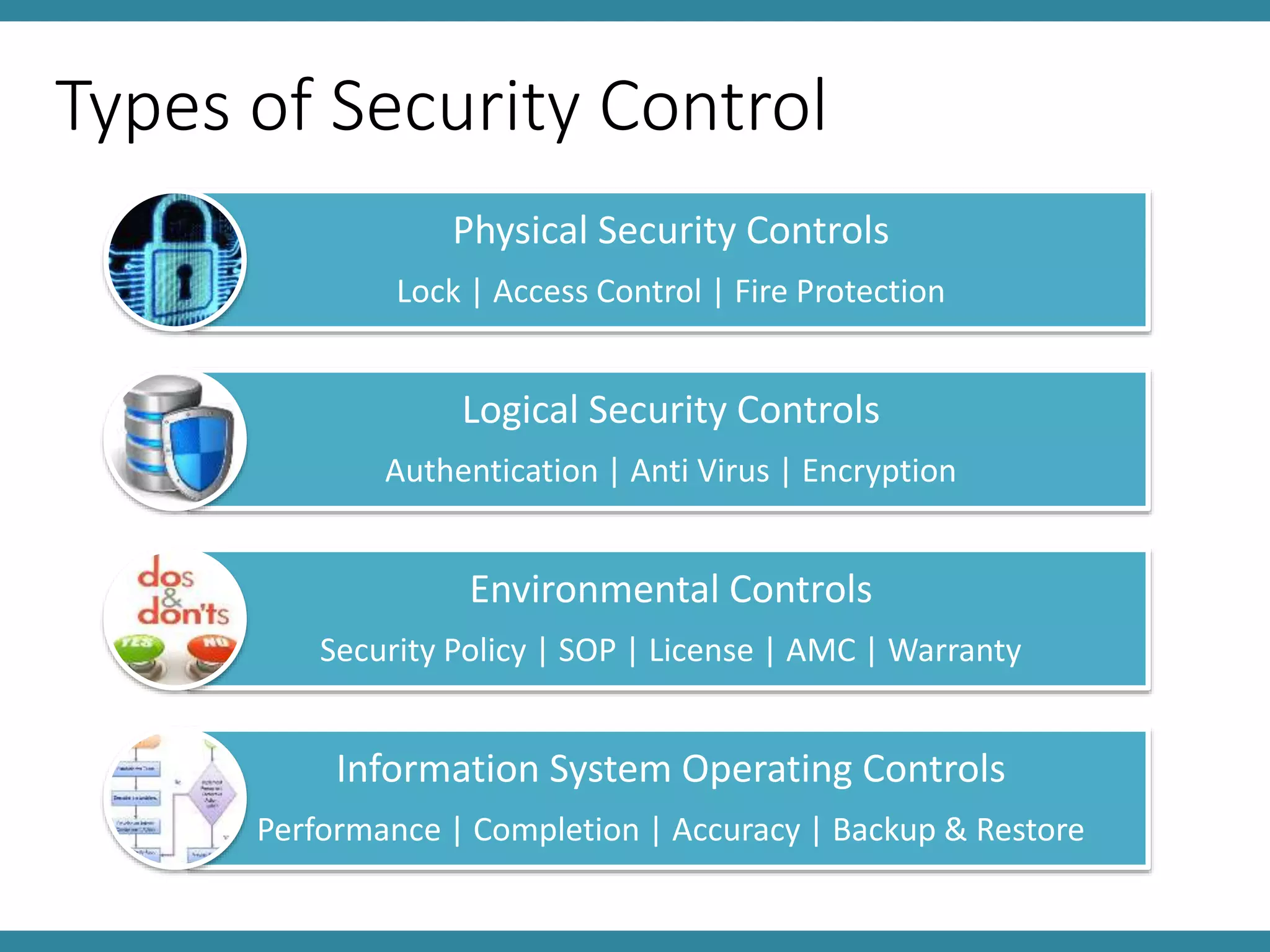
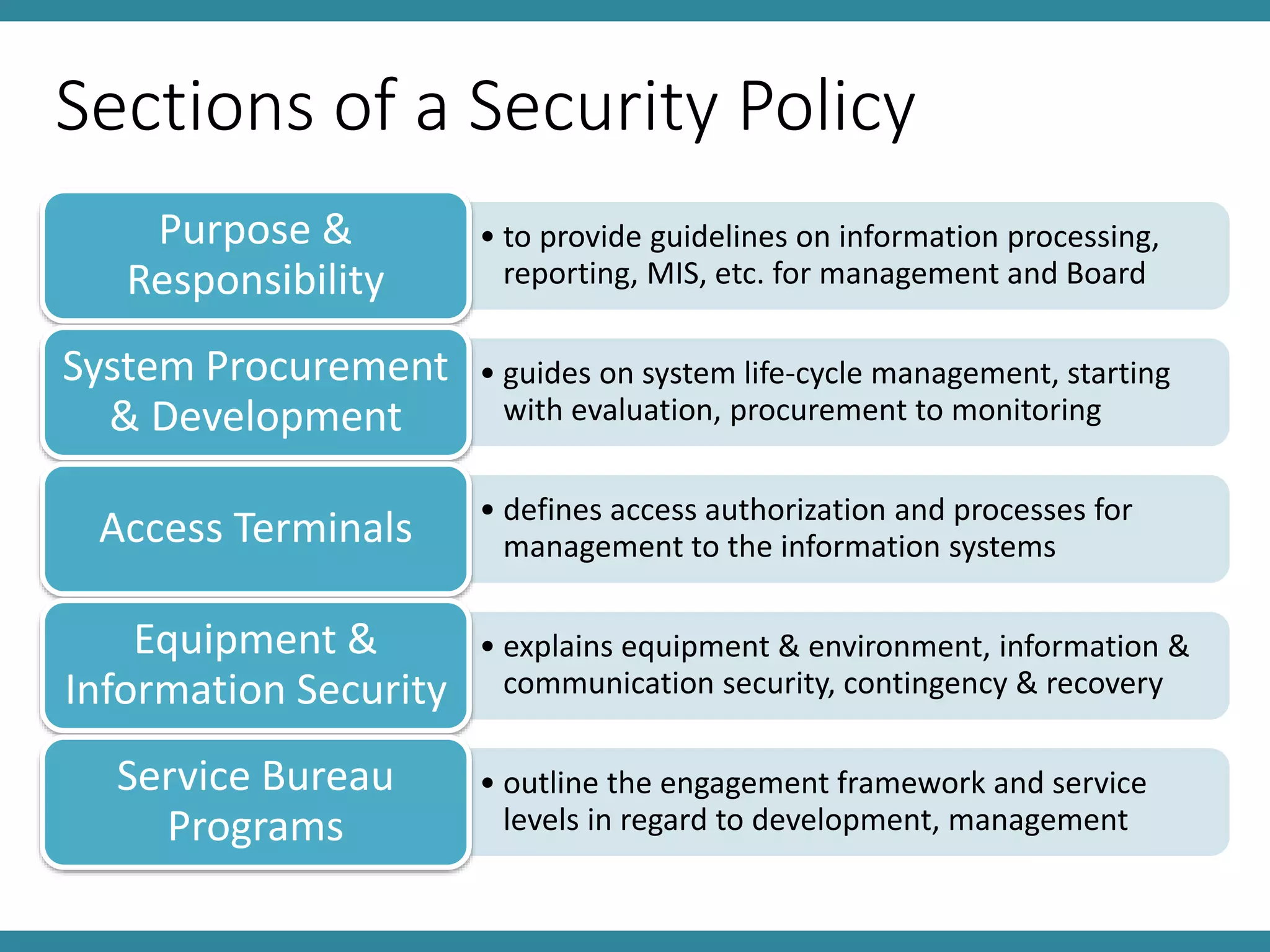
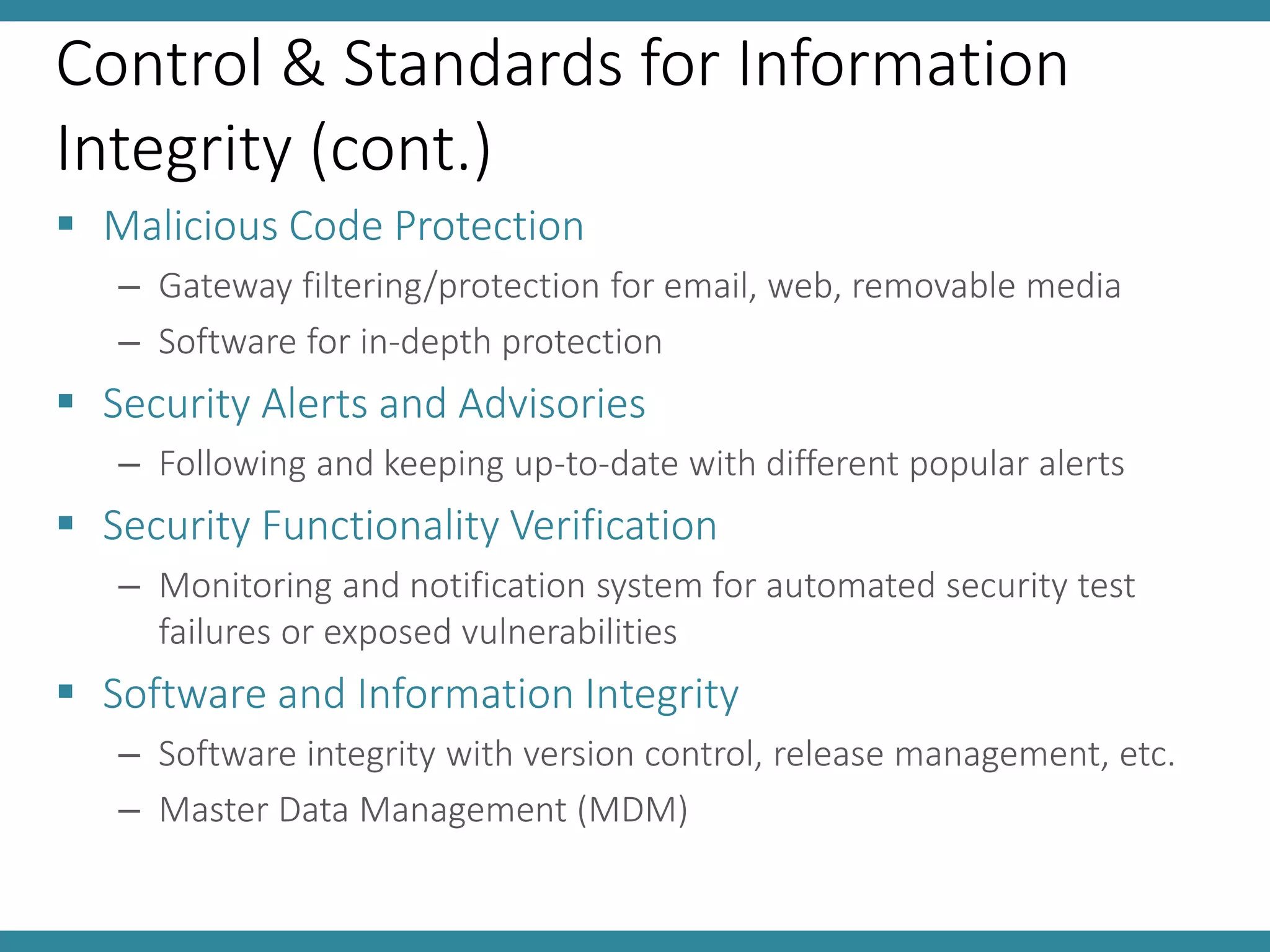
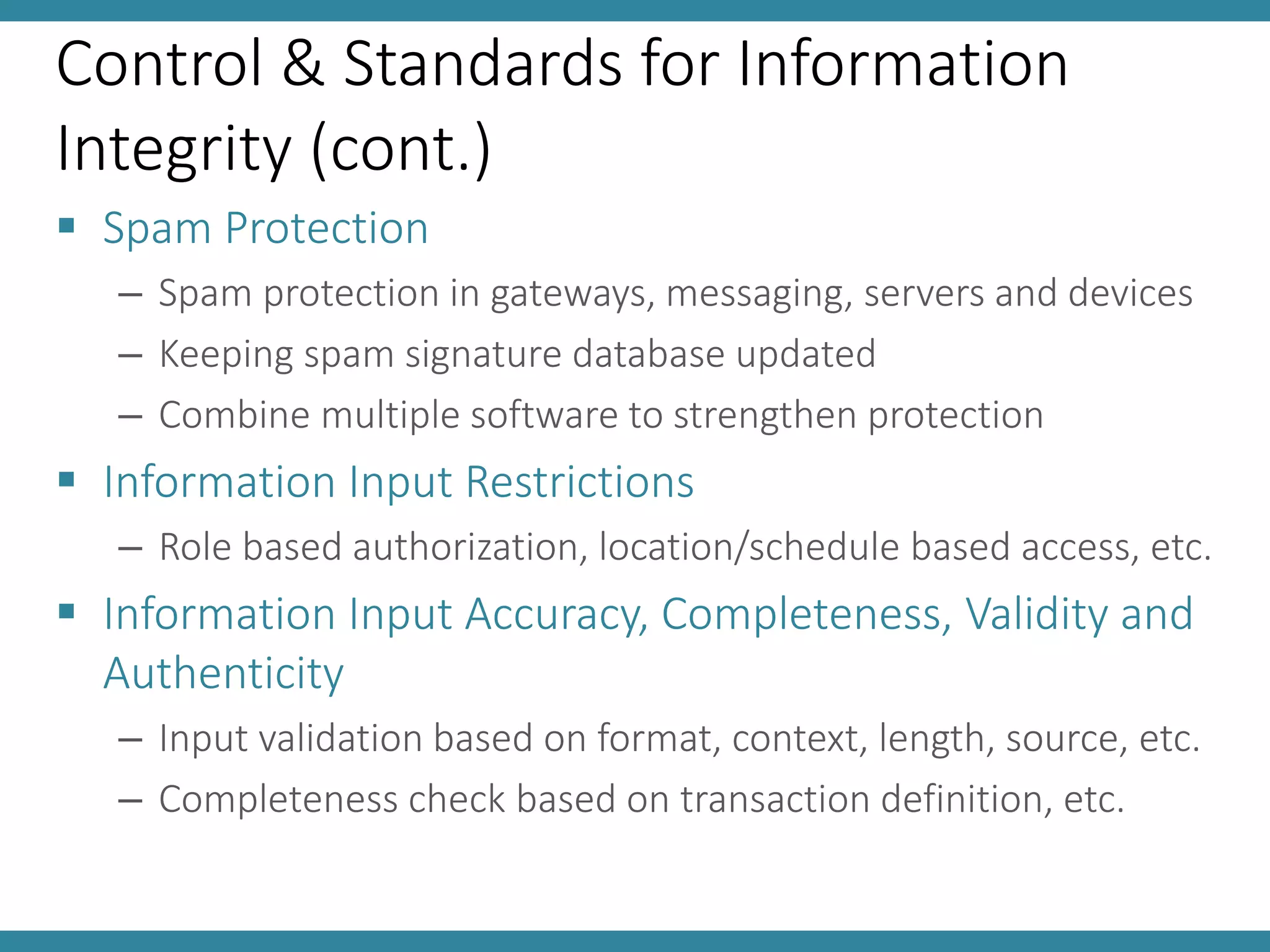
This document discusses controls and standards for information systems security. It covers various types of security controls including physical security controls like locks and access control, and logical security controls like authentication and encryption. It also discusses standards for information integrity, access control, and system implementation and maintenance. The key topics covered are information system security policy, physical and logical security controls, and standards for information integrity, access control, computer audits and system lifecycle management.