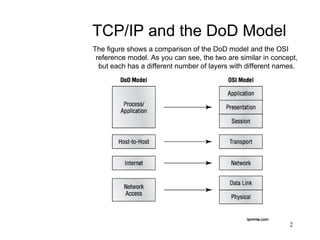
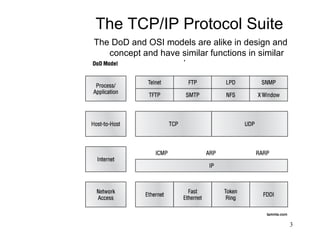
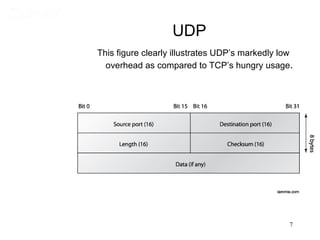
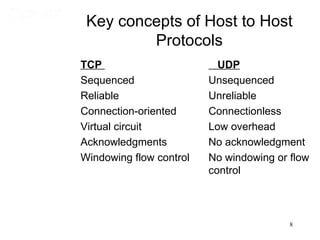
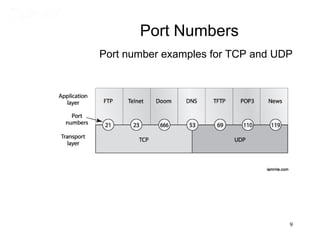
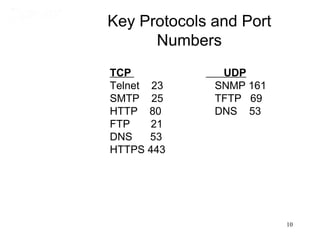
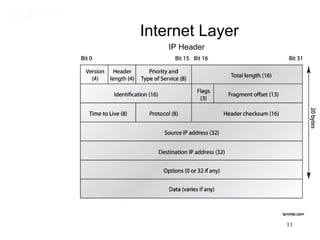
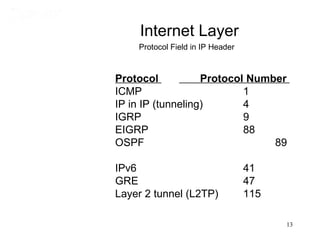
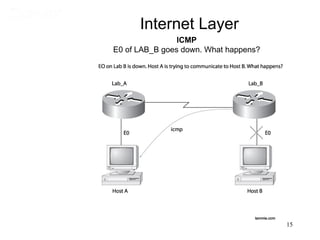
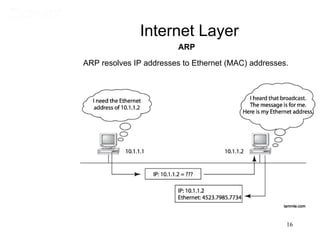
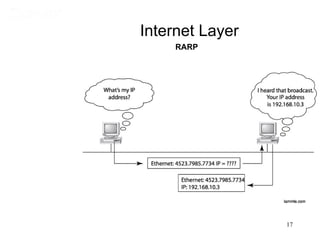
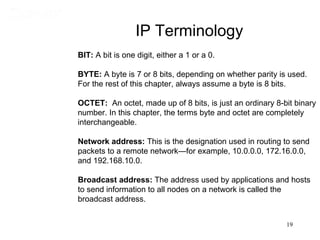
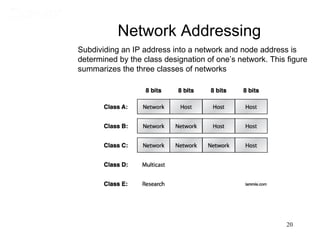
This document covers TCP/IP and IP addressing topics for a CCNA certification. It discusses the TCP/IP and DoD models, including the layers and protocols of each. It then covers IP addressing classes, private addressing, and key IP concepts like subnets, network addresses, and broadcast addresses. The document provides examples of protocols and port numbers for each layer, including application layer protocols, TCP, UDP, IP, ICMP, and ARP. It concludes with a review of written labs and questions.