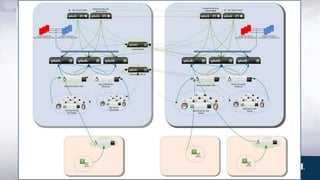
This document contains summaries of multiple case studies involving the use of Splunk software for security and compliance purposes. The first case study involves a large multi-national company that implemented Splunk across 140 global data centers to address accountability, auditing, security and compliance concerns. The second case study outlines how a private aerospace firm used Splunk to create a centralized security incident and event management solution across multiple US data centers. The third case study describes how a US federal agency implemented Splunk and hired staff to fully enable a new 24/7 Security Operations Center. Additional brief case studies describe how Denver Water and the University of Texas at Austin also utilize Splunk.