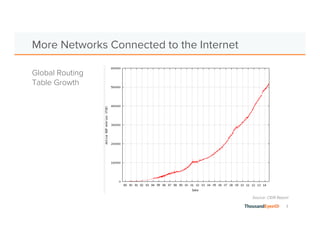
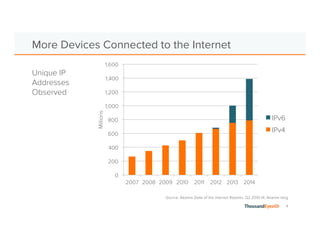
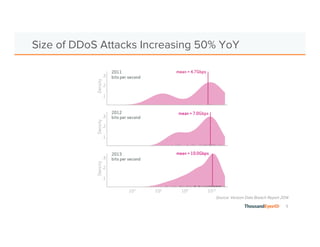
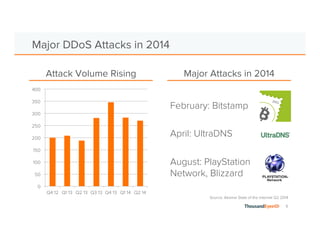
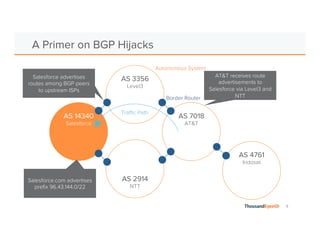
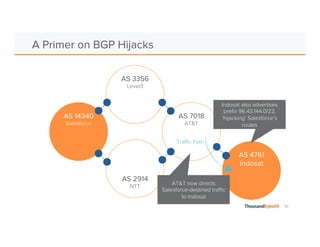
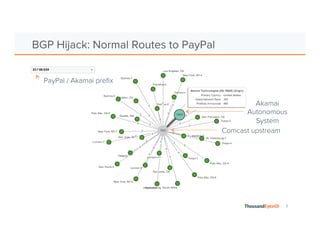
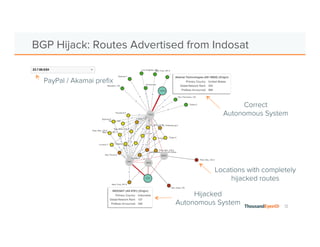
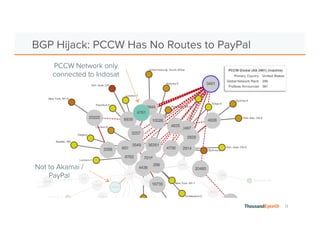
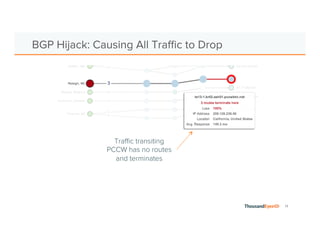
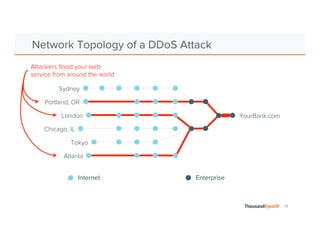
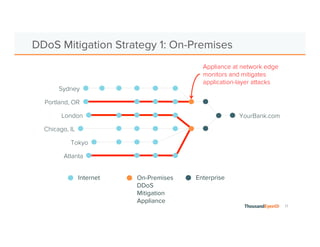
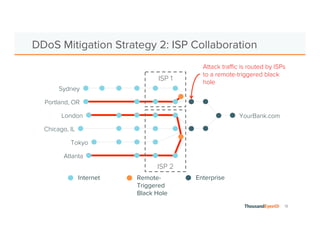
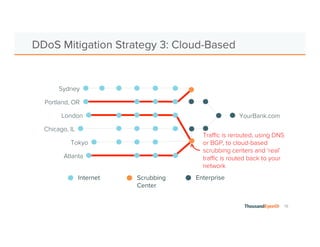
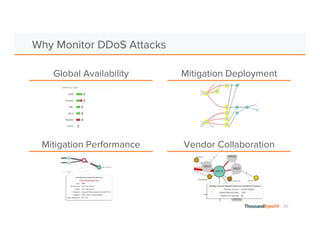
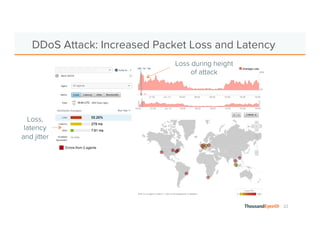
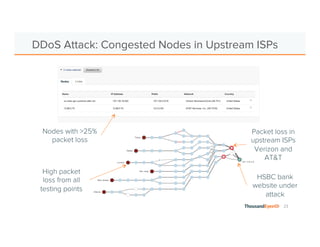
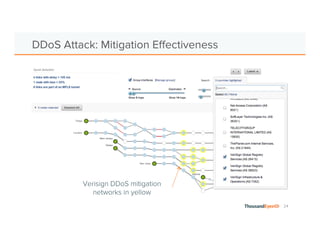
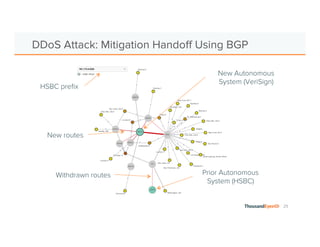
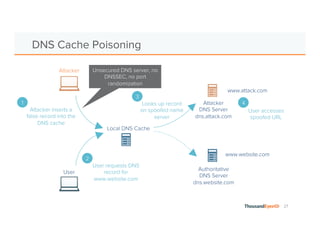
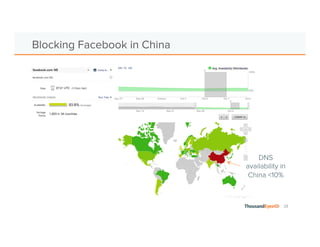
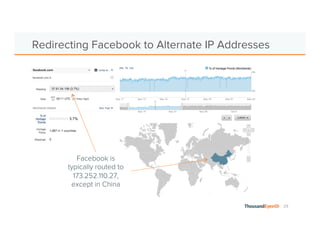
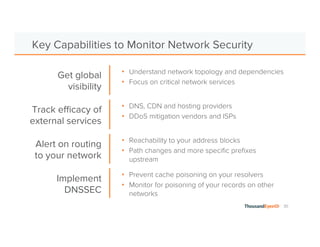
The document discusses the increasing complexity and severity of cyber threats, specifically focusing on DDoS attacks, DNS poisoning, and BGP hijacks. It emphasizes the importance of monitoring network security and implementing effective mitigation strategies to address these threats in a dynamic network environment. The document also highlights ThousandEyes' role in global network performance management and its relevance in today's cyber landscape.