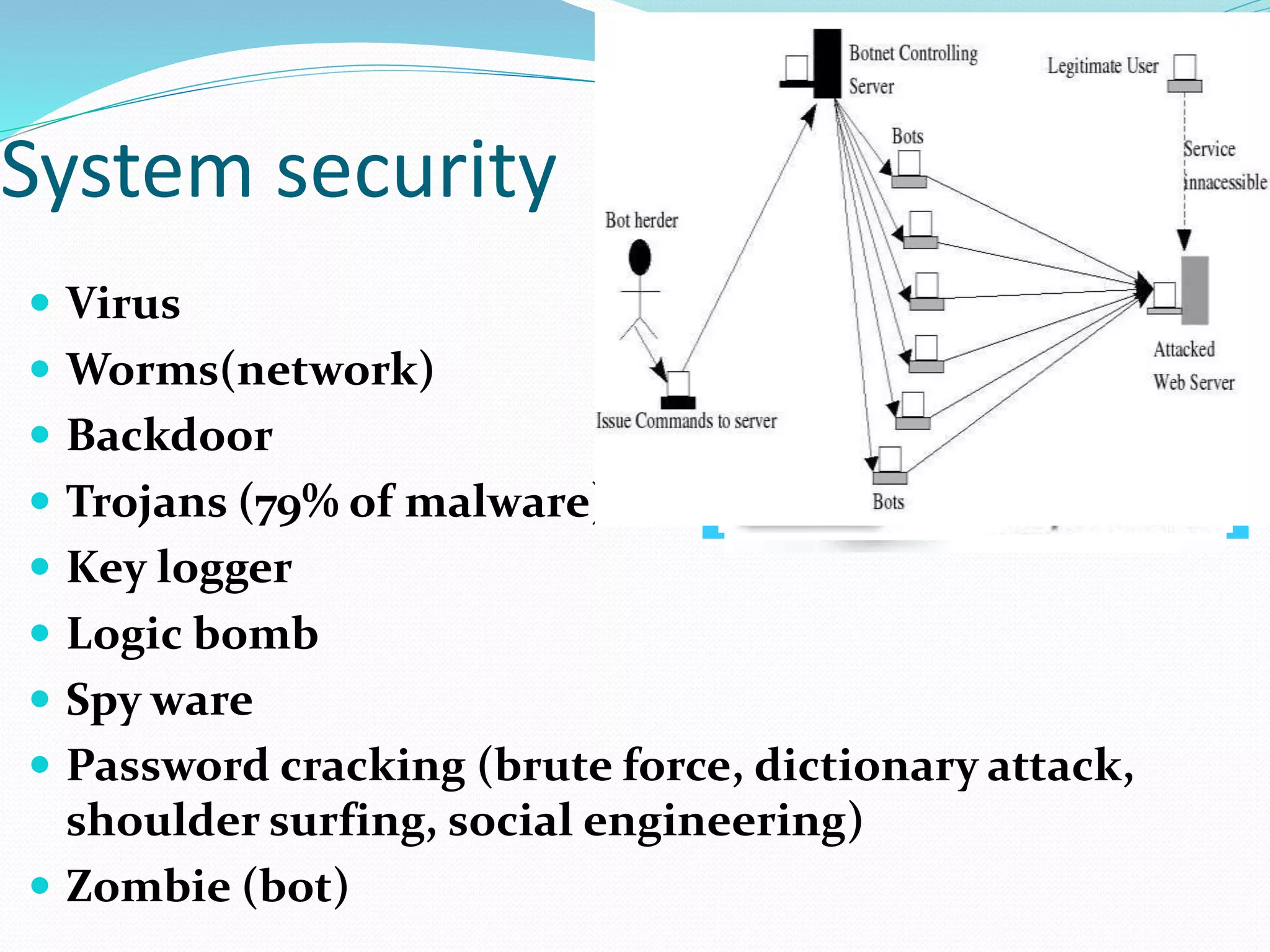
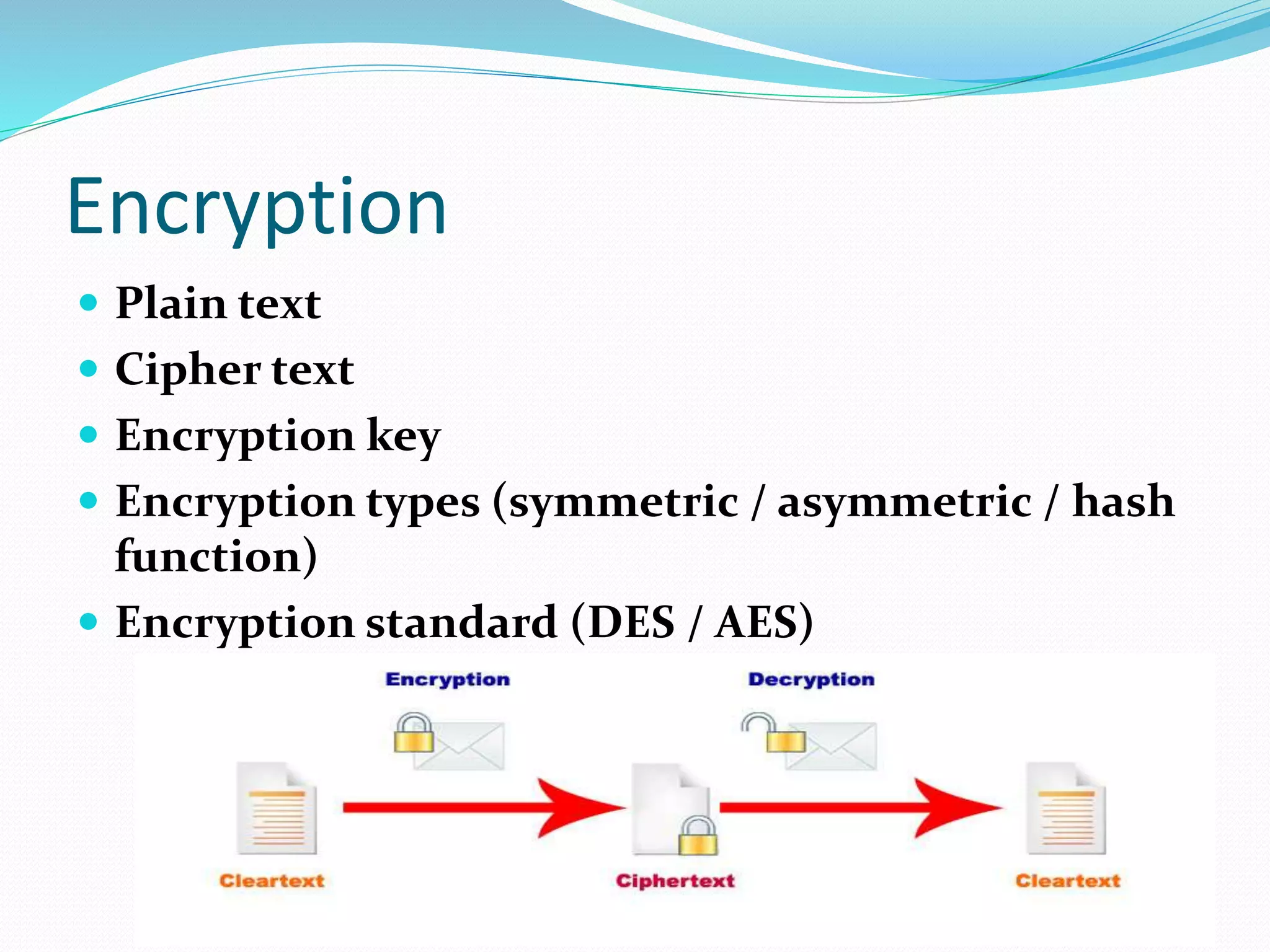
The document discusses various cybersecurity threats and issues. It notes that hacking attempts occur daily against entities like the Algerian military and that cyber attacks have targeted nuclear facilities in Iran and caused electric outages in the US. It outlines the scope of hacking, including implanted medical devices, automobiles, networks, and more. Reasons for cyber attacks include criminals seeking money or protest, and actions by governments against their own citizens. The document also covers security levels, common attacks like viruses and trojans, identity theft methods, social engineering, mobile security, and network security types such as sniffing and spoofing.