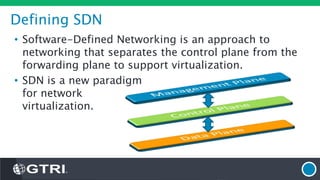
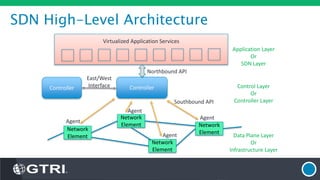
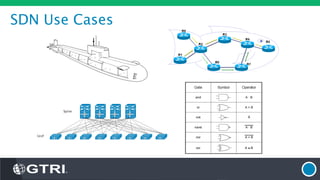
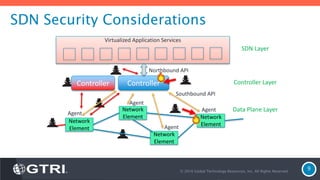
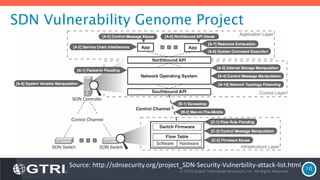
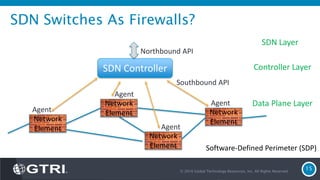
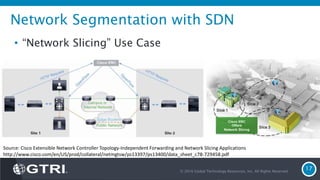
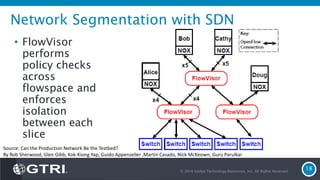
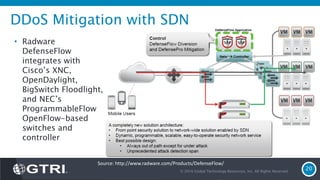
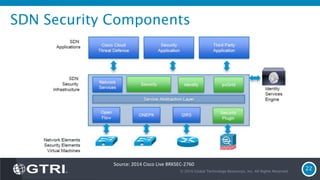
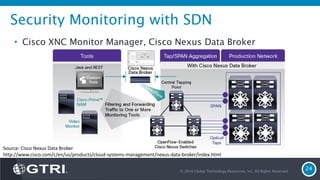
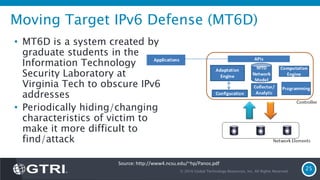
The document discusses Software-Defined Networking (SDN) and its security implications, focusing on the separation of the control and data planes for improved network management. It highlights potential attack vectors and vulnerabilities within SDN systems, as well as methods for hardening security and innovative security use cases. The presentation concludes with resources for further exploration and offers a free technology review for interested companies.