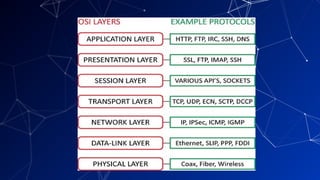
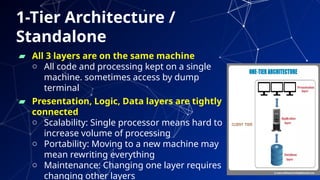
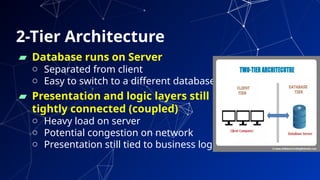
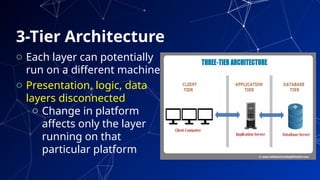
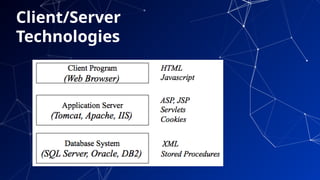
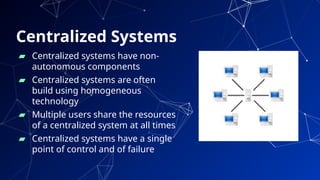
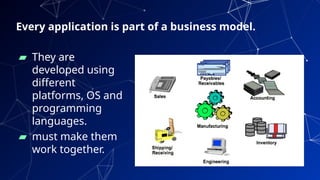
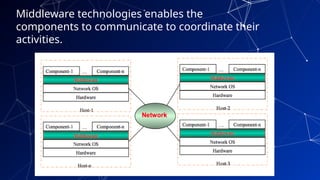
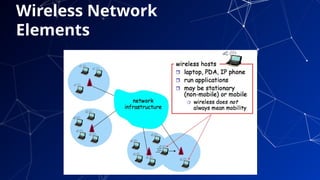
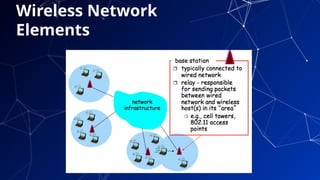
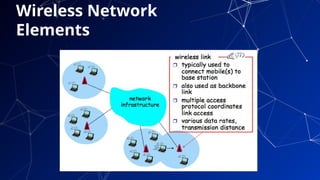
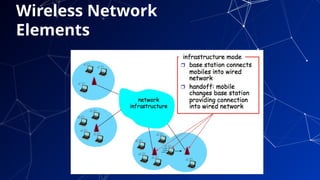
The document provides an introduction to netcentric computing, covering its history, architecture, client/server paradigms, distributed computing, mobile and wireless computing, and network security. It discusses the foundational elements of networking, including types of networks, protocols, and the role of the internet, as well as the evolution and challenges of mobile computing and ensuring network security. Additionally, it touches on multimedia systems and their technical requirements for content transmission and management.



![Netcentric Principle
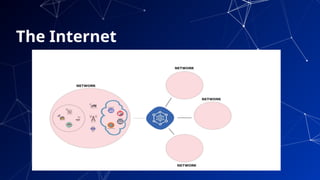
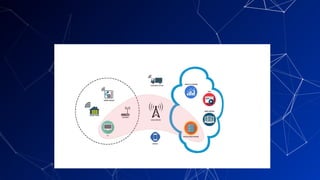
▰ Net-Centric Computing (NCC) principle is based
on a distributed environment where multiple
components, possibly across geographical
boundaries, that communicate and coordinate
their actions through message passing. [2]
▰ To an actor outside this system, it appears as if a
single coherent system.
▰ Example : The Internet
4](https://image.slidesharecdn.com/itt501-chapter1-250119062154-bfc0be6f/85/ITT501-Chapter-1-pptx-netcentric-fundamentals-4-320.jpg)