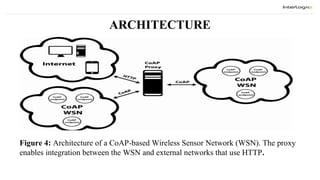
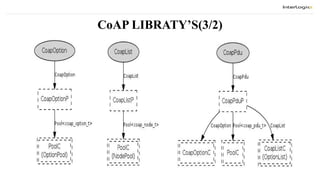
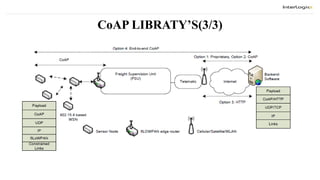
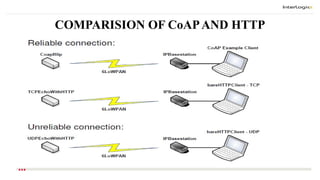
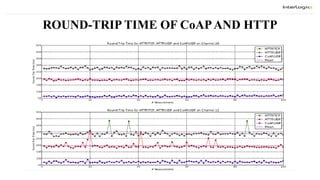
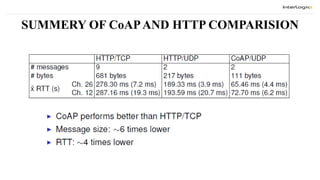
The document discusses the design and implementation of a Constrained Application Protocol (CoAP) for TinyOS, called TinyCoAP. CoAP seeks to apply HTTP's application transfer paradigm and features to constrained networks like wireless sensor networks in a simple and low overhead way. It describes CoAP's message layer for UDP transport, request/response interactions using HTTP-like methods and response codes, and reliability mechanisms. The TinyCoAP implementation in TinyOS aims to minimize resource usage with an efficient and lightweight code optimized for TinyOS. It consists of components for the CoAP conceptual layers, message handling, and client/server interactions.