The document provides an overview of IPv6 for penetration testing, covering essential terminology, practices for connecting to IPv6 services, and challenges posed by non-IPv6 aware tools. It discusses local and remote scanning techniques, limitations of common security configurations, and tools to facilitate IPv6 usage. Additionally, it highlights the significance of understanding IPv6 in a penetration testing context and offers practical examples and resources for further exploration.

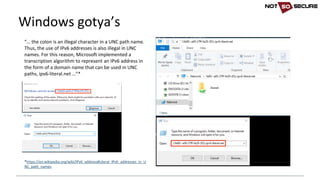


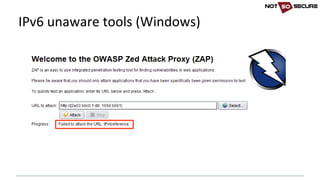
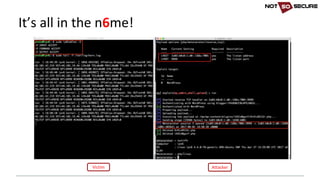
![Talking to the target
server
{
listen [::]:80 default_server;
root /var/www/html/ipv6;
server
{
listen 80 default_server;
root /var/www/html/ipv4;](https://image.slidesharecdn.com/ipv6forpentestersv3-170609120531/85/IPv6-for-Pentesters-13-320.jpg)
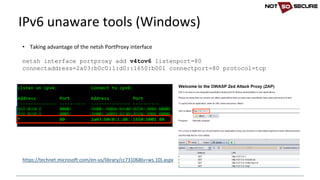
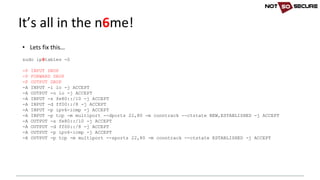
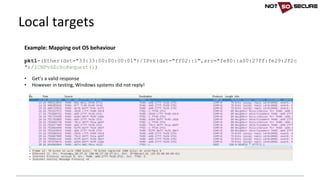
![• IPv6 aware:
wpscan --url http://[2a03:b0c0:1:d0::1650:b001]/wp/ --enumerate u
[+] URL: http://[2a03:b0c0:1:d0::1650:b001]/wp/
[snip]
[+] Enumerating usernames ...
[+] Identified the following 1 user/s:
+----+---------+----------------+
| Id | Login | Name |
+----+---------+----------------+
| 1 | blogger | blogger – IPv6 |
+----+---------+----------------+
• IPv6 unaware:
nikto -host http://[2a03:b0c0:1:d0::1650:b001]
- Nikto v2.1.6
---------------------------------------------------------------------------
+ ERROR: Cannot resolve hostname '[2a03'
+ 0 host(s) tested
IPv6 unaware tools (Linux)](https://image.slidesharecdn.com/ipv6forpentestersv3-170609120531/85/IPv6-for-Pentesters-15-320.jpg)
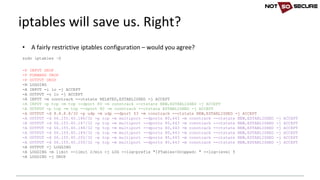
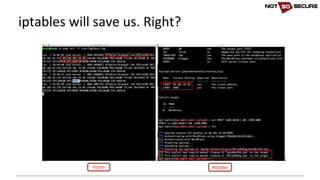
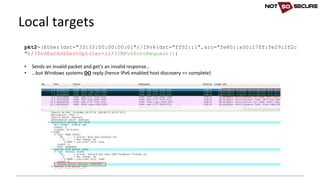
![• Forcing a square peg into a round hole…
socat -v tcp4-listen:80,fork tcp6:[2a03:b0c0:1:d0::1650:b001]:80
[snip]...
< 2017/05/26 17:12:03.734587 length=313 from=151 to=463
r
7br
<!DOCTYPE html>
<html>
<body>
<H1>You hit my IPv6 page!</H1>Your IP: 2002:xxxx:xxxx:10:99d8:b8d5:b5e0:fef
nikto -host http://127.0.0.1
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 127.0.0.1
+ Target Hostname: 127.0.0.1
+ Target Port: 80
+ Start Time: 2017-05-26 17:12:03 (GMT1)
---------------------------------------------------------------------------
+ Server: nginx/1.10.0 (Ubuntu)
+ The anti-clickjacking X-Frame-Options header is not present.
IPv6 unaware tools (Linux)](https://image.slidesharecdn.com/ipv6forpentestersv3-170609120531/85/IPv6-for-Pentesters-16-320.jpg)