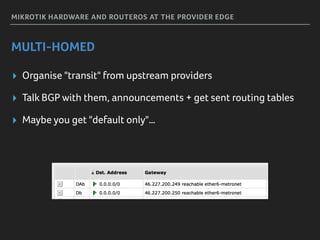
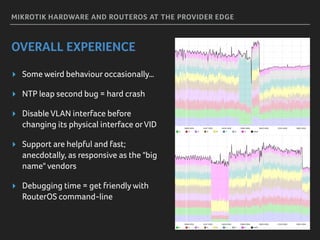
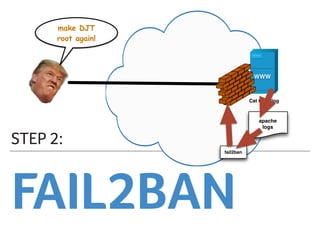
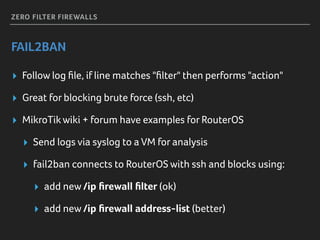
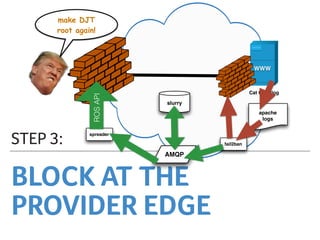
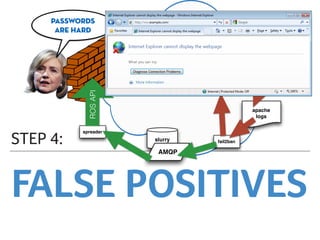
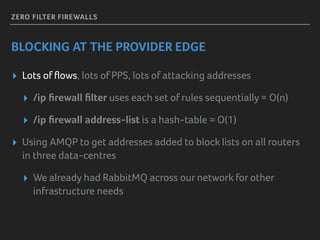
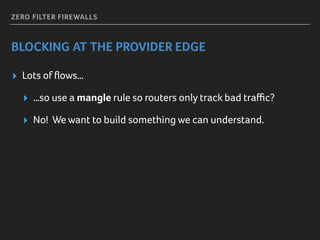
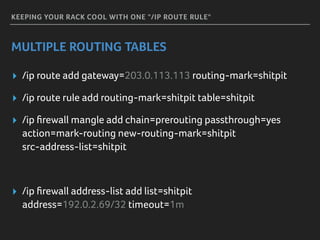
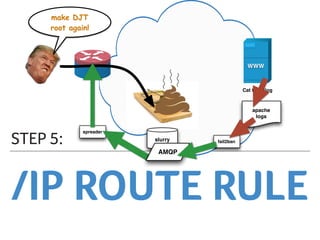
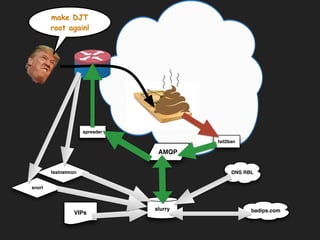
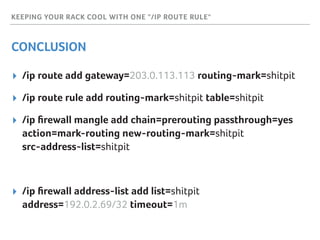
Marek discusses how his company Faelix uses MikroTik hardware and RouterOS at their network edges to route over 600k IPv4 and 30k IPv6 routes. While there were some initial issues, MikroTik has proven reliable and cost-effective. Marek then explains how Faelix implements firewalling with zero filter rules through a multi-step process. They use fail2ban to block brute force attacks, AMQP to share block lists across routers, and destination NAT misbehaving traffic. Most importantly, they leverage the "/ip route rule" feature to route blocked traffic to a separate routing table for easy isolation without complex firewall rules.