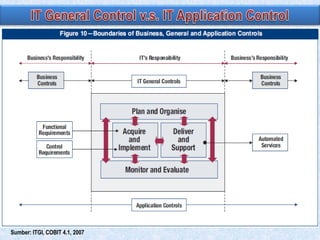
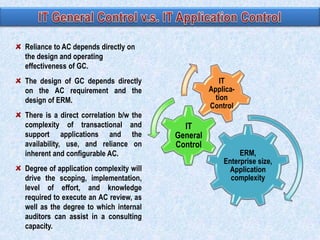
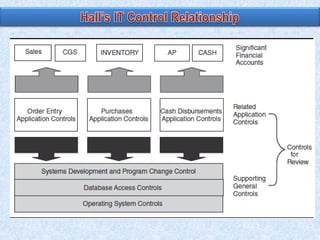
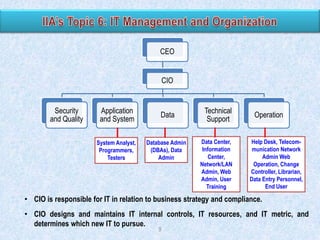
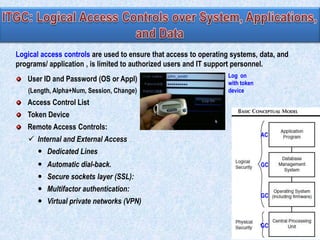
The document discusses two broad groupings of information systems control activities: general controls and application controls. General controls relate to many IS applications and support effective application controls by ensuring continued operation of IS. They include logical access controls, system development life cycle controls, program change management controls, and data center physical security controls. Application controls are designed to ensure complete and accurate processing of data from input through output and include controls over input, processing, and output of applications. The design of general controls depends on application control requirements and enterprise risk management, while reliance on application controls depends on the design and operating effectiveness of general controls.