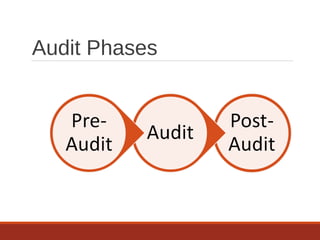
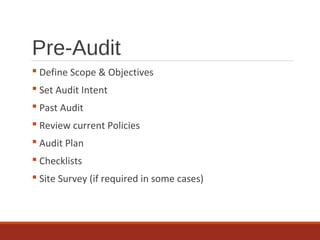
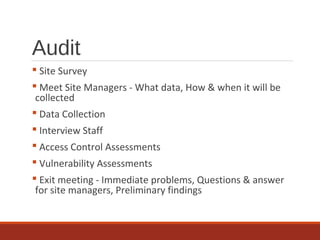
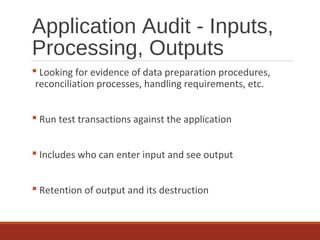
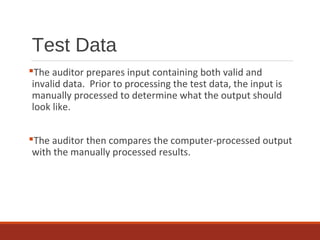
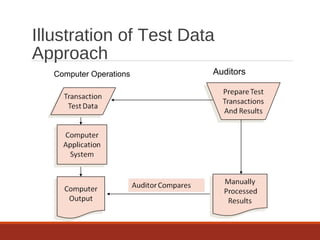
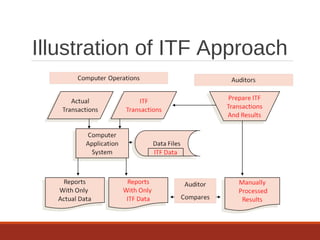
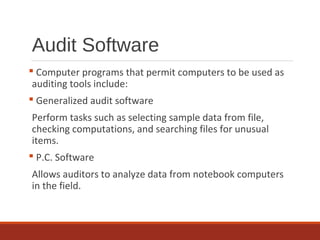
The document provides an overview of IT auditing, detailing the roles and responsibilities of IT auditors, the certifications offered by ISACA, and the phases of an IT audit including pre-audit, audit, and post-audit processes. It discusses various auditing techniques for applications and technology, emphasizing the importance of security, data management, and compliance during audits. Overall, it serves as a comprehensive guide for understanding IT audits and the standards for conducting them effectively.