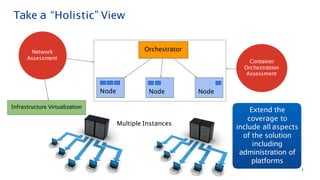
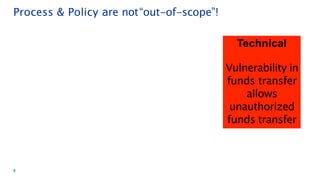
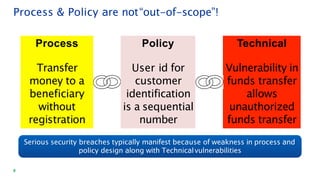
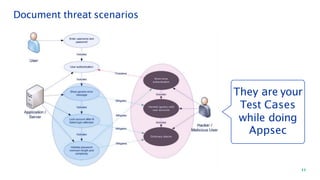
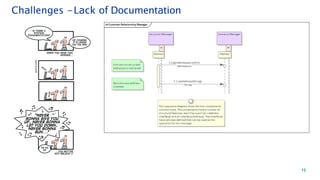
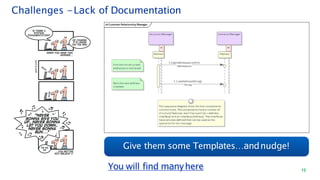
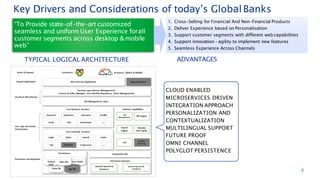
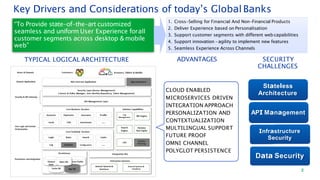
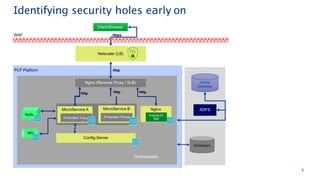
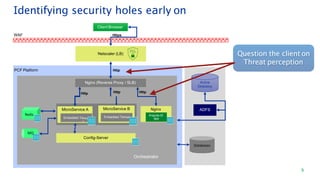
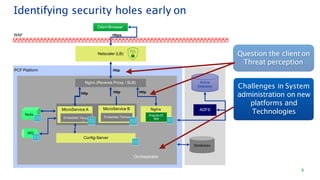
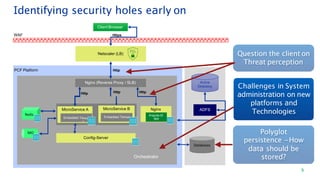
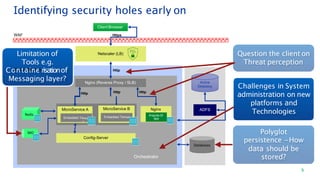
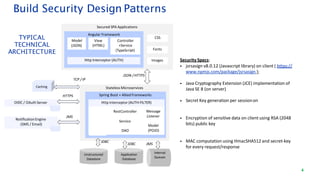
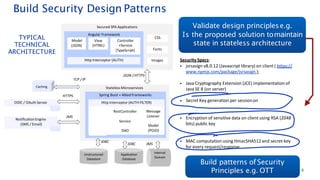
The document discusses security architecture consulting, focusing on cross-selling, personalization, innovation support, and seamless user experiences across various digital platforms. It highlights the importance of addressing security vulnerabilities in system administration and emphasizes the need for robust authentication, authorization, and encryption protocols to safeguard sensitive data. Additionally, it outlines the steps for a thorough security review, including user access management, cryptography management, and application deployment processes to ensure comprehensive security measures are in place.





![The Devil is in the Detail!
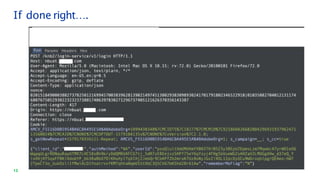
5
this.clientSessionId = this.generateRandom();
function generateRandom() {
var asciiArray = new Uint32Array([0xFAFBA, 0xAFFBC, 0xFABBD,
0xFFFBA, 0xFAFFE, 0xFADBA, 0xFEFBB, 0xFAFBD]);
window.crypto.getRandomValues(asciiArray);
return this.padZero(asciiArray);
}
function padZero(randomNumberArray) {
return '0' + randomNumberArray[0] +
'0' + randomNumberArray[1] +
'0' + randomNumberArray[2] +
'0' + randomNumberArray[3] +
'0' + randomNumberArray[4] +
'0' + randomNumberArray[5] +
'0' + randomNumberArray[6] +
'0' + randomNumberArray[7];
}
New “nonce” header value sent on every Request and validated
against Response header value. Also acts as correlation-id to trace &
correlate user requests in logs across backend services.
Format: (16-digit random per session | 16-digit random per request)
var requestId = this.generateRandom();
RequestHeaders[‘nonce’] = this.clientSessionId + '|' + requestId;
“state” is unique server session id. Created for tracking conversation of Multi-Factor Login
Flow with max. idle/inactivity timeout of short duration (e.g. 5 mins).
Format: Base64.getUrlEncoder().withoutPadding().encode(
User-Agent | client_id | clientSessionId | UID | UUID.randomUUID().toString() )
LogonUI
(AngularClient)
Authentication
Service
End-User
1. InputUserId
[nonce]{state,authMethod}
CacheServer
(Redis)
POST/v1/idp/login
[nonce]{client_id, userId}
HTTP
Server
https://www.kotak.com/Signin/
generateNonce()
//Look-upUserIdand
CRN,
generateState()
validateNonce()
put(state,HashMap)
Display Fields
Relevant for
authMethod
//BustFrames
Reverse Proxy should add standard Security Headers to ALL Responses:
Strict-Transport-Security: max-age=599
X-Content-Type-Options: nosniff
X-Frame-Options: DENY
X-XSS-Protection: 1; mode=block
Access-Control-Allow-Origin: https://www.abcbank.com
FindUID authMethod](https://image.slidesharecdn.com/securityarchitectureconsulting-200201190106/85/Security-Architecture-Consulting-Hiren-Shah-16-320.jpg)