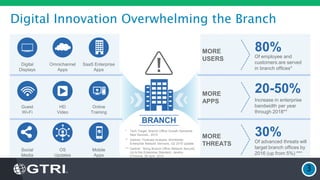
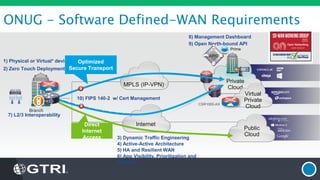
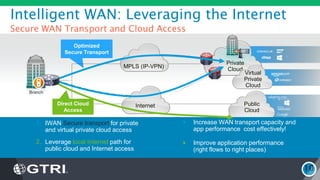
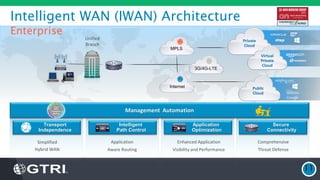
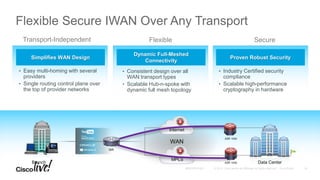
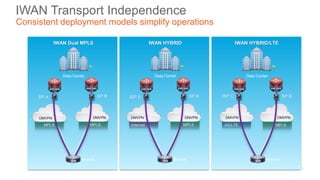
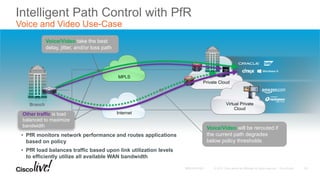
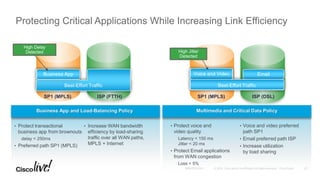
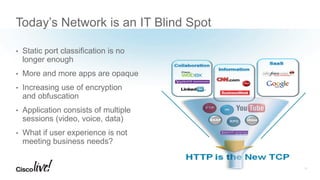
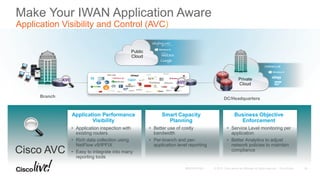
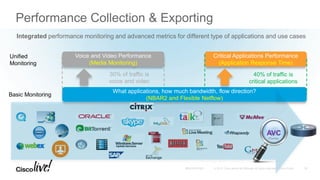
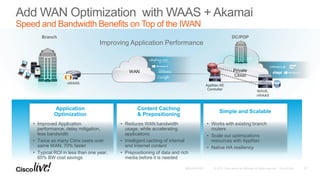
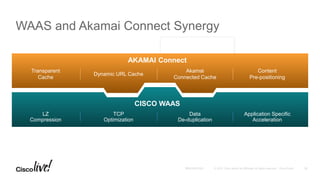
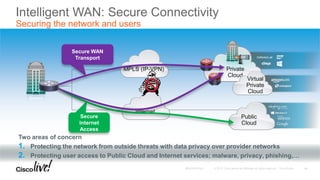
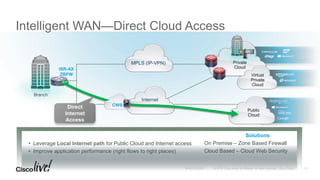
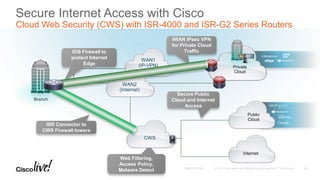
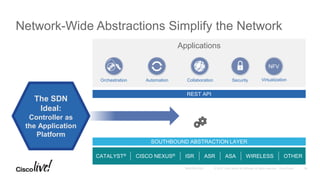
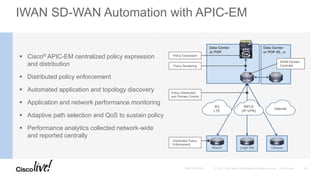
The document discusses the fundamentals of Software Defined WAN (SD-WAN) and its architecture, emphasizing transport independence, intelligent path control, application optimization, and secure connectivity. It highlights the increasing demands on branch office networks due to the rise in digital innovations and the need for effective bandwidth management and security. Additionally, it outlines Cisco's iWAN solutions, showcasing features such as deployment automation, traffic optimization, and threat defense to enhance application performance and simplify network operations.