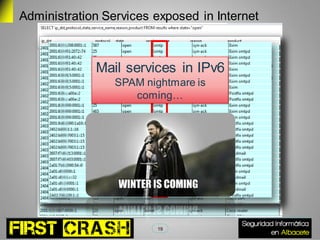
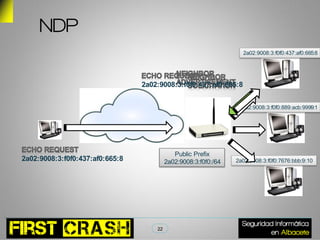
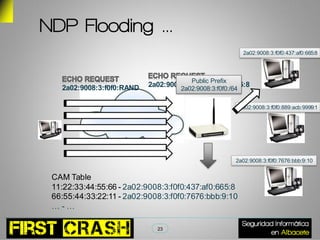
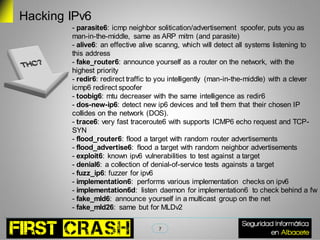
This document discusses IPv6 security risks. It begins with a brief introduction to IPv6 and its address types. It then outlines some hacking tools for IPv6 like parasite6 for man-in-the-middle attacks. Research results show administration services are exposed on the public internet through IPv6 prefixes. A demo shows tunneling and NDP flooding attacks on IPv6 networks. The document concludes by asking if the audience has any questions.





![Hacking IPv6
IPv6(dst="2a02:9001:0:ffff:80:58:105:253")/
IPv6ExtHdrRouting(type=0,addresses=["2a02:9001:0:57::6"])/
ICMPv6EchoRequest()
#!/usr/bin/pythonfrom
scapy.all import *
def aleatorio():
ff=str(RandIP6())
ff=ff[20:39]
return ff
for i in range(1,100000):
packet=IPv6(src="2001:5c0:1400:a:8000:0:580c:3aa",dst="2a02:9008:3:111:"
+(aleatorio()))/ICMPv6EchoRequest()
send(packet,iface="sit1")
8](https://image.slidesharecdn.com/crash-133899603696-phpapp02-120606102219-phpapp02/85/Crash-8-320.jpg)