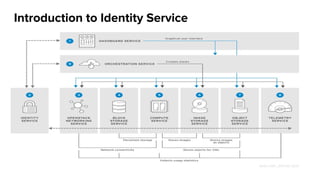
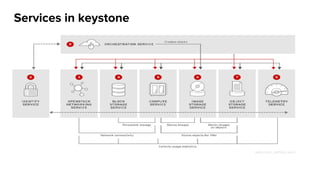
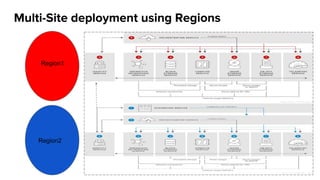
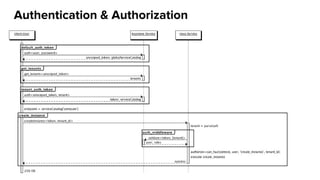
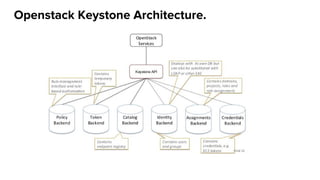
The document summarizes an OpenStack Keystone meetup presentation on identity services. It introduces key concepts of Keystone like actors, credentials, tokens, roles, projects and domains. It covers the Keystone architecture and configuration file. Demos were presented on creating entities in DevStack and integrating Keystone with an IPA/LDAP backend. The presentation concludes with references and information on getting involved in the Keystone community.








![Configuration file (keystone.conf)
/etc/keystone/keystone.conf
● [DEFAULT] - General configuration
● [assignment] - Assignment system driver configuration
● [auth] - Authentication plugin configuration
● [cache] - Caching layer configuration
● [catalog] - Service catalog driver configuration
● [credential] - Credential system driver configuration
● [domain_config] - Domain configuration
● [endpoint_filter] - Endpoint filtering configuration
● [endpoint_policy] - Endpoint policy configuration
● [federation] - Federation driver configuration
● [fernet_tokens] - Fernet token configuration
● [identity] - Identity system driver configuration
● [identity_mapping] - Identity mapping system driver configuration
● [ldap] - LDAP configuration options](https://image.slidesharecdn.com/keystonedeepdive-1-170618053325/85/Keystone-deep-dive-1-14-320.jpg)
![Configuration file (keystone.conf)
/etc/keystone/keystone.conf
● [memcache] - Memcache configuration options
● [oauth1] - OAuth 1.0a system driver configuration
● [paste_deploy] - Pointer to the PasteDeploy configuration file
● [policy] - Policy system driver configuration for RBAC
● [resource] - Resource system driver configuration
● [revoke] - Revocation system driver configuration
● [role] - Role system driver configuration
● [saml] - SAML configuration options
● [security_compliance] - Security compliance configuration
● [shadow_users] - Shadow user configuration
● [signing] - Cryptographic signatures for PKI based tokens
● [token] - Token driver & token provider configuration
● [tokenless_auth] - Tokenless authentication configuration
● [trust] - Trust configuration](https://image.slidesharecdn.com/keystonedeepdive-1-170618053325/85/Keystone-deep-dive-1-15-320.jpg)



![LDAP Integration for Identity
● # setsebool -P authlogin_nsswitch_use_ldap on
● Configure keystone.conf for multiple backends:
● Define the destination LDAP server in the /etc/keystone/keystone.conf file:
[ldap]
url = ldaps://ipa.india-1.local
user = uid=svc-ldap,cn=users,cn=accounts,dc=india-1,dc=local
user_filter = (memberOf=cn=grp-openstack,cn=groups,cn=accounts,dc=india-1,dc=local)
password = <RedactedComplexPassword>
user_tree_dn = cn=users,cn=accounts,dc=india-1,dc=local
user_objectclass = inetUser
user_id_attribute = uid
user_name_attribute = uid
user_mail_attribute = mail
user_pass_attribute =
user_allow_create = False
user_allow_update = False
user_allow_delete = False
tls_cacertfile = /etc/ssl/certs/ca.crt
group_tree_dn = ou=Groups,dc=india-1,dc=local
group_objectclass = groupOfNames
[identity]
driver = keystone.identity.backends.ldap.Identity"
[identity]
domain_specific_drivers_enabled = True
domain_config_dir = /etc/keystone/domains
● Configure LDAP server in the /etc/keystone/domains/keystone.<domain>.conf](https://image.slidesharecdn.com/keystonedeepdive-1-170618053325/85/Keystone-deep-dive-1-19-320.jpg)