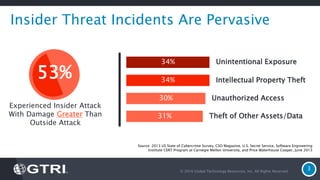
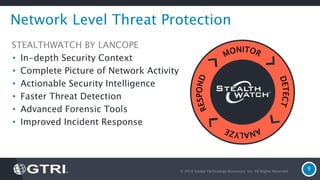
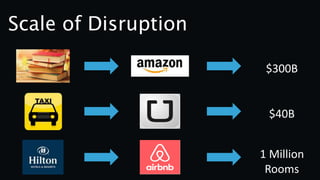
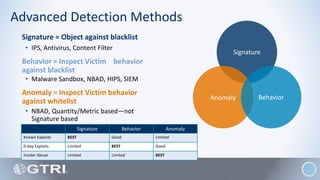
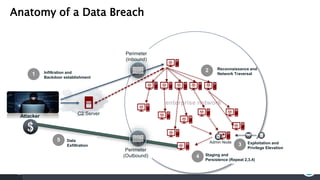
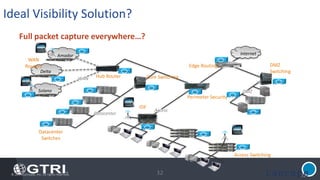
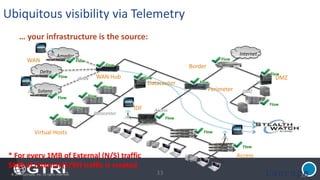
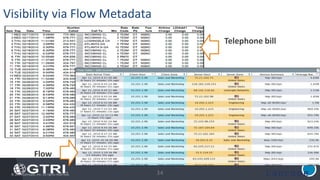
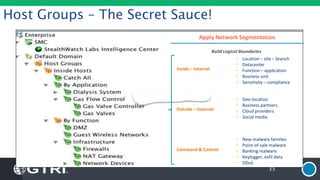
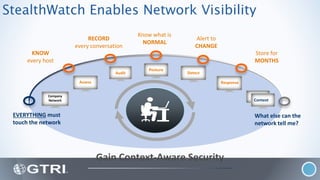
The document discusses insider threats, which are pervasive risks posed by employees or contractors that can lead to significant security breaches, with annual losses estimated at $2.9 trillion. It outlines the importance of prevention through a combination of vigilance, experienced partnerships, and advanced security capabilities. Additionally, it highlights various types of insider threats and the need for comprehensive protection measures against them.