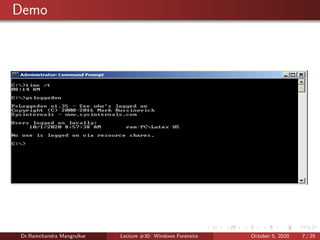
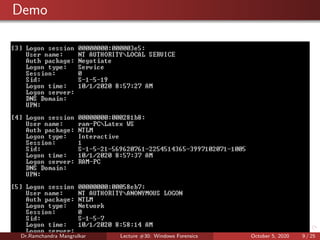
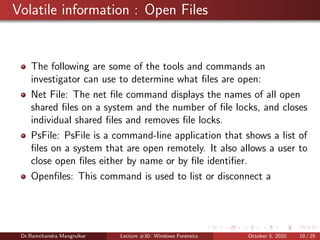
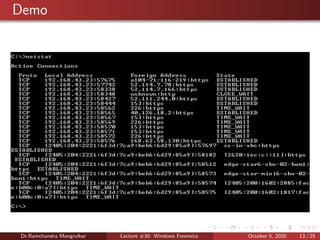
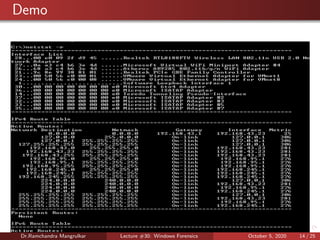
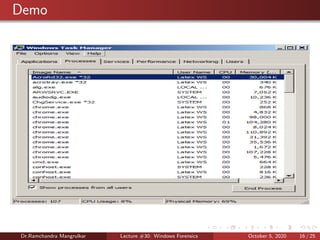
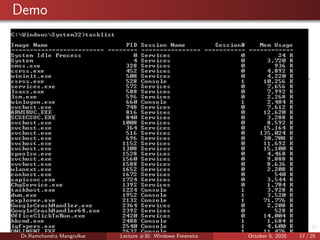
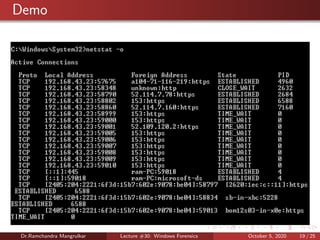
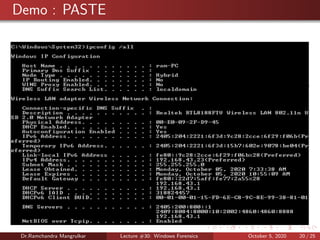
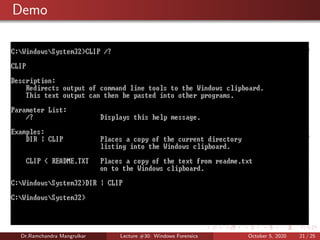
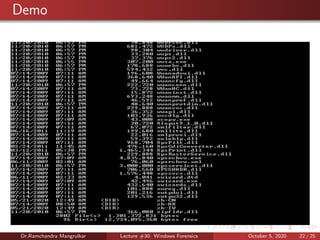
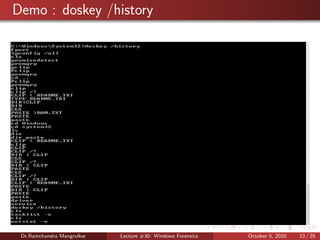
The document summarizes a lecture on Windows forensics. It discusses three major components of proper forensic analysis: understanding FAT and NTFS file systems, understanding Windows artifacts, and using proper forensic software. It also outlines objectives like collecting volatile/nonvolatile data and analyzing memory, registry, and files. Specific volatile data is explored, like system time, users, open files, network information, processes, and the clipboard. Methods for obtaining this data, like commands and software, are demonstrated. Nonvolatile data storage is also discussed.