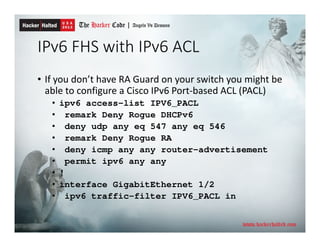
The document discusses IPv6 security threats, highlighting that many networks unknowingly utilize IPv6 capabilities by default, which presents significant security risks. It outlines various IPv6 attack tools and methods for reconnaissance, as well as potential local area network threats and attacks, particularly around the neighbor discovery protocol. Recommendations for securing IPv6 networks include implementing network access controls, filtering traffic, and ensuring equal protections for IPv6 as for IPv4.




![Reconnaissance
• Ping sweeps, port scans, application vulnerability scans are
problematic given the large IPv6 address space.
• Brute-force scanning even a single /64 is not practical.
• There are methods of speeding up reconnaissance on LAN.
• ping6 -I eth0 ff02::1
• [root@hat ~]# ./alive6 eth0 ff02::1
• Node Information Queries (RFC 4620) in BSD
• Scanning for specific EUI-64 addresses using specific OUIs
• Scanning IPv4 and getting IPv6 info
• Metasploit Framework “ipv6_neighbor" auxiliary module can leverage IPv4
to find IPv6 hosts
• Scanning 6to4, ISATAP, Teredo with embedded IPv4 addresses
• Find one node and leverage the neighbor cache to find other nodes
• DHCPv6 logs, DNS servers, server logs, NMSs, Google Hacking](https://image.slidesharecdn.com/ipv6securityhackerhalted2013-130930121444-phpapp02/85/IPv6-Security-Hacker-Halted-2013-5-320.jpg)







![IPv6 First Hop Security Results
• Switch successfully blocked RAs and rogue DHCPv6
Switch-1# show ipv6 snoop counter interface gigabitethernet 2/0/2
Received messages on Gi2/0/2:
Protocol Protocol message
NDP RA[14734]
DHCPv6 SOL[191] ADV[1]
Bridged messages from Gi2/0/2:
Protocol Protocol message
NDP
DHCPv6 SOL[191]
Dropped messages on Gi2/0/2:
Feature Protocol Msg [Total dropped]
DHCP Guard DHCPv6 ADV [1]
reason: Message type is not authorized by the policy on this
port, device-role mismatch [1]
RA guard NDP RA [14734]
reason: Message unauthorized on port [14734]
Switch-1#](https://image.slidesharecdn.com/ipv6securityhackerhalted2013-130930121444-phpapp02/85/IPv6-Security-Hacker-Halted-2013-15-320.jpg)
![IPv6 First Hop Security Results
• Switch successfully blocked RAs and rogue DHCPv6
Switch-1# show ipv6 snoop counter interface gigabitethernet 2/0/1
Received messages on Gi2/0/1:
Protocol Protocol message
NDP RS[11] RA[2794] NS[51] NA[7031]
DHCPv6 SOL[142]
Bridged messages from Gi2/0/1:
Protocol Protocol message
NDP RS[11] NS[50] NA[15]
DHCPv6 SOL[142]
Dropped messages on Gi2/0/1:
Feature Protocol Msg [Total dropped]
RA guard NDP RA [2794]
reason: Message unauthorized on port [2794]
Snooping NDP NS [1]
reason: Packet accepted but not forwarded [1]
NA [7016]
reason: Address limit per policy reached [7007]
reason: Packet accepted but not forwarded [9]
Switch-1#](https://image.slidesharecdn.com/ipv6securityhackerhalted2013-130930121444-phpapp02/85/IPv6-Security-Hacker-Halted-2013-16-320.jpg)