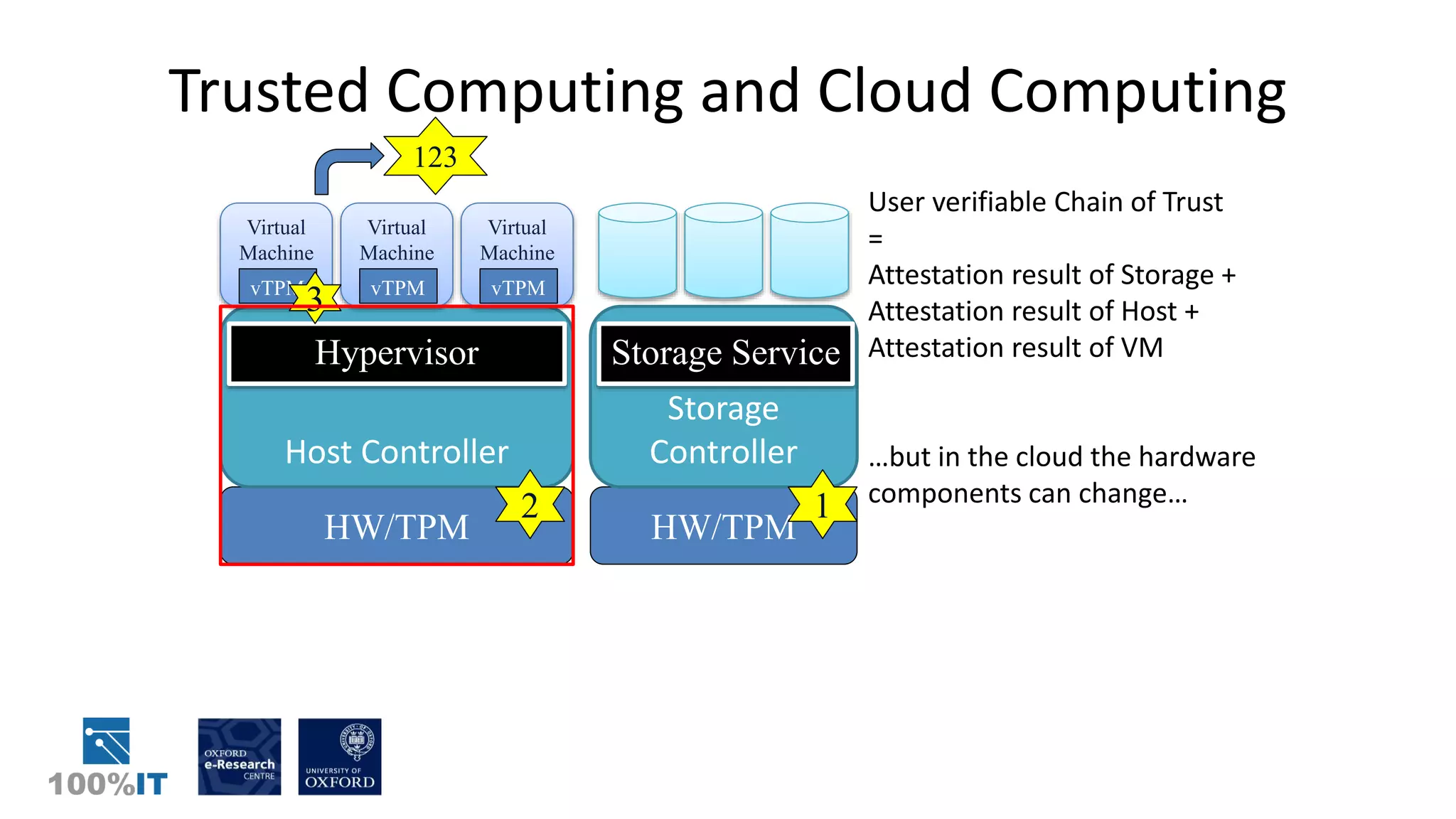
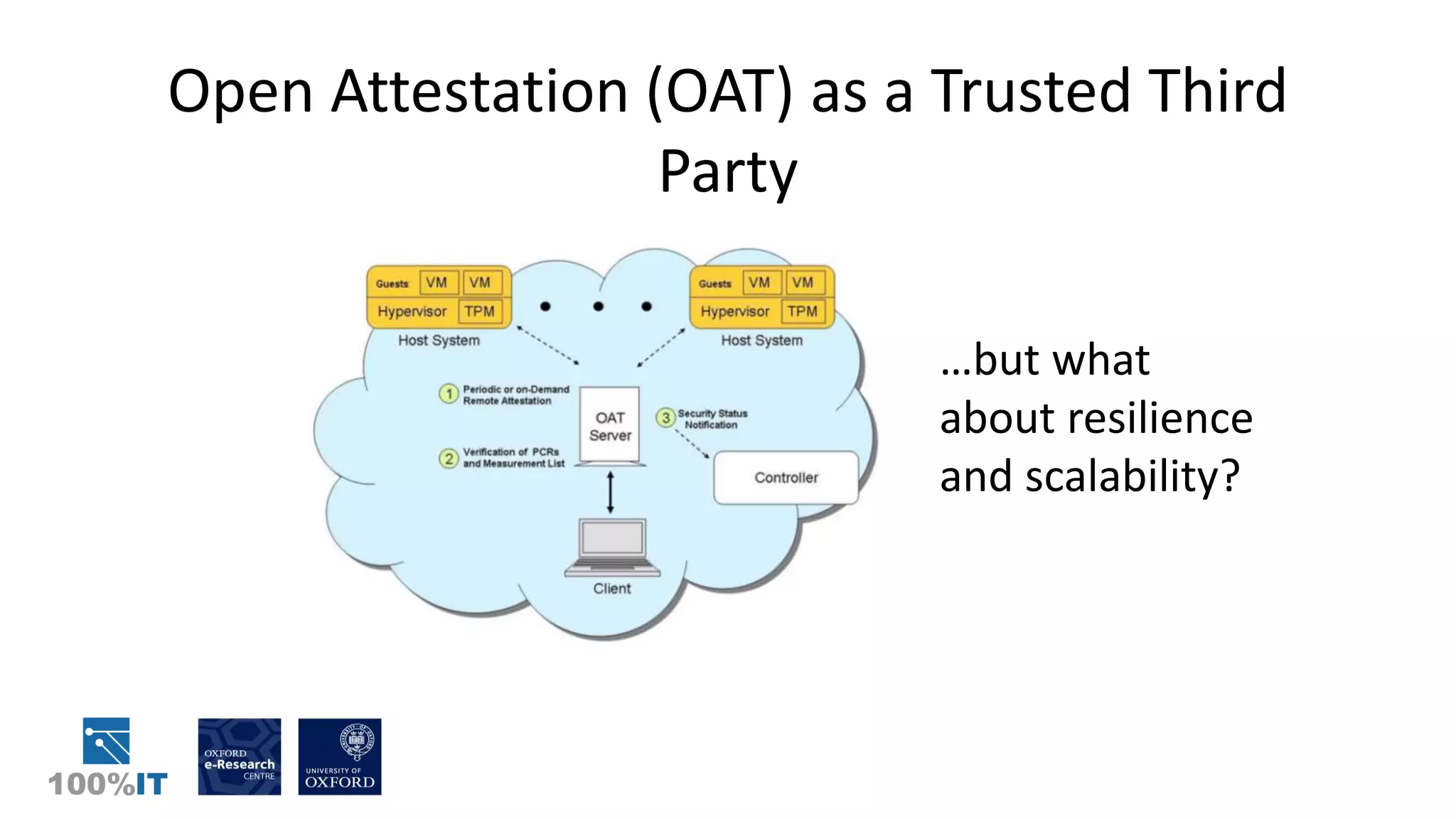
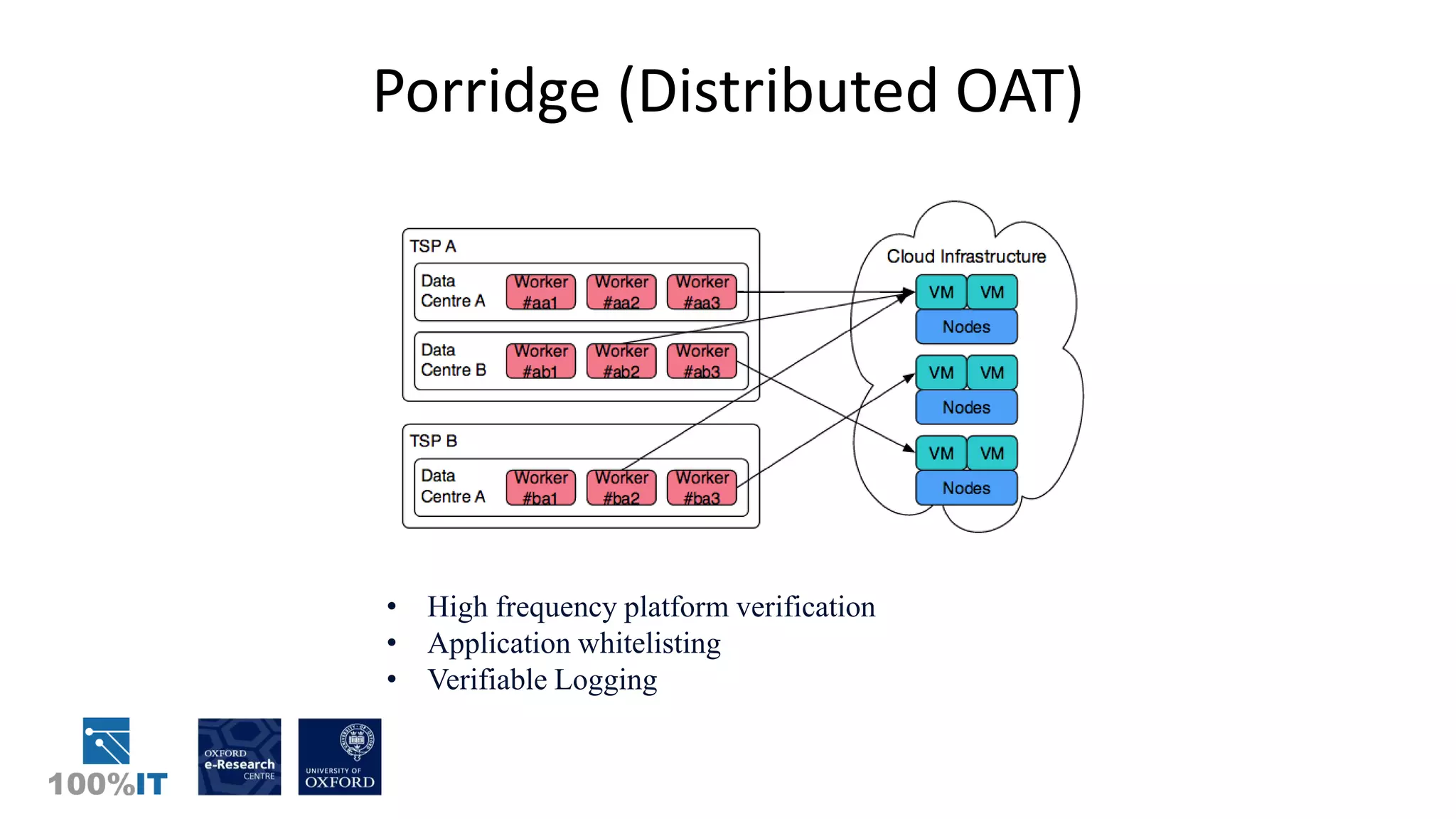
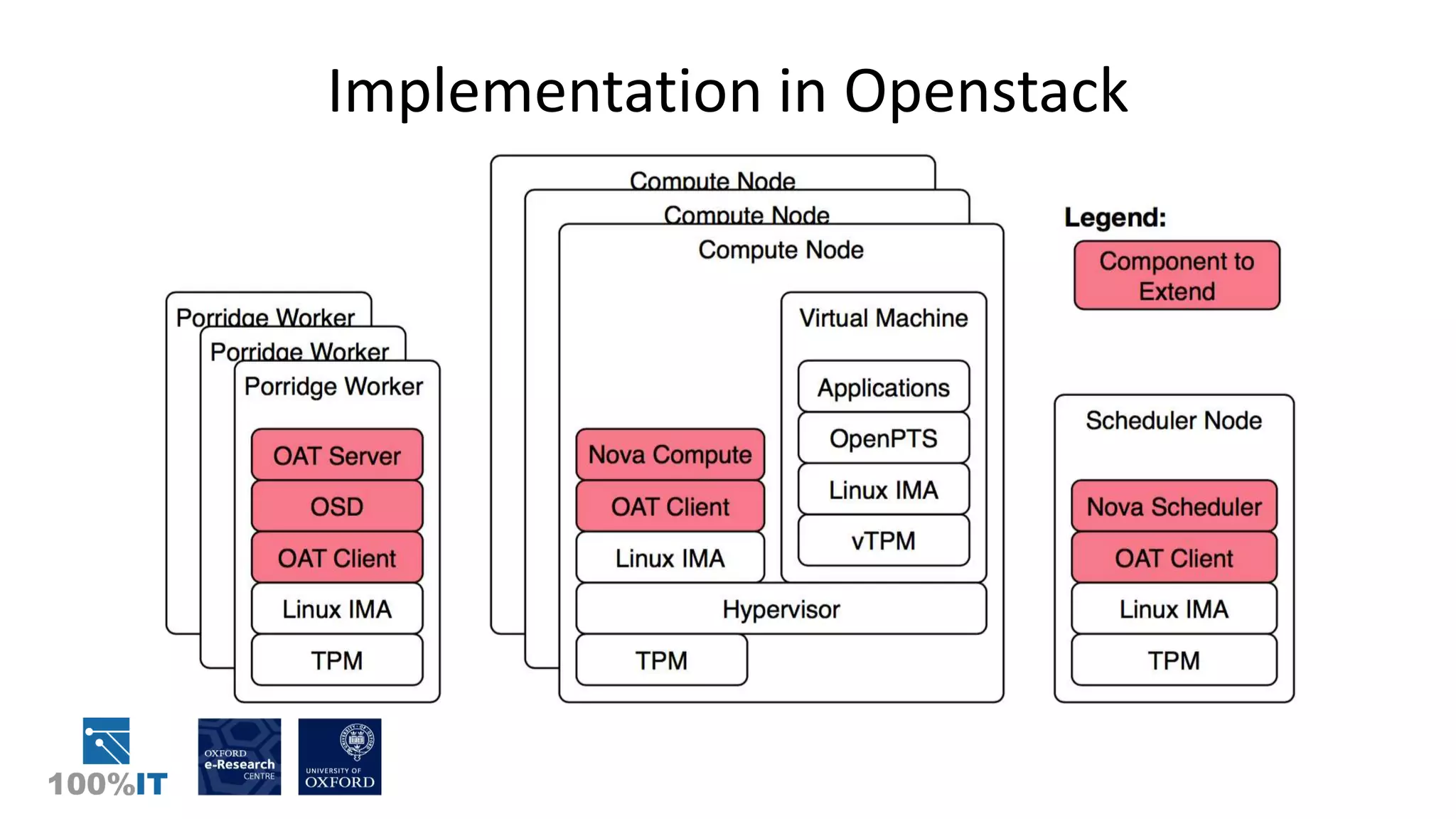
Trusted computing and remote attestation techniques can be used to build trust in cloud computing by creating a "chain of trust" from the hardware to the cloud services and user data. This allows a user to verify the configuration of each component in the cloud and ensure only authorized applications and services can access sensitive data. The solution involves using trusted computing mechanisms like TPM chips to attest cloud hosts, VMs, and services. It also allows application and data whitelisting based on these remote attestations to build trust without requiring users to unconditionally trust their cloud provider.