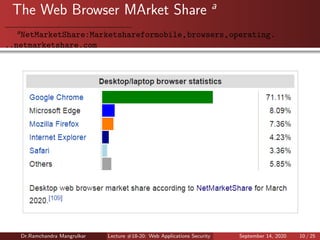
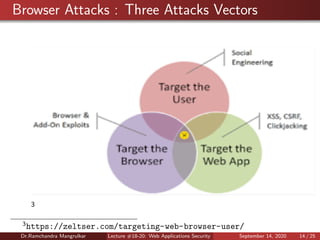
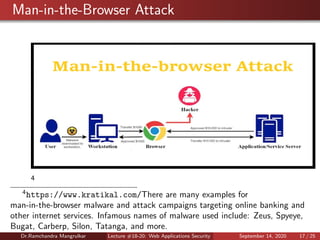
This document summarizes a lecture on web application security. It discusses the architecture of web browsers and potential vulnerabilities, including man-in-the-browser attacks, keystroke loggers, and page substitution attacks. It also covers common vulnerabilities in web applications like injection flaws, broken authentication, sensitive data exposure, and incorrect access control settings. The goal is to educate about key security risks to web browsers and applications.