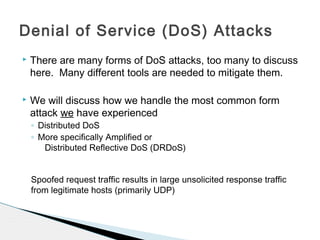
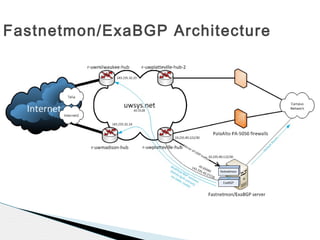
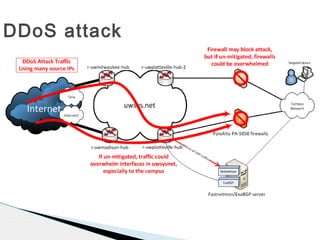
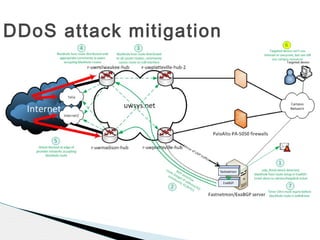
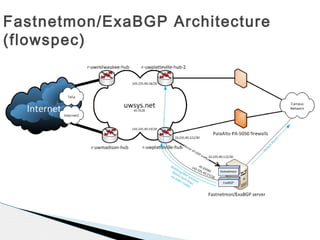
This document discusses using fastnetmon and ExaBGP to monitor and mitigate DDoS attacks at the University of Wisconsin-Platteville. Fastnetmon monitors network traffic in real-time and detects DDoS attacks based on packet, bandwidth, and flow thresholds. It then triggers ExaBGP to inject blackhole routes to drop attack traffic while allowing legitimate traffic to pass. This integrated solution allows the university to automatically detect and mitigate DDoS attacks in near real-time.









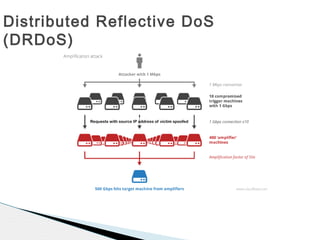
![Distributed Reflected DoS
(DRDoS)
Protocol
Bandwidth
Amplification Factor
Vulnerable Command Protocol/Port
DNS 28 to 54 see: TA13-088A [4] UDP/53
NTP 556.9 see: TA14-013A [5] UDP/123
SNMPv2 6.3 GetBulk request UDP/161
NetBIOS 3.8 Name resolution UDP/137
SSDP 30.8 SEARCH request UDP/1900
CharGEN 358.8
Character generation
request
UDP/19
QOTD 140.3 Quote request UDP/17
BitTorrent 3.8 File search
Kad 16.3 Peer list exchange
Quake Network Protocol 63.9 Server info exchange
Steam Protocol 5.5 Server info exchange
Multicast DNS (mDNS) 2 to 10 Unicast query UDP/5353
RIPv1 131.24 Malformed request UDP/520
Portmap (RPCbind) 7 to 28 Malformed request UDP/111
Source: https://www.us-cert.gov/ncas/alerts/TA14-017A](https://image.slidesharecdn.com/9534715-160210202830/85/9534715-14-320.jpg)



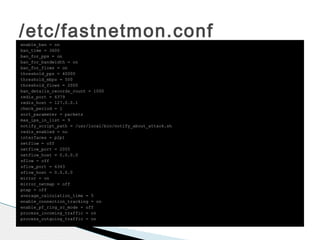





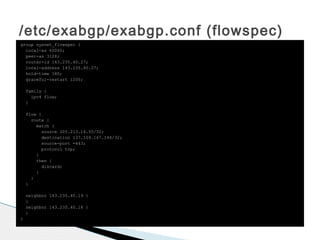
![/etc/exabgp/exabgp.conf# exabgp.conf
# Used to inject blackhole routes into uwsys.net within 137.104.0.0/16
#
# Blackhole Communities:
# uwsysnet_blackhole 3128:911 blackhole this route in AS3128 and upstreams
# uwsysnet_blackhole_internet 3128:912 blackhole this route in upstreams but NOT AS3128#
# Well-Known Communities:
# no-export 65535:65281 do not advertise to any eBGP peers
# no-advertise 65535:65282 do not advertise to any BGP peer
# local-as 65535:65283 do no advertise this route to peers outside the local as
group sysnet_blackhole {
local-as 65060;
peer-as 3128;
router-id 143.235.40.27;
local-address 143.235.40.27;
hold-time 180;
graceful-restart 1200;
family {
ipv4 unicast;
}
static {
# route 10.10.10.1/32 next-hop 192.0.2.1 community 3128:911;
# route 10.10.01.1/32 next-hop 192.0.2.1 community [ 3128:911 65535:65281 ];
# The next line is used to indicate where to automatically add routes at, do not edit it!
# INSERT_NEW
# 2015-09-04 21:46:31 - auto-blachole incoming
route 137.104.212.131/32 next-hop 192.0.2.1 community [3128:911];
# 2015-07-08 03:07:18 - auto-blachole incoming
# 2015-07-08 04:16:18 - route 137.104.231.0/32 next-hop 192.0.2.1 community [3128:911];
}
neighbor 143.235.32.14 {
}
neighbor 143.235.32.15 {
}
}](https://image.slidesharecdn.com/9534715-160210202830/85/9534715-27-320.jpg)



![/etc/exabgp/exabgp.conf (flowspec)
# flowspec syntax:
# flow {
# route give-me-a-name
# route-distinguisher|rd 255.255.255.255:65535|65535:65536|65536:65535; (optional)
# next-hop 1.2.3.4; (to use with redirect-to-nexthop)
# match {
# source 10.0.0.0/24;
# source ::1/128/0;
# destination 10.0.1.0/24;
# port 25;
# source-port >1024
# destination-port =80 =3128 >8080&<8088;
# protocol [ udp tcp ]; (ipv4 only)
# next-header [ udp tcp ]; (ipv6 only)
# fragment [ not-a-fragment dont-fragment is-fragment first-fragment last-fragment ]; (ipv4 only)
# packet-length >200&<300 >400&<500;
# flow-label >100&<2000; (ipv6 only)
# }
# then {
# accept;
# discard;
# rate-limit 9600;
# redirect 30740:12345;
# redirect 1.2.3.4:5678;
# redirect 1.2.3.4;
# redirect-next-hop;
# copy 1.2.3.4;
# mark 123;
# action sample|terminal|sample-terminal;
# }
# }
# }
#
# one or more match term, one action
# fragment code is totally untested](https://image.slidesharecdn.com/9534715-160210202830/85/9534715-32-320.jpg)

![/usr/local/bin/notify_about_attack.sh
#!/usr/bin/env bash
# Blackhole and IP address and notify the NOC
# $1 client_ip_as_string
# $2 data_direction
# $3 pps_as_string
# $4 action (ban or unban)
email_notify=“noc@somewhere.edu"
if [ "$4" = "unban" ]; then
# Unban actions if used
/usr/local/sbin/auto-blackhole remove:$1
exit 0
fi
if [ "$4" = "ban" ]; then
cat | mail -s "FastNetMon Guard: IP $1 $2 attack with power $3 pps" $email_notify;
# You can add ban code here!
exit 0
fi
if [ "$4" == "attack_details" ]; then
cat | mail -s "FastNetMon Guard: IP $1 $2 attack with power $3 pps" $email_notify;
/usr/local/sbin/auto-blackhole $1 $2
exit 0
fi](https://image.slidesharecdn.com/9534715-160210202830/85/9534715-37-320.jpg)


![/usr/local/sbin/exabgp_reload
#!/bin/bash
# This script should read the PID of exabgp from a file
# then check if that PID is running and reload it :)
#
# Originally from www.m00nie.com
PID_FILE=/var/run/exaBGP/exabgp_PID
if [ -f "${PID_FILE}" ]; then
# The file exists so read the PID
PID=`head -n 1 $PID_FILE`
# Check is the process is actuall running
if [ -n "`ps -p ${PID} | grep ${PID}`" ]; then
echo exaBGP is already running [$PID].
# It is so lets reload the config :)
echo sending sighup to reload config...
# Use below for exaBGP < 3.2 (Thanks to Roberto Saavedra for noting this)
# kill -SIGHUP $PID
kill -SIGUSR1 $PID
echo Reload complete
exit
else
# Shouldnt really get here
echo PID file exists but the PID is not running!
exit
fi
fi
# No PID file
echo No PID file found at $PID_FILE](https://image.slidesharecdn.com/9534715-160210202830/85/9534715-40-320.jpg)
