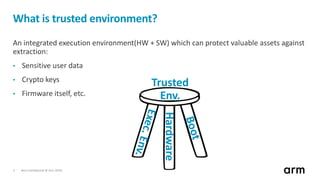
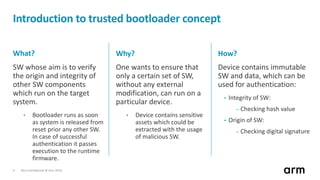
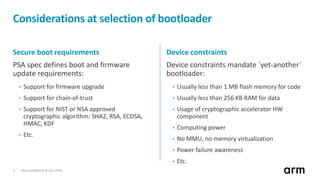
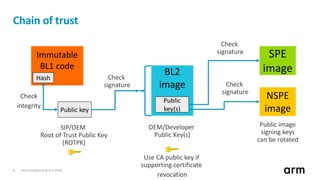
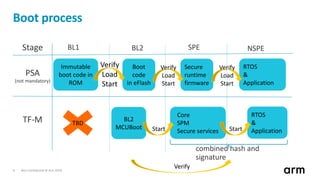
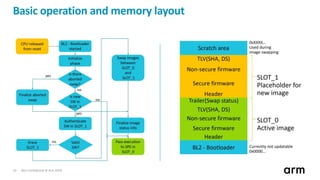
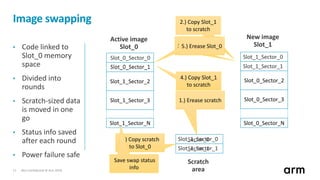
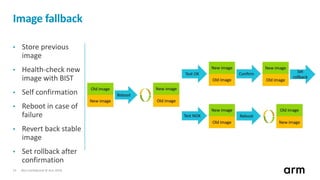
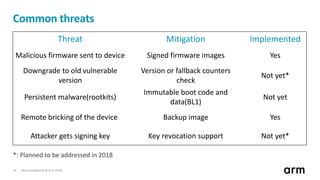
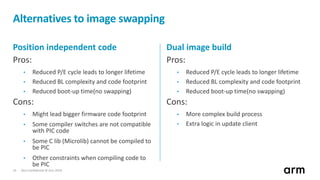
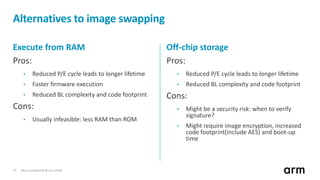
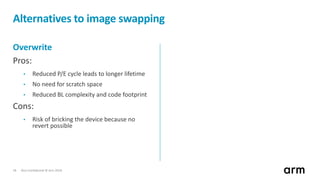
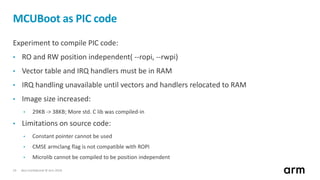
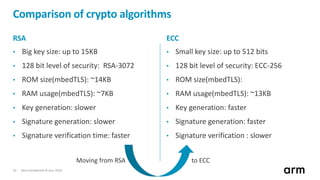
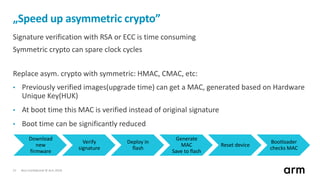
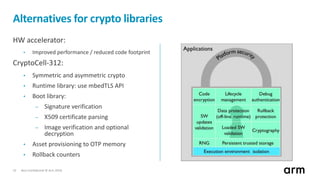
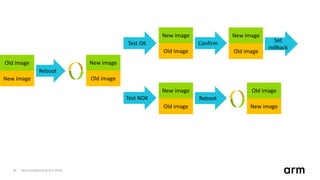
The document discusses the concept of trusted boot and the implementation of a secure bootloader, specifically focusing on the mcuboot project used within the Trusted Firmware-M (TF-M) framework. It covers the importance of firmware integrity, secure boot architecture, firmware upgrades, and various alternatives to improve security and performance in embedded systems. Additionally, it outlines the design constraints, common threats, and future plans for enhancing the bootloader functionalities and security compliance.