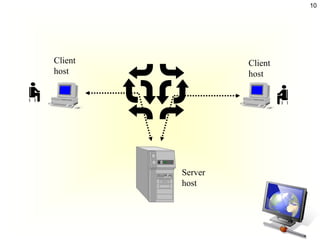
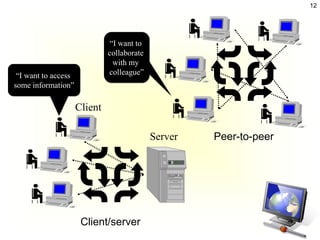
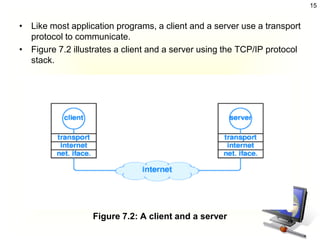
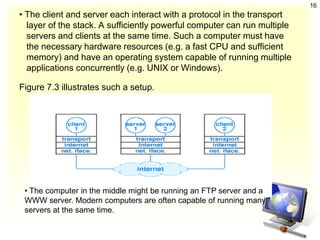
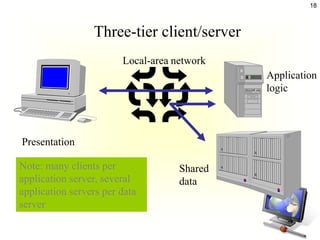
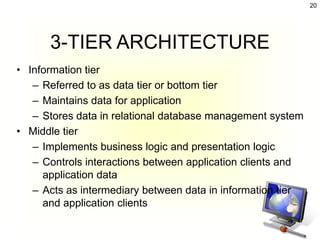
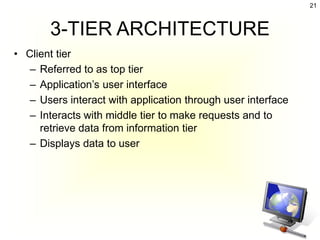
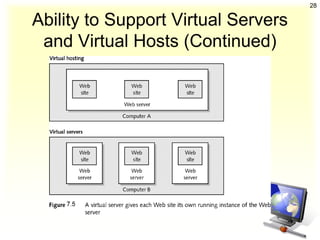
The document discusses client-server architecture and interactions. It defines client-server as a network architecture that separates clients, often applications with a GUI, from servers. Clients can send requests to servers. Common server types include application, file, terminal, and mail servers. The document also discusses properties of clients and servers, browser extensions like plugins and helper applications, client-server sessions, multitier architectures, and common server applications.