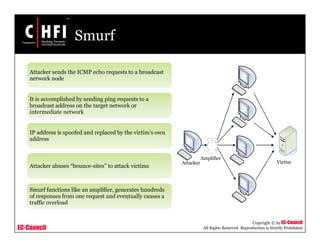
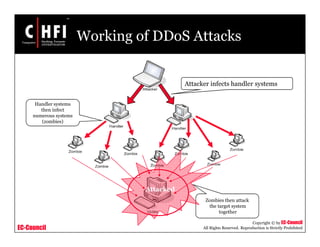
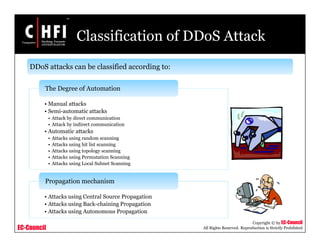
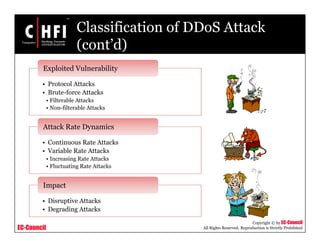
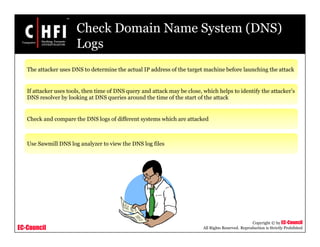
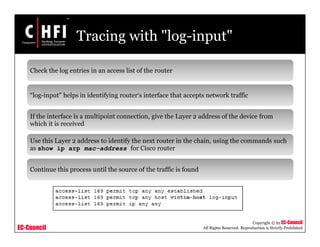
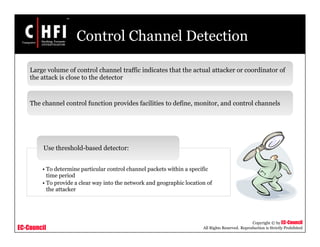
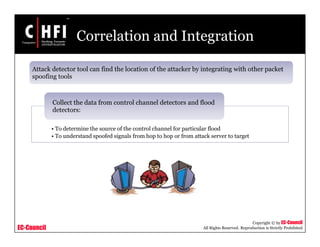
This document provides an overview of techniques for investigating denial of service (DoS) attacks, including distributed denial of service (DDoS) attacks. It describes common types of DoS attacks like SYN flooding, ping of death, and smurf attacks. The document outlines methods for detecting DoS attacks using techniques like activity profiling, change point detection, and wavelet analysis. It also discusses tools like Cisco NetFlow and intrusion detection systems. Methods for investigating DoS attacks discussed include packet traceback, DNS logs, and hop-by-hop traceback to trace attacks back to their source. The challenges of traceback methods and limitations of hop-by-hop traceback are also noted.

















![EC-Council
Copyright © by EC-Council
All Rights Reserved. Reproduction is Strictly Prohibited
Tool: Nmap
Nmap is an open source utility for network exploration or security auditing
Uses raw IP packets to determine the available hosts on the network, services they offer, etc.
•C:CMDTNmap>nmap [Scan Type(s)] [Options] <host or net list>
Syntax:](https://image.slidesharecdn.com/file000144-140617045529-phpapp02/85/File000144-51-320.jpg)