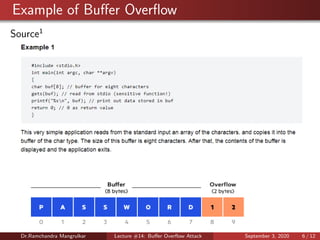
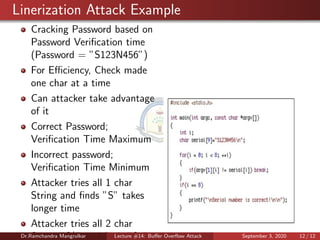
The document discusses buffer overflow attacks, which occur when a program writes more data to a buffer than it is allocated to hold. This can overwrite other memory locations and potentially allow attackers to execute malicious code. The lecture covers how buffer overflows work, examples of overflow errors, programming languages that are more vulnerable, and techniques for preventing overflows like address space randomization and data execution prevention.