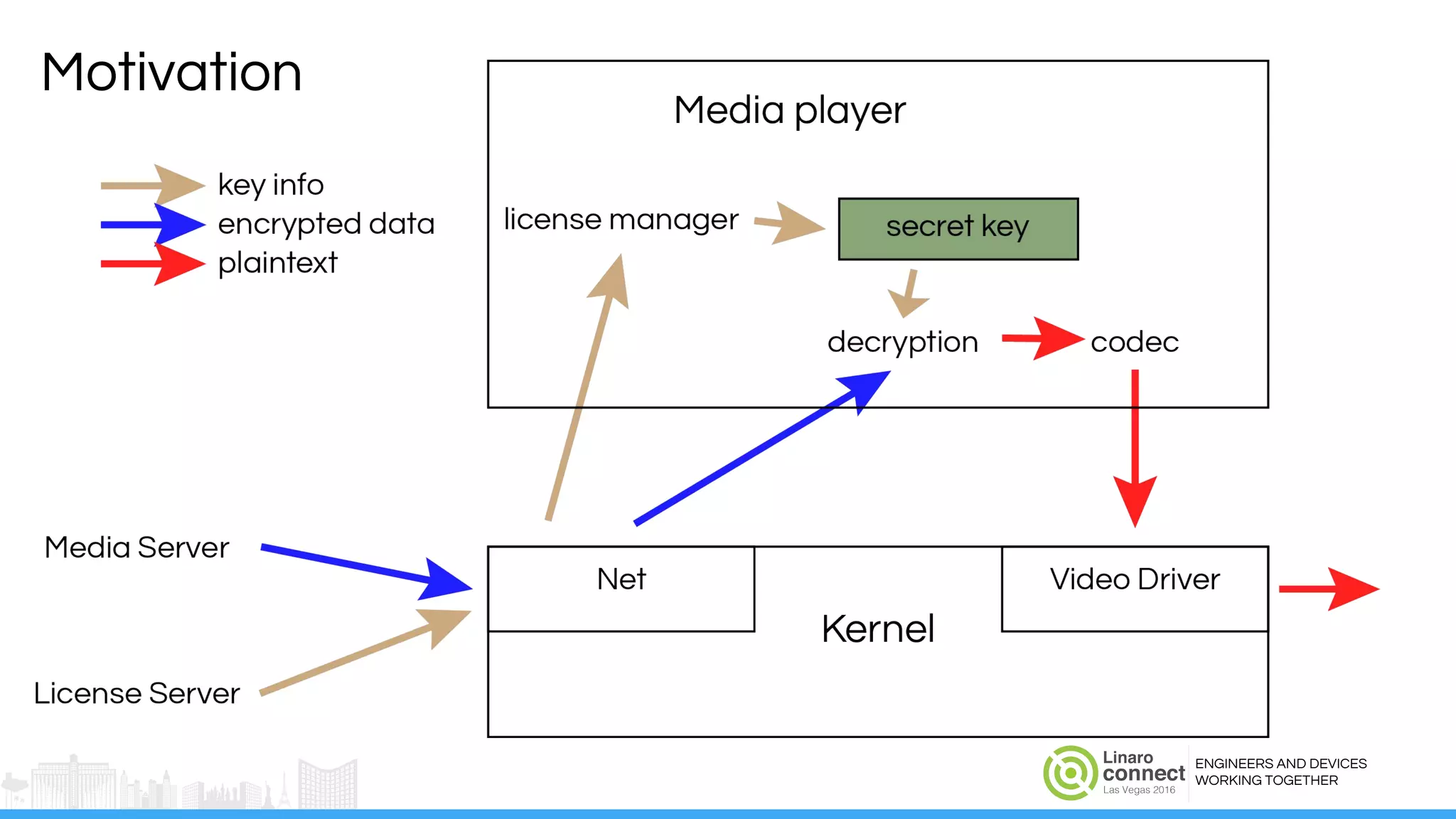
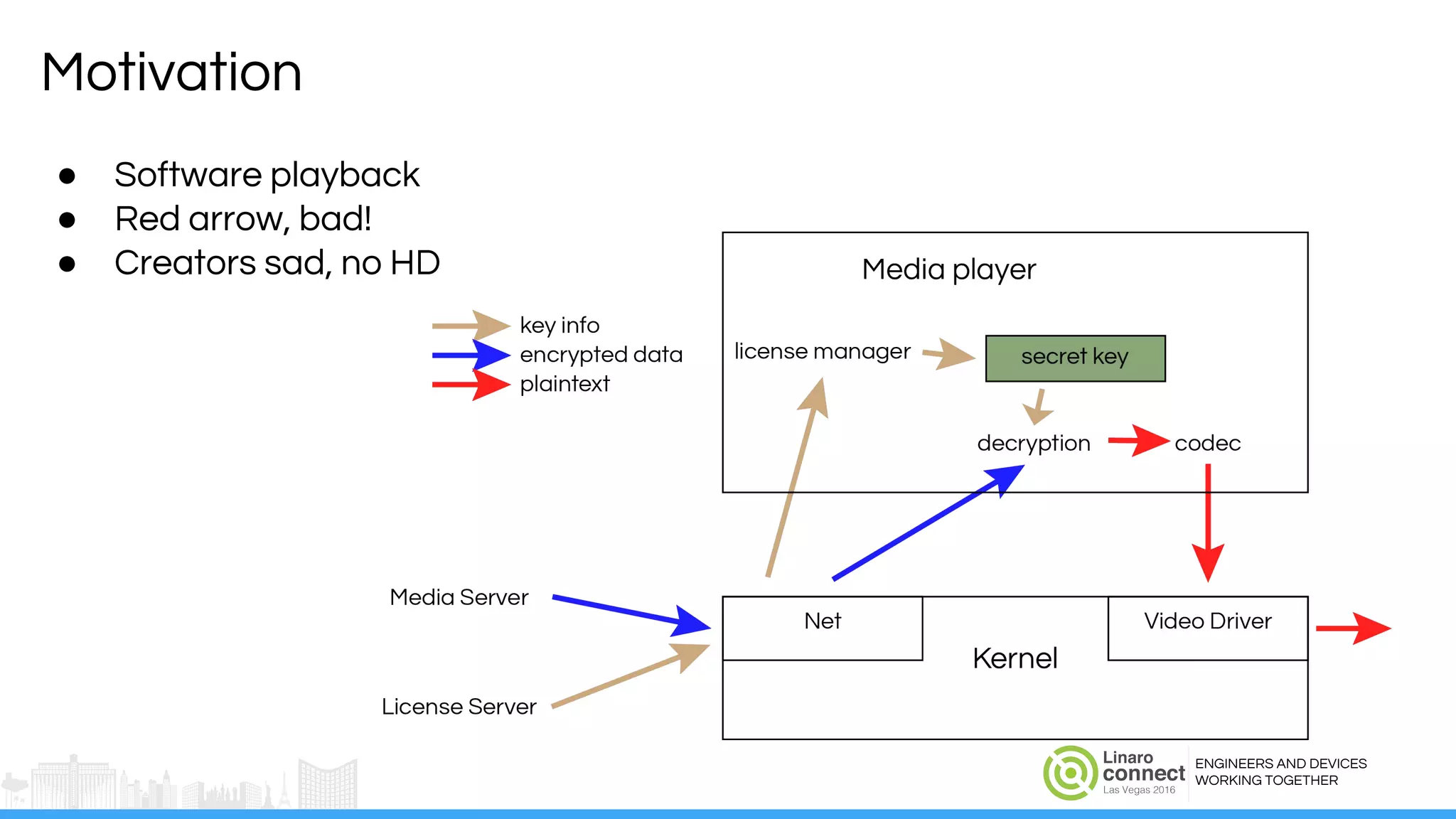
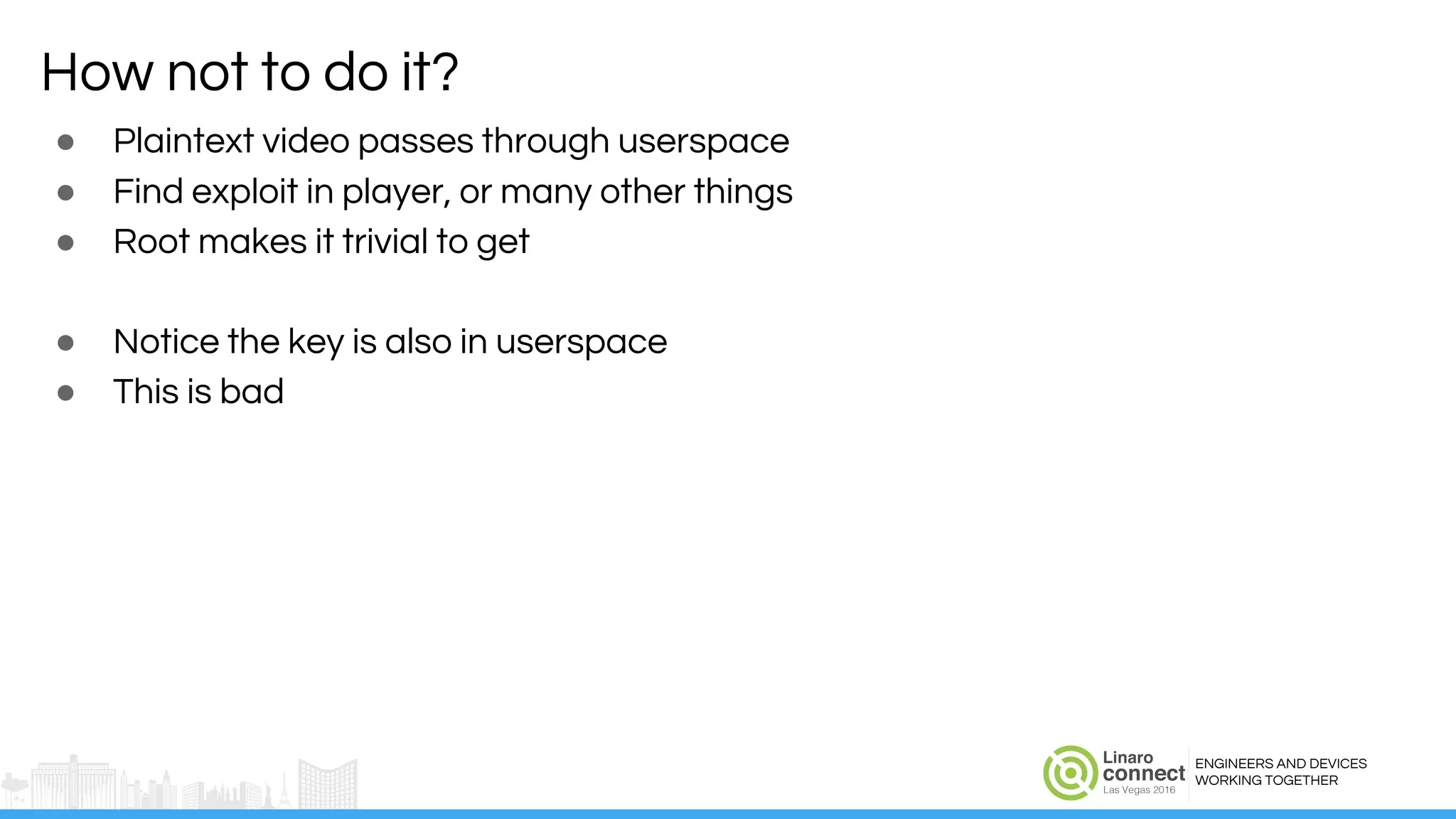
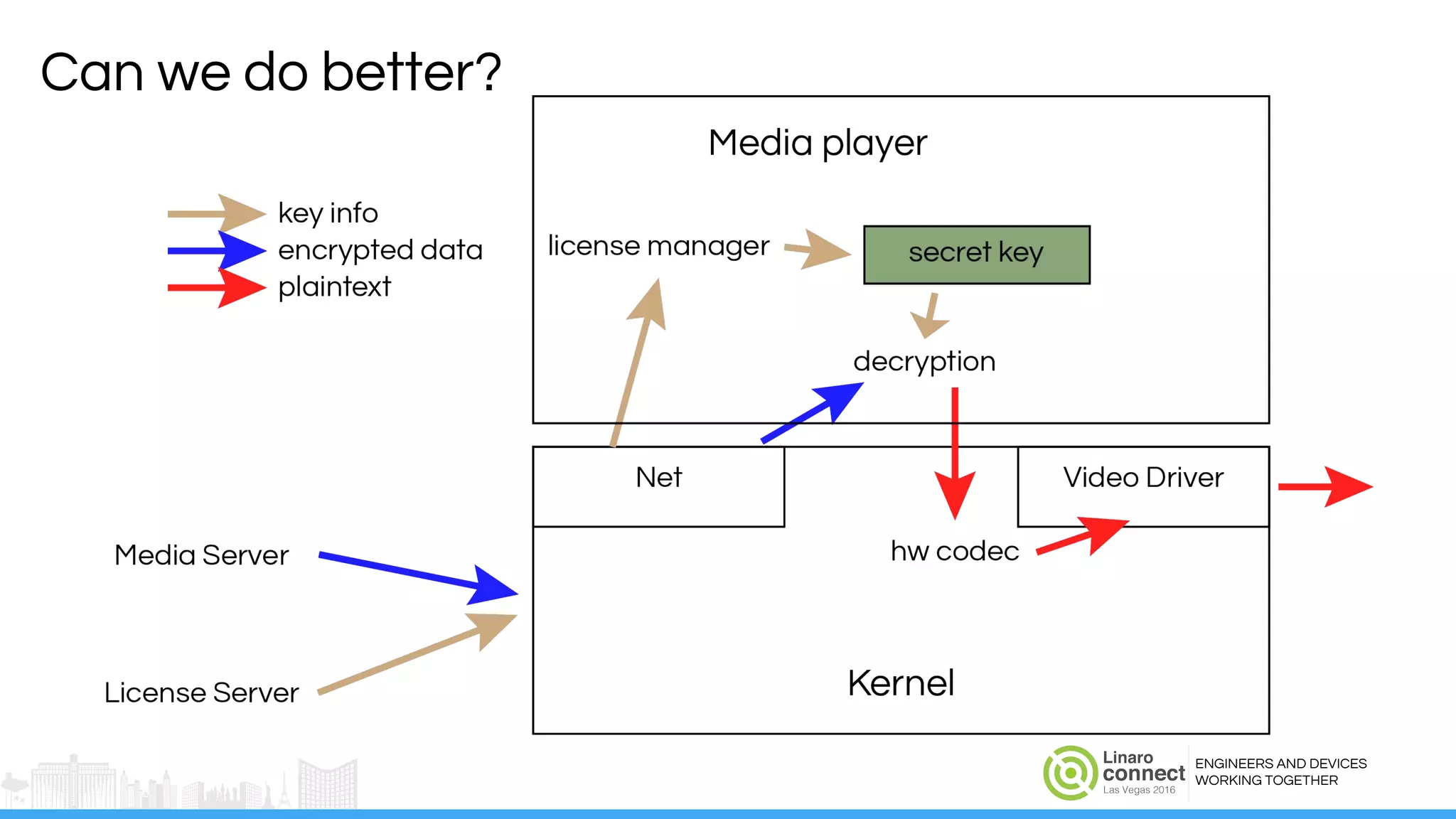
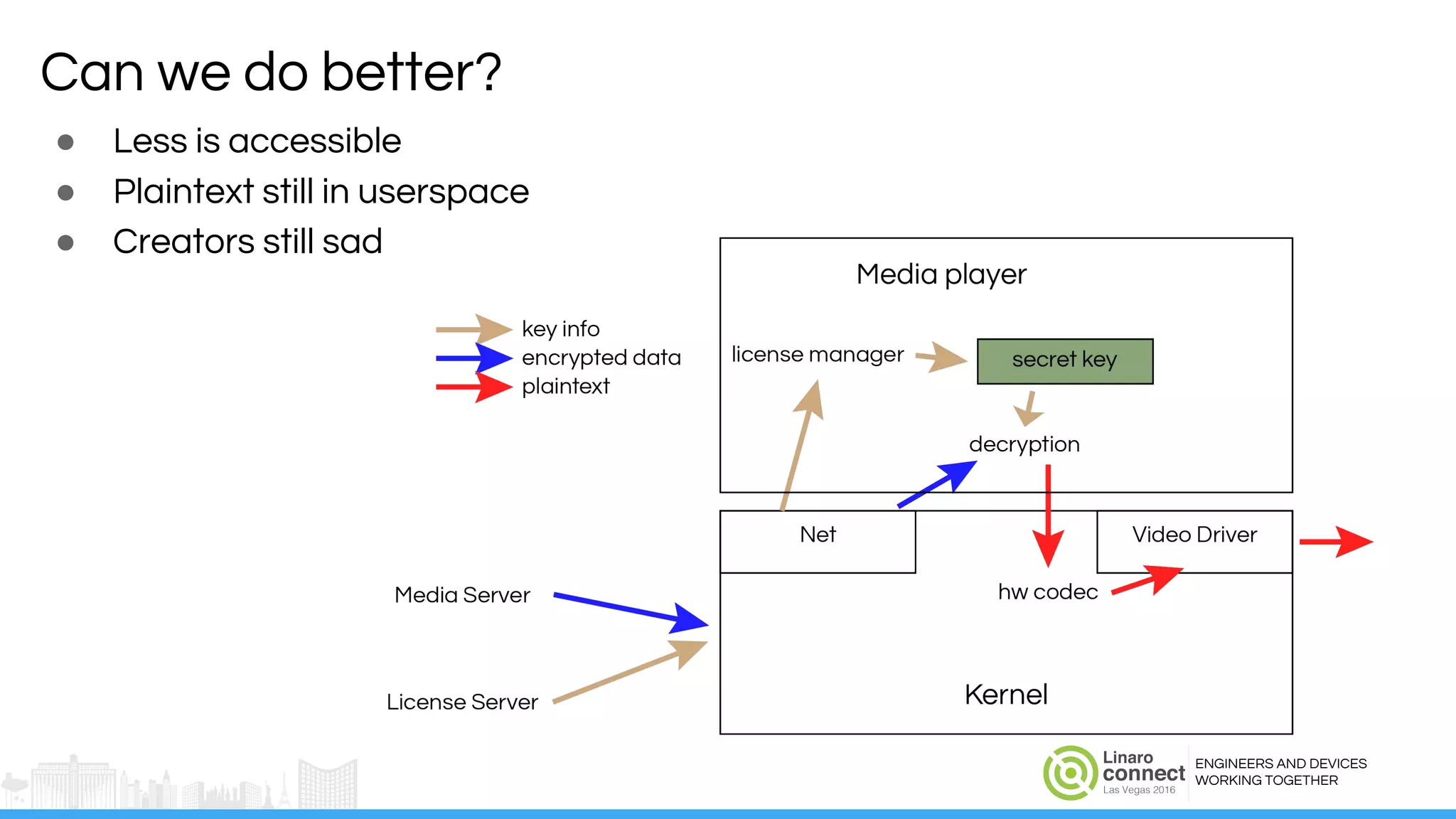
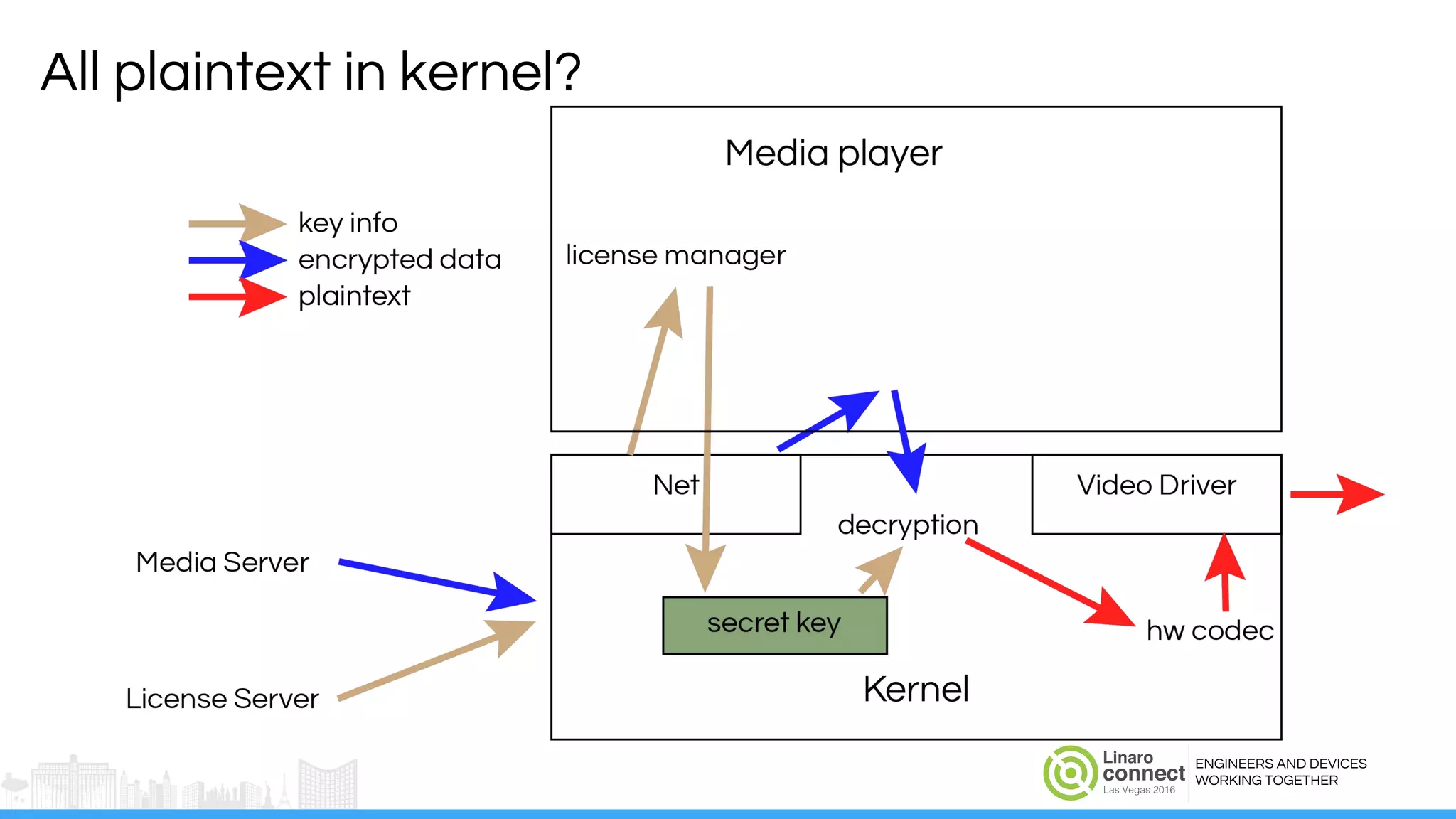
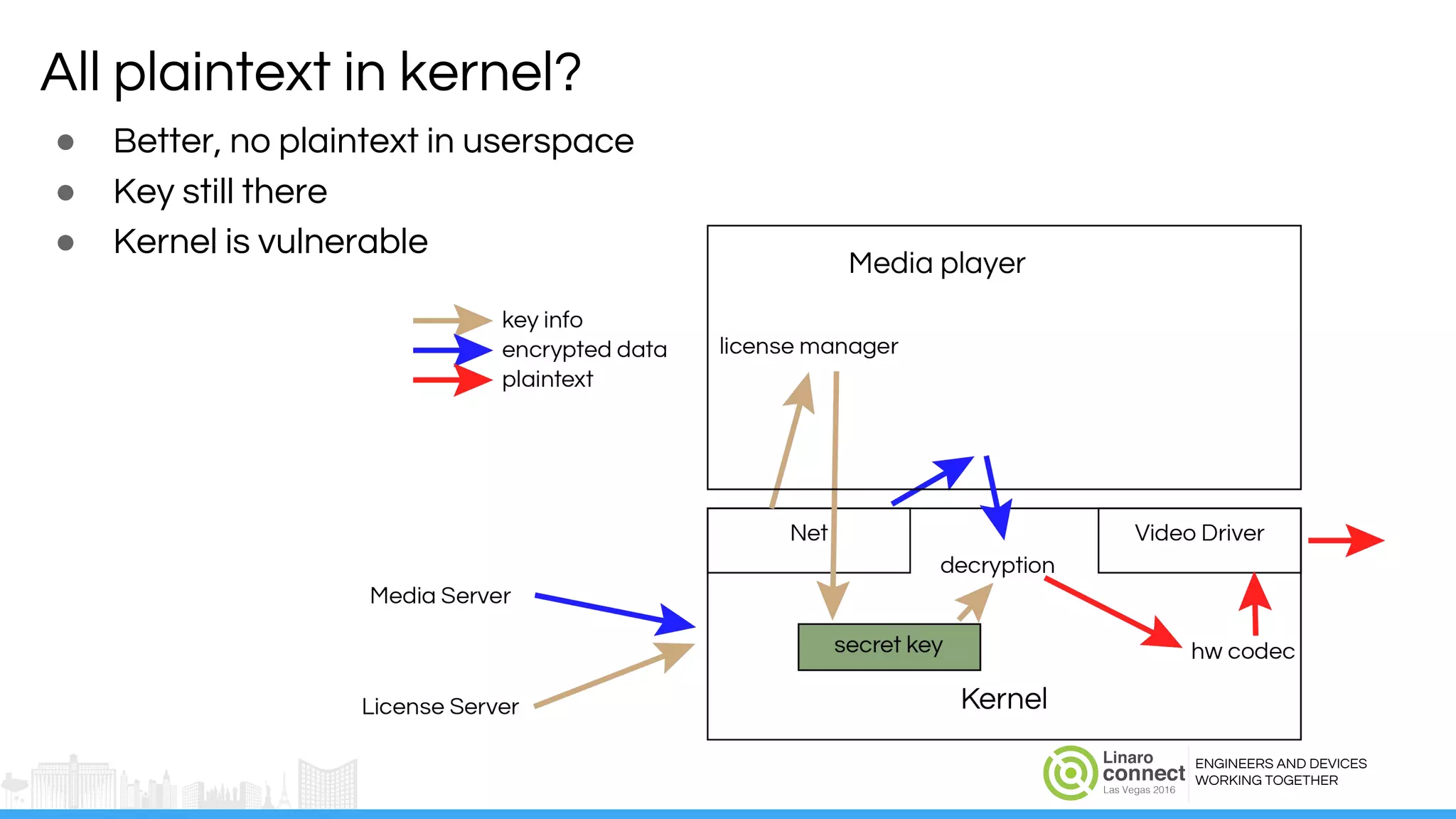
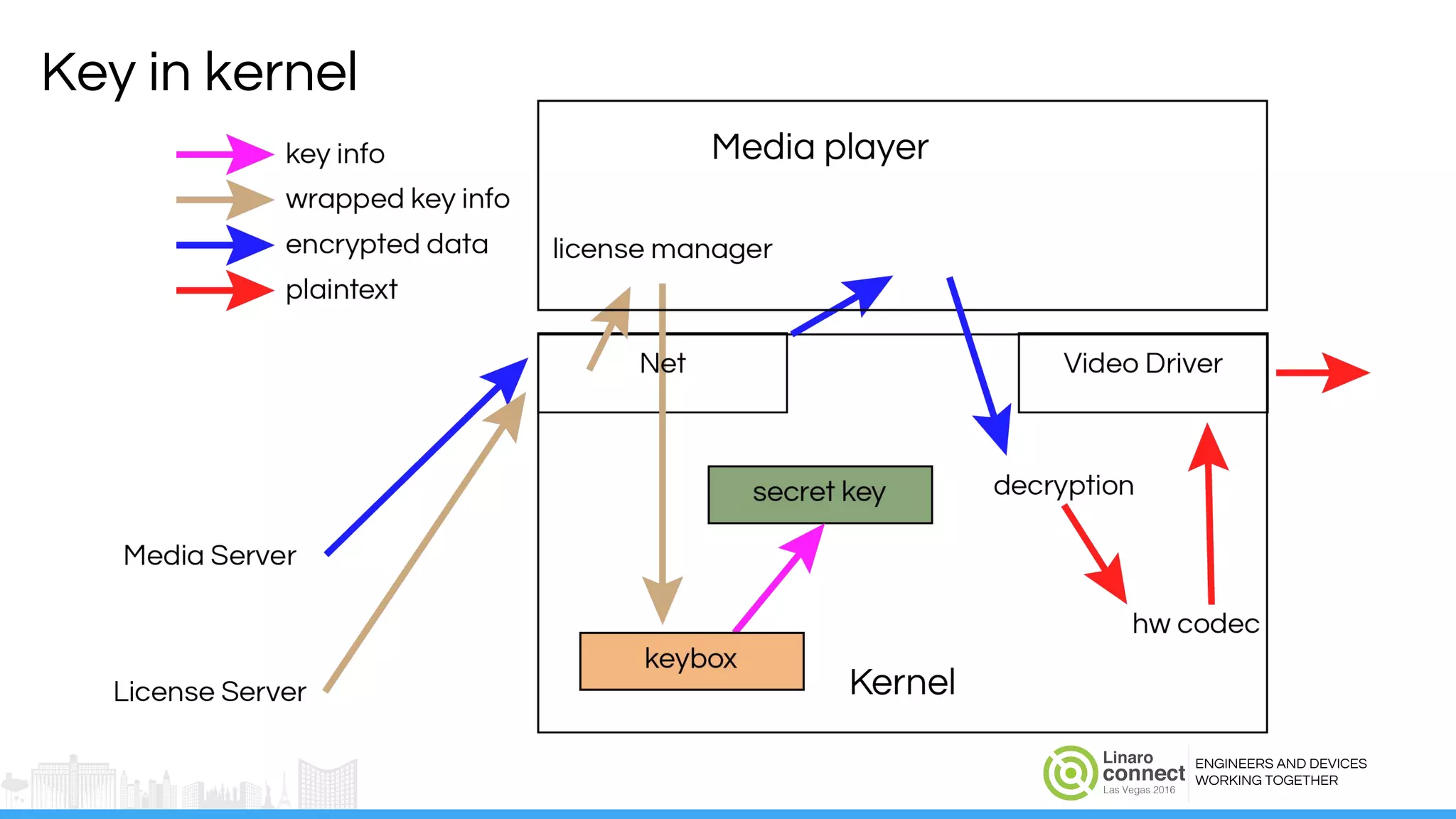
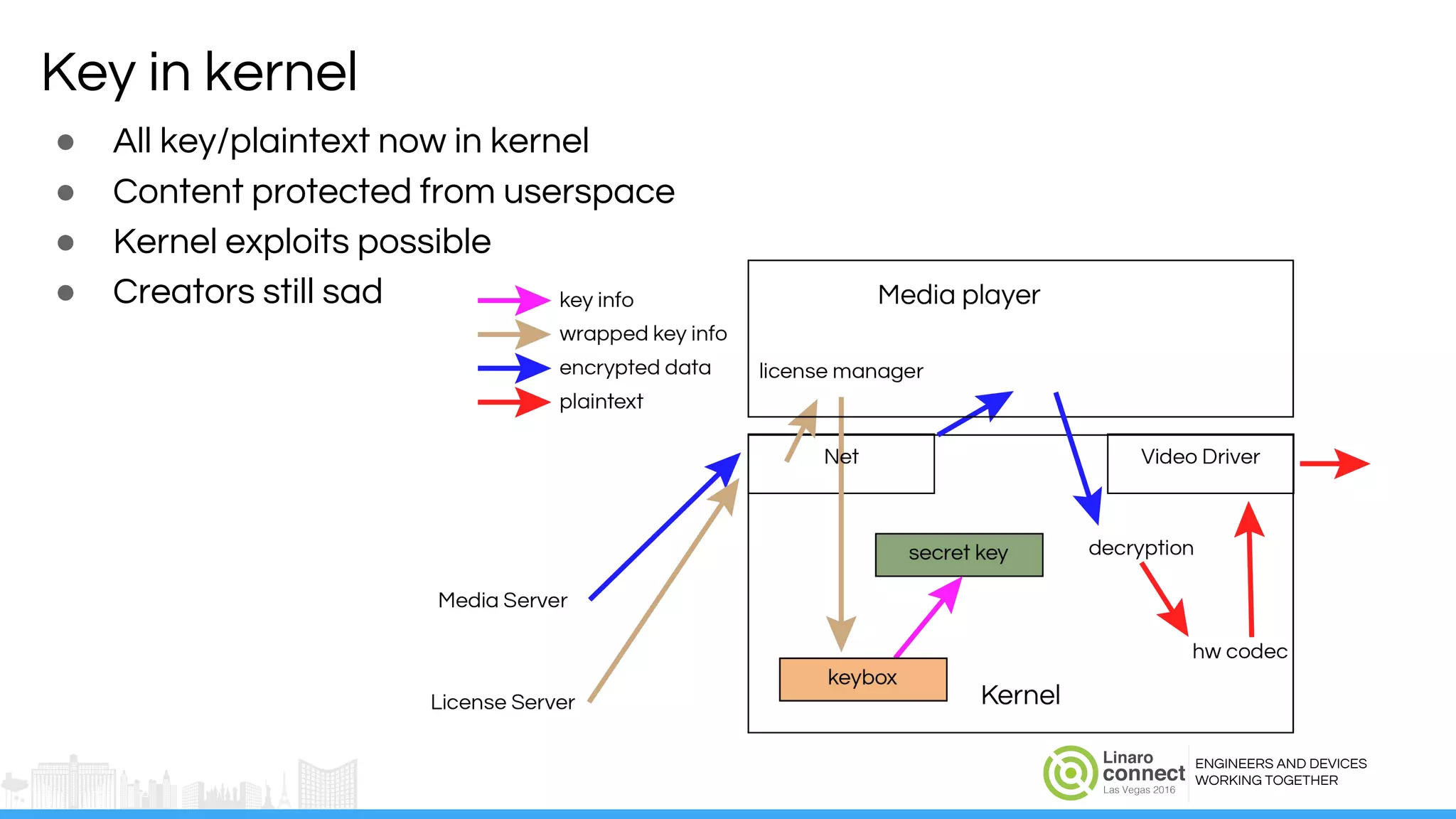
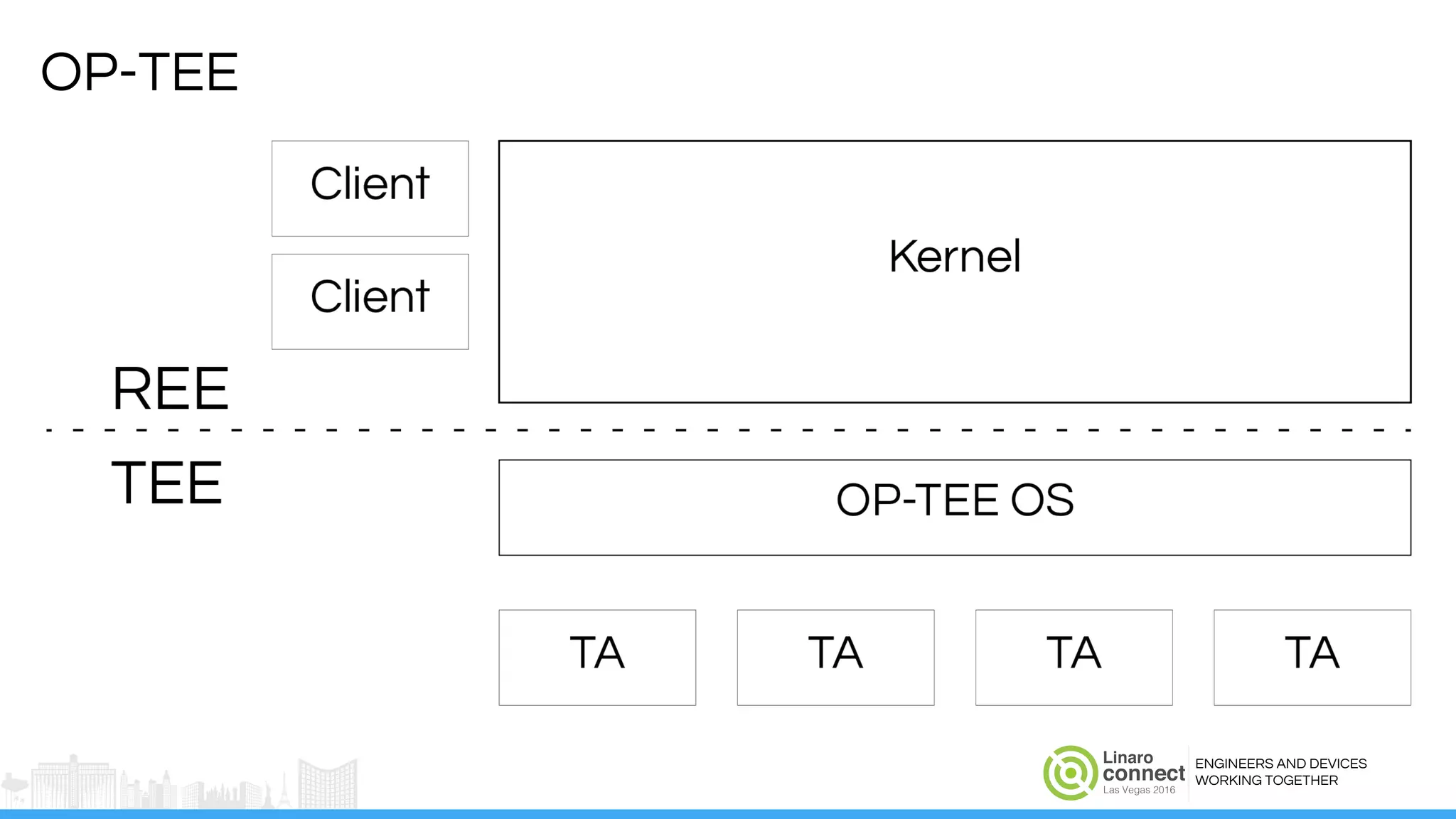
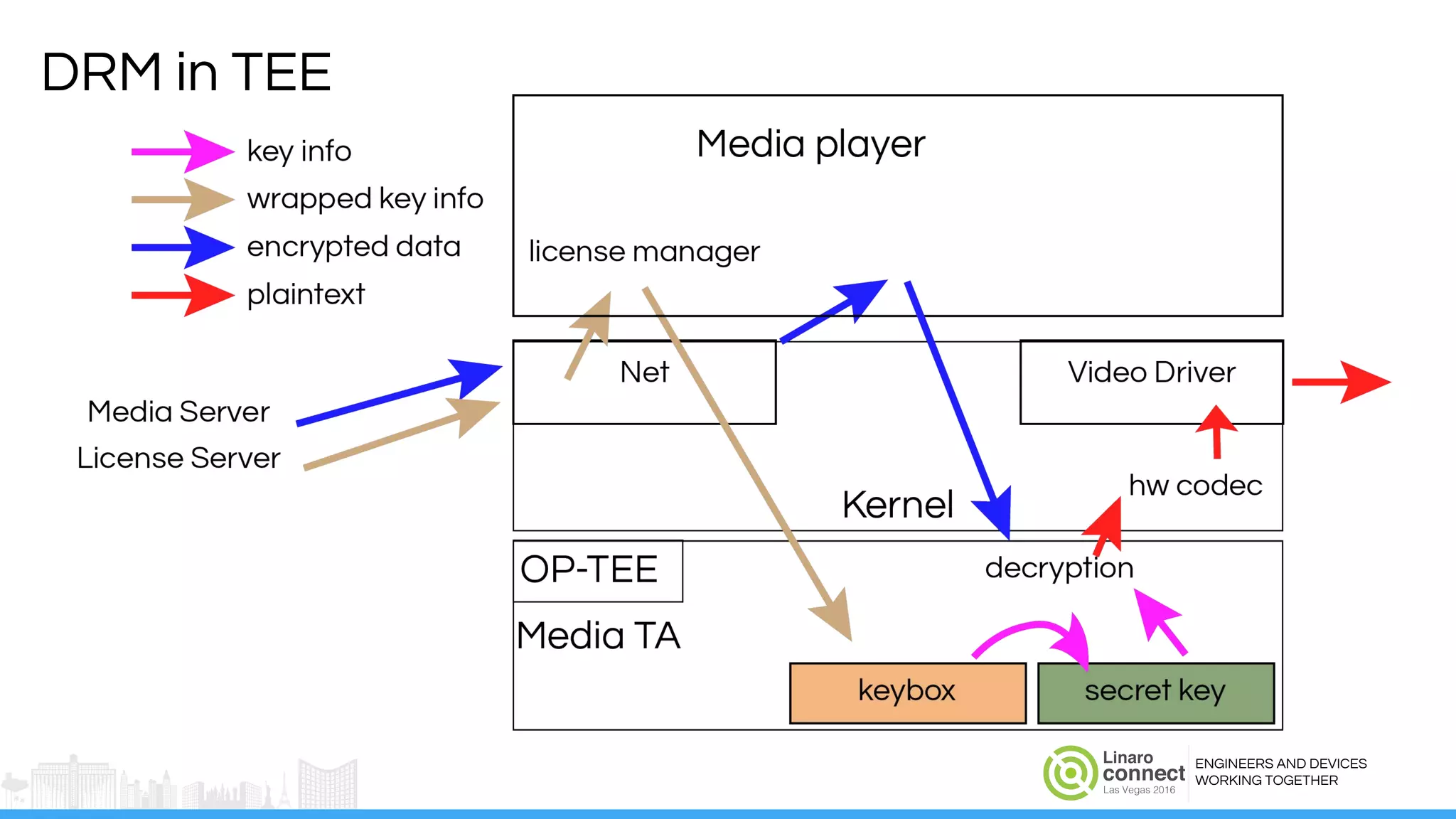
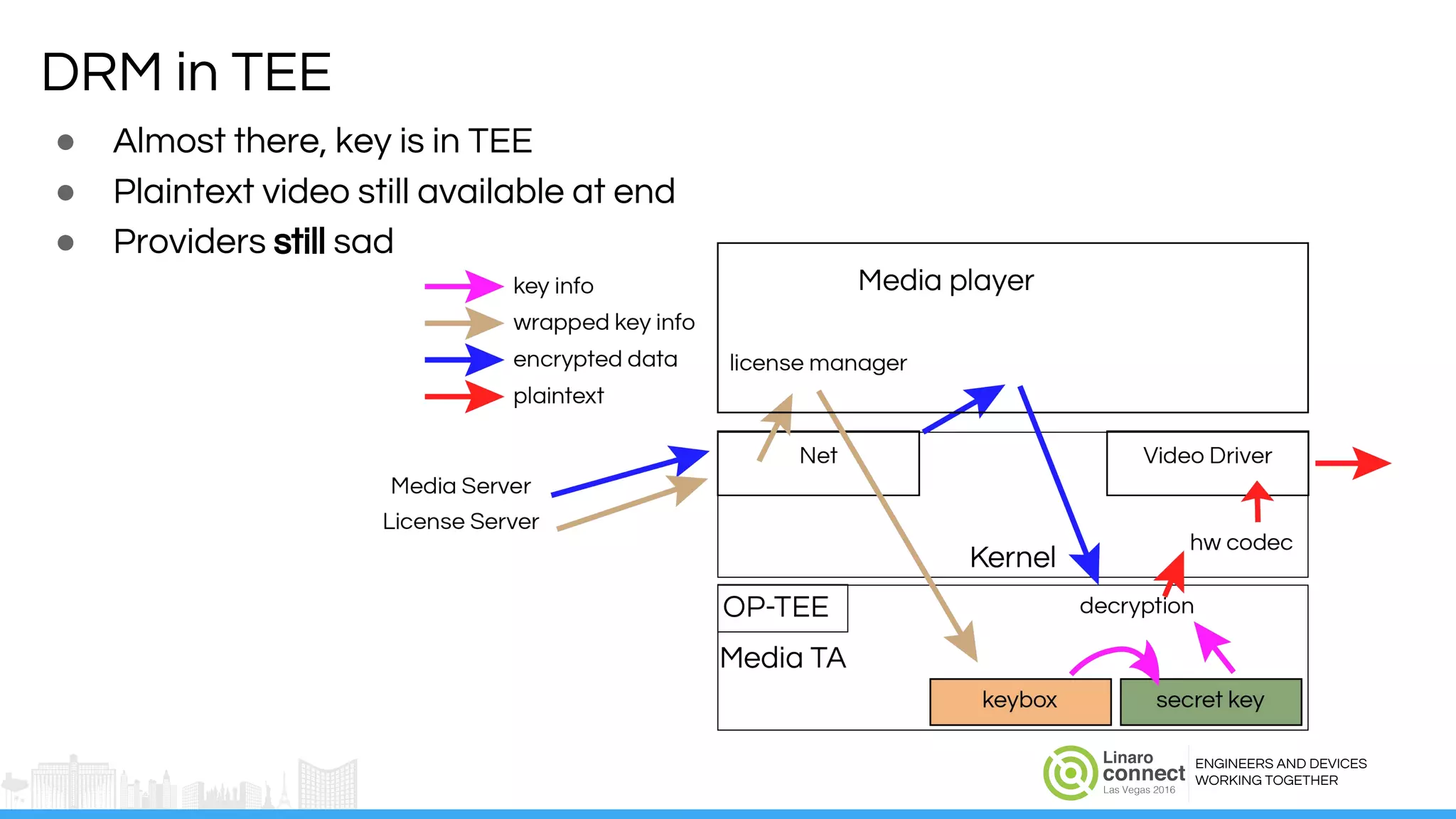
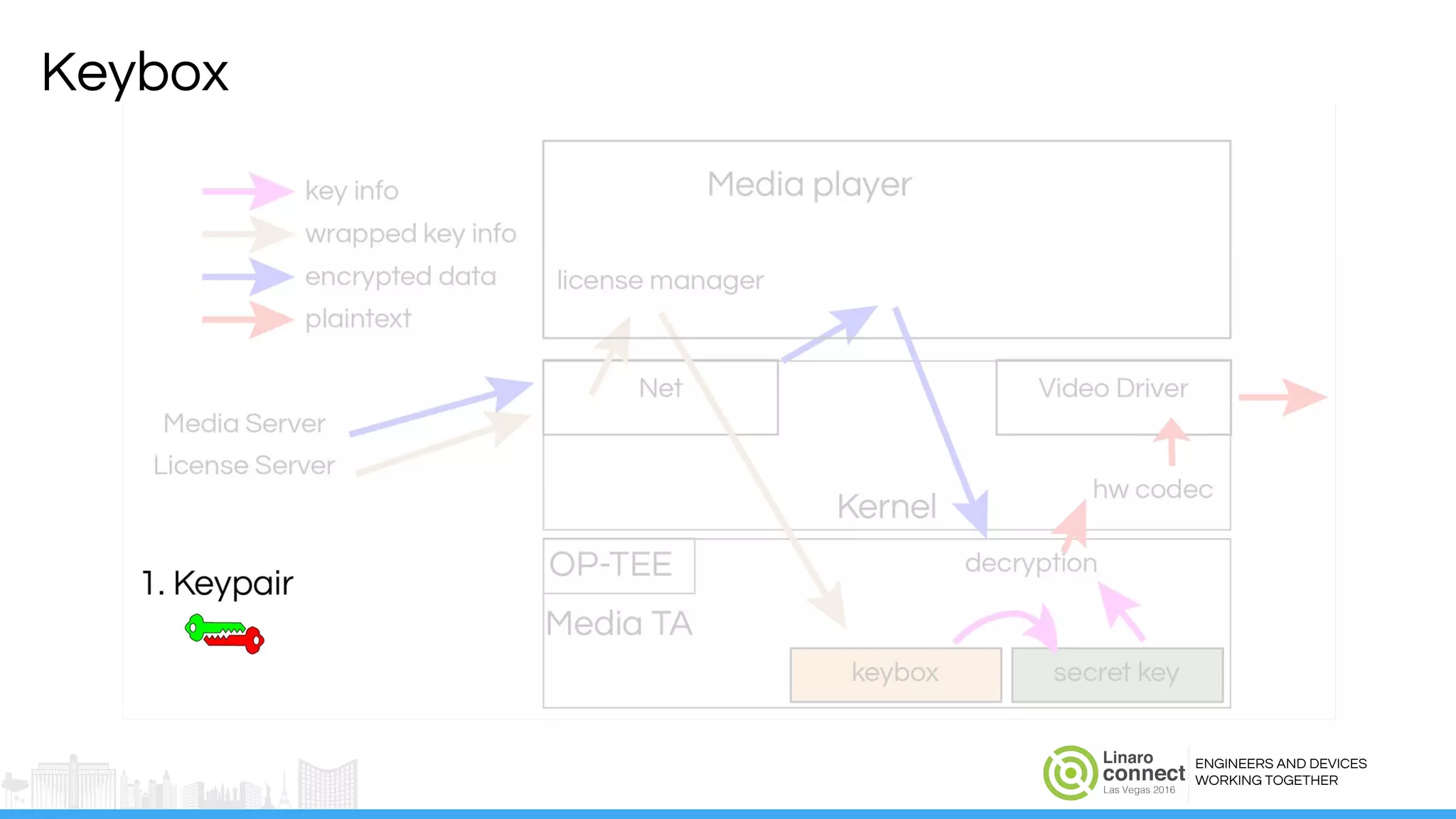
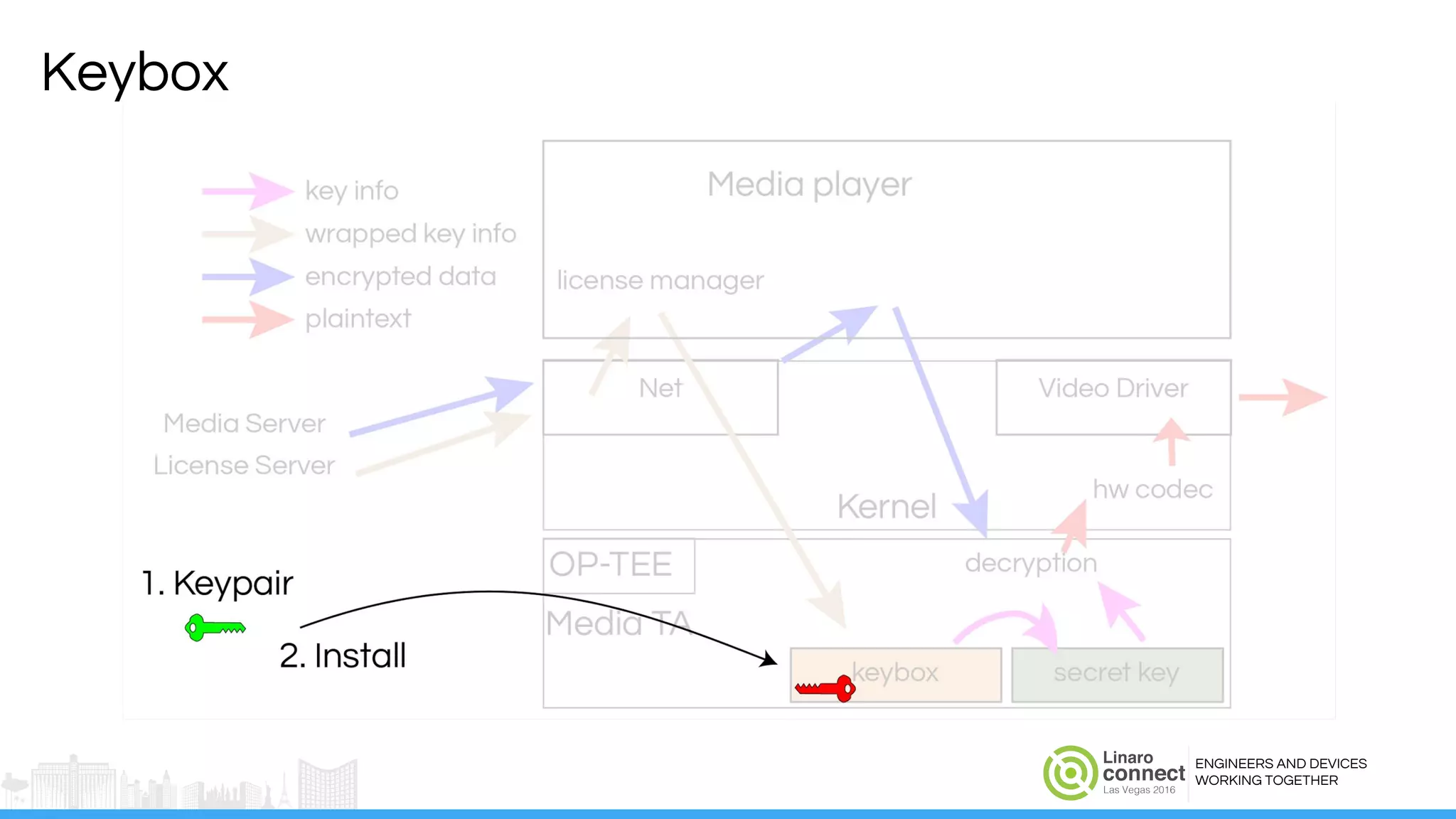
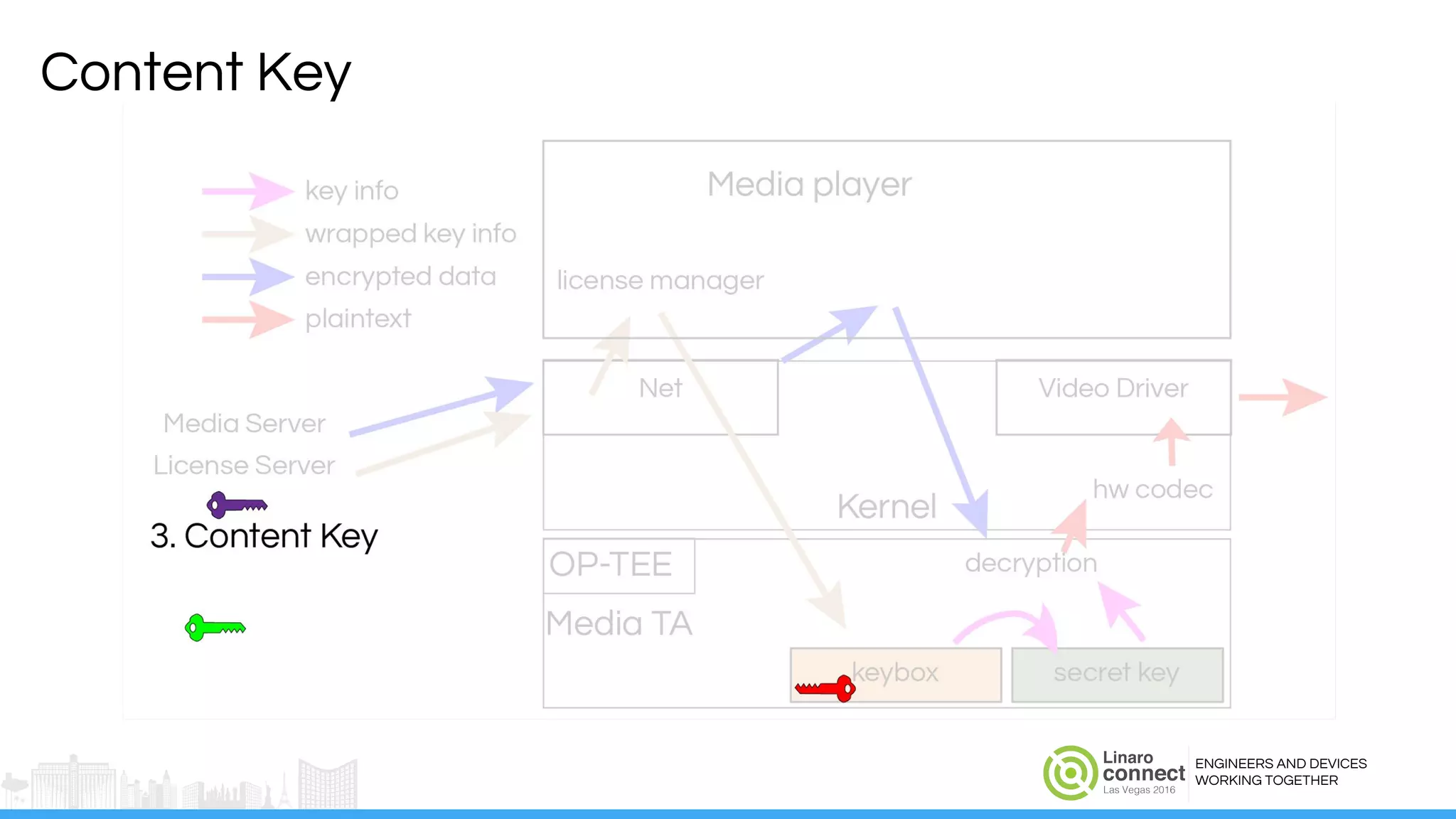
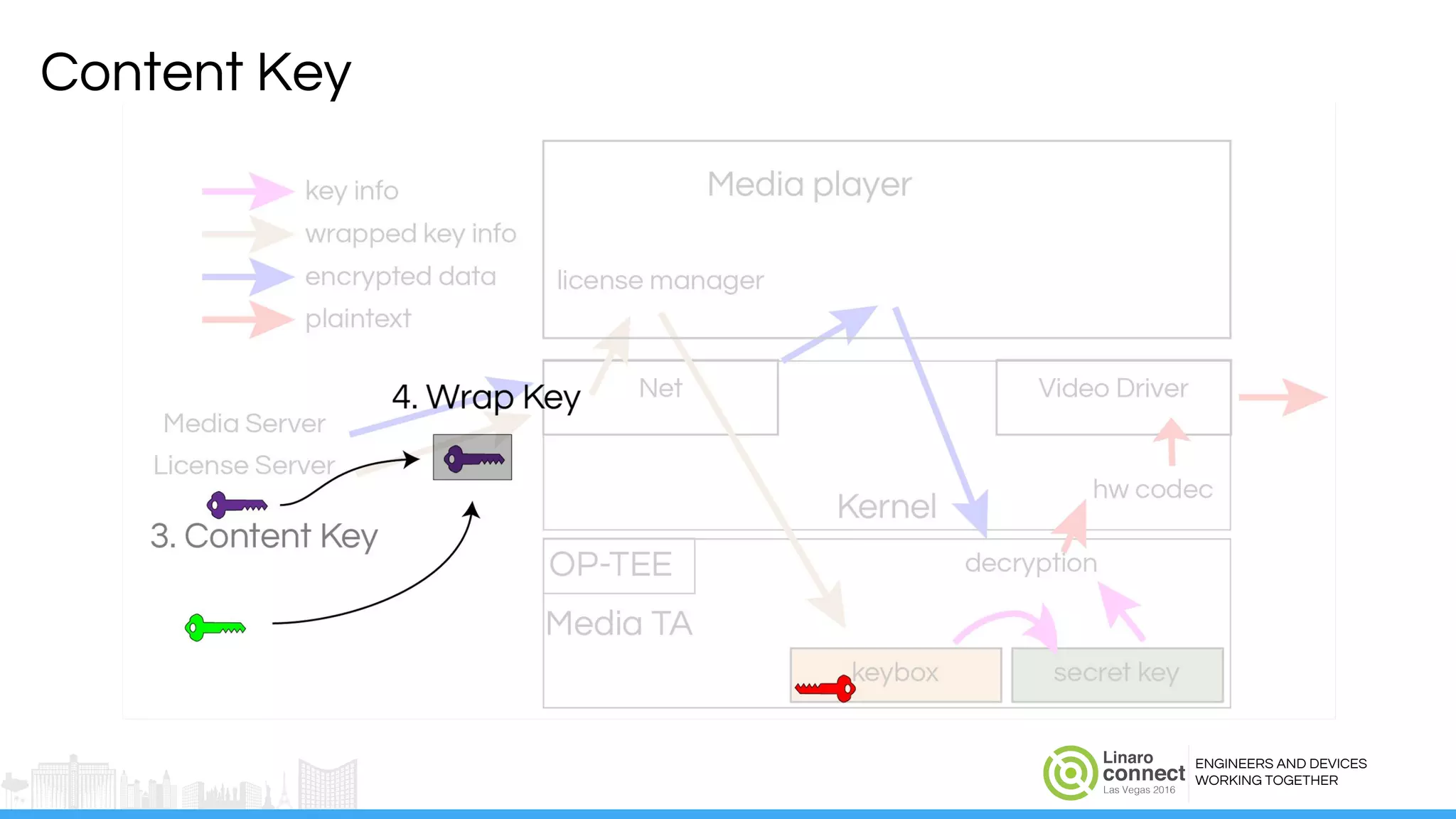
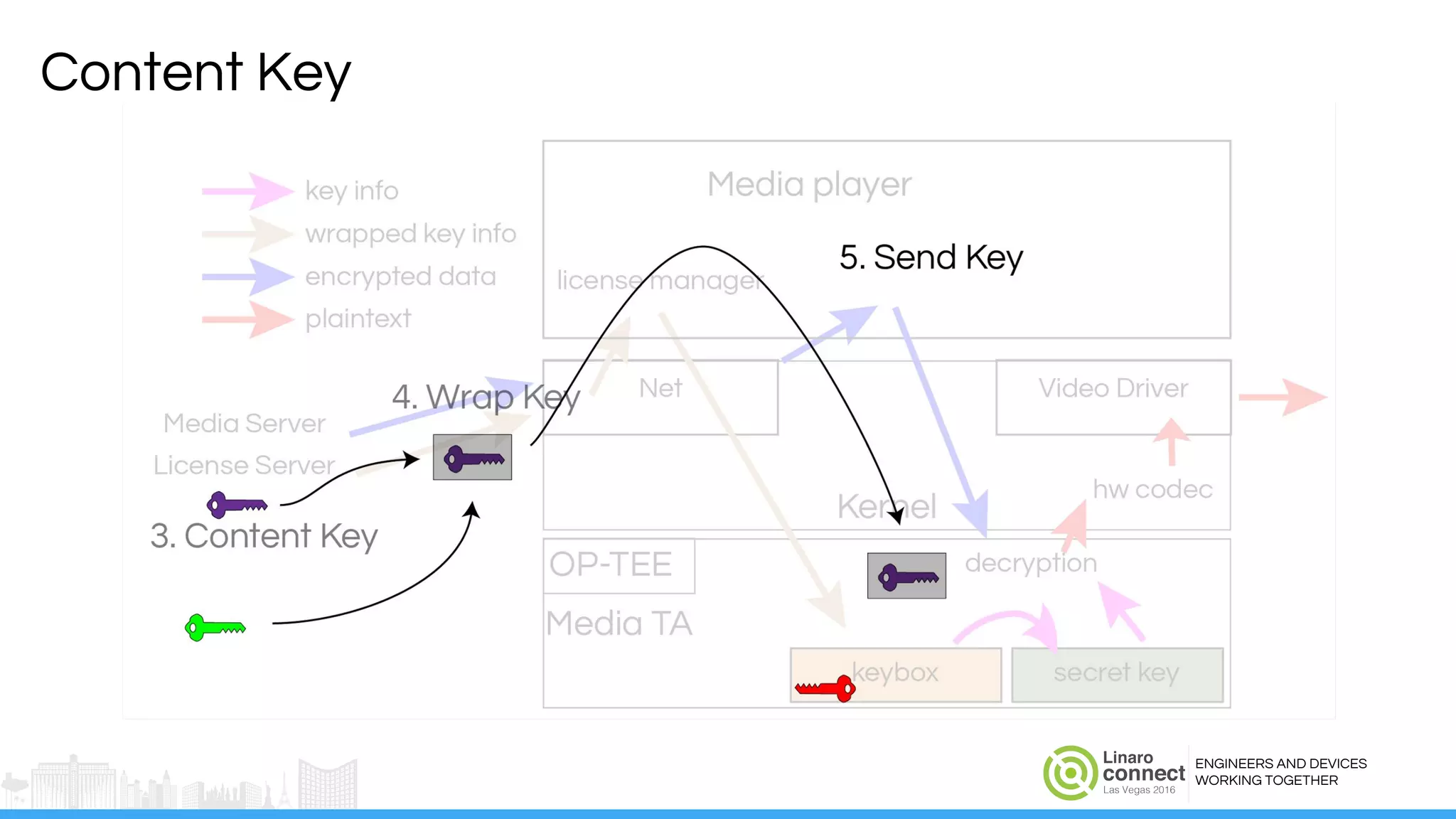
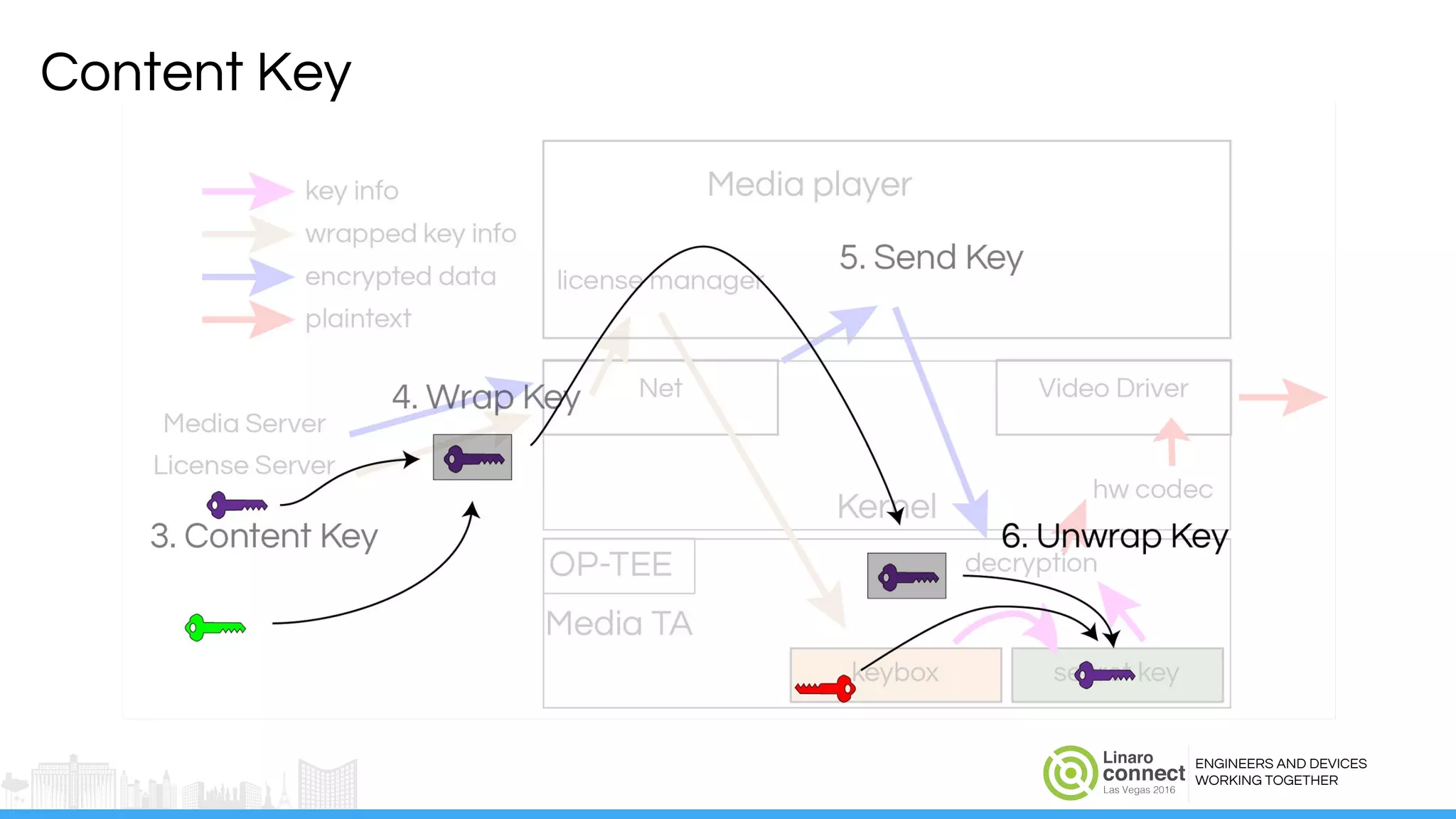
The document discusses the integration of Widevine DRM with OP-TEE for secure media playback on Android devices. It highlights the challenges of managing plaintext video data and key security within user and kernel spaces, and introduces OP-TEE as a solution to secure content. The presentation outlines the current status of implementing this technology, including necessary improvements and ongoing efforts to enhance security features.