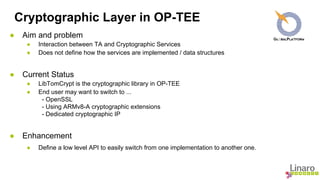
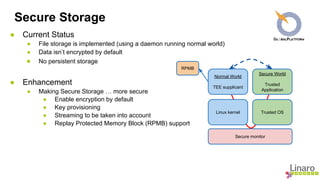
The document outlines future enhancements for OP-TEE, focusing on improvements in cryptographic services, secure storage, and memory management. Key enhancements include defining an API for implementing various cryptographic algorithms, ensuring secure storage encryption by default, and enabling multiple Trusted Applications (TAs) to run in parallel. Additionally, it discusses the aim to support power state coordination interface (PSCI) and integrate address space layout randomization (ASLR) to enhance security.