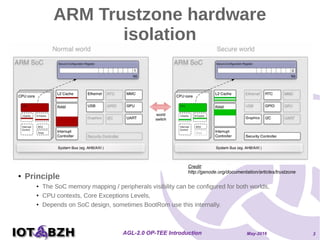
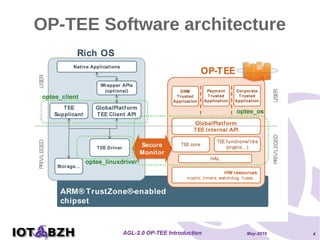
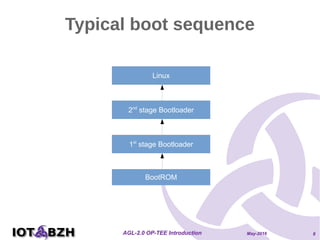
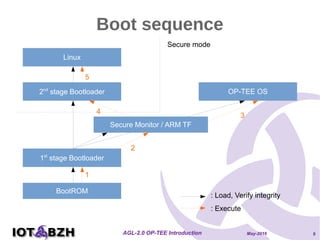
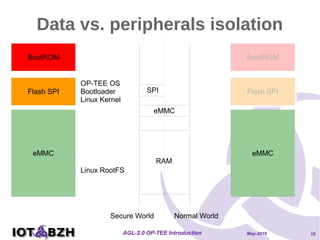
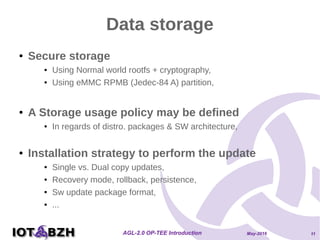
The document provides an overview of OP-TEE, an open-source portable trusted execution environment that implements the Global Platform API on ARM TrustZone. It describes the software architecture, including the interaction between rich execution environments and trusted execution environments, as well as the security measures in place for trusted applications. It further discusses integration with Yocto, features of the Global Platform, and references for additional information.