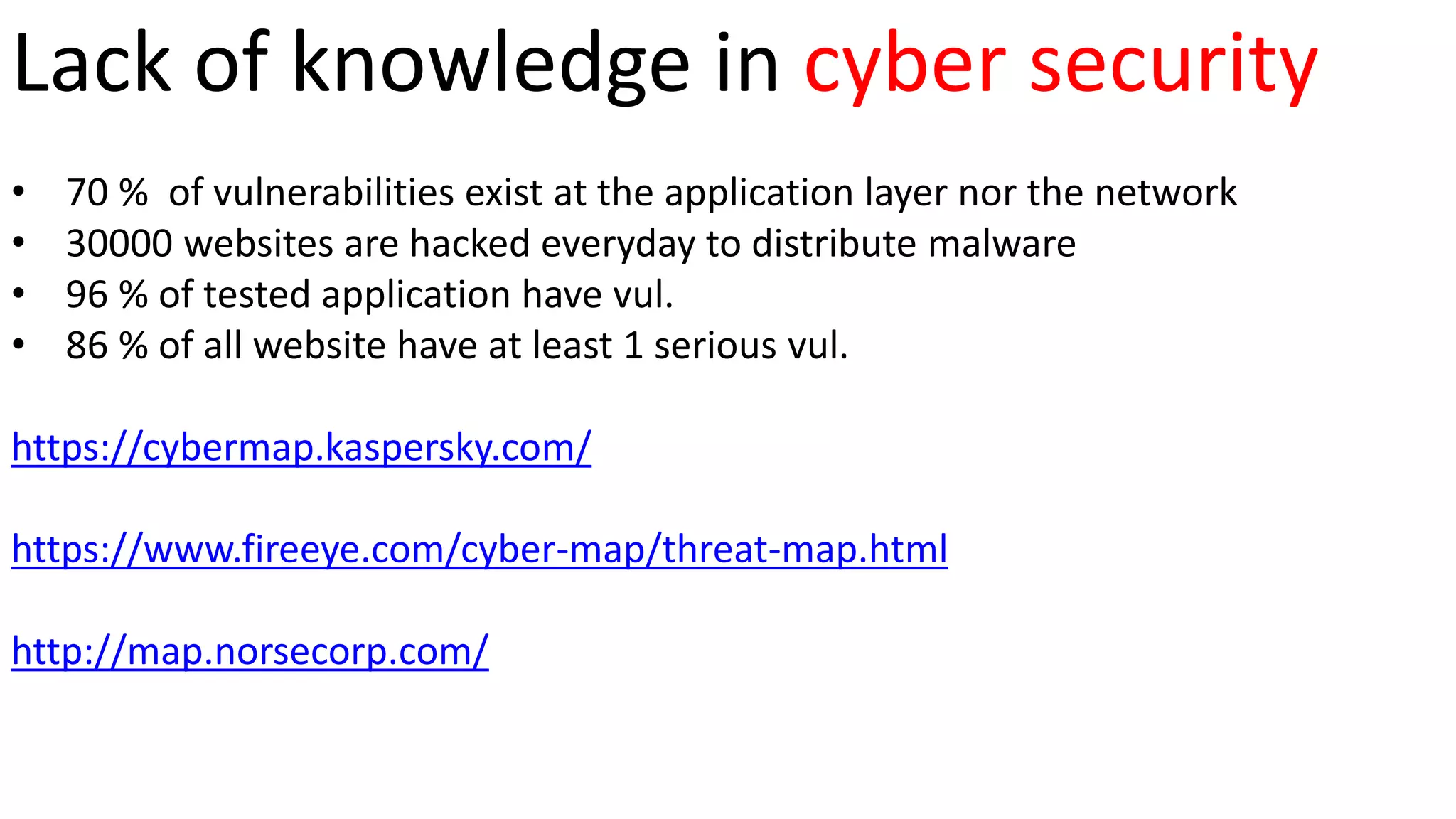
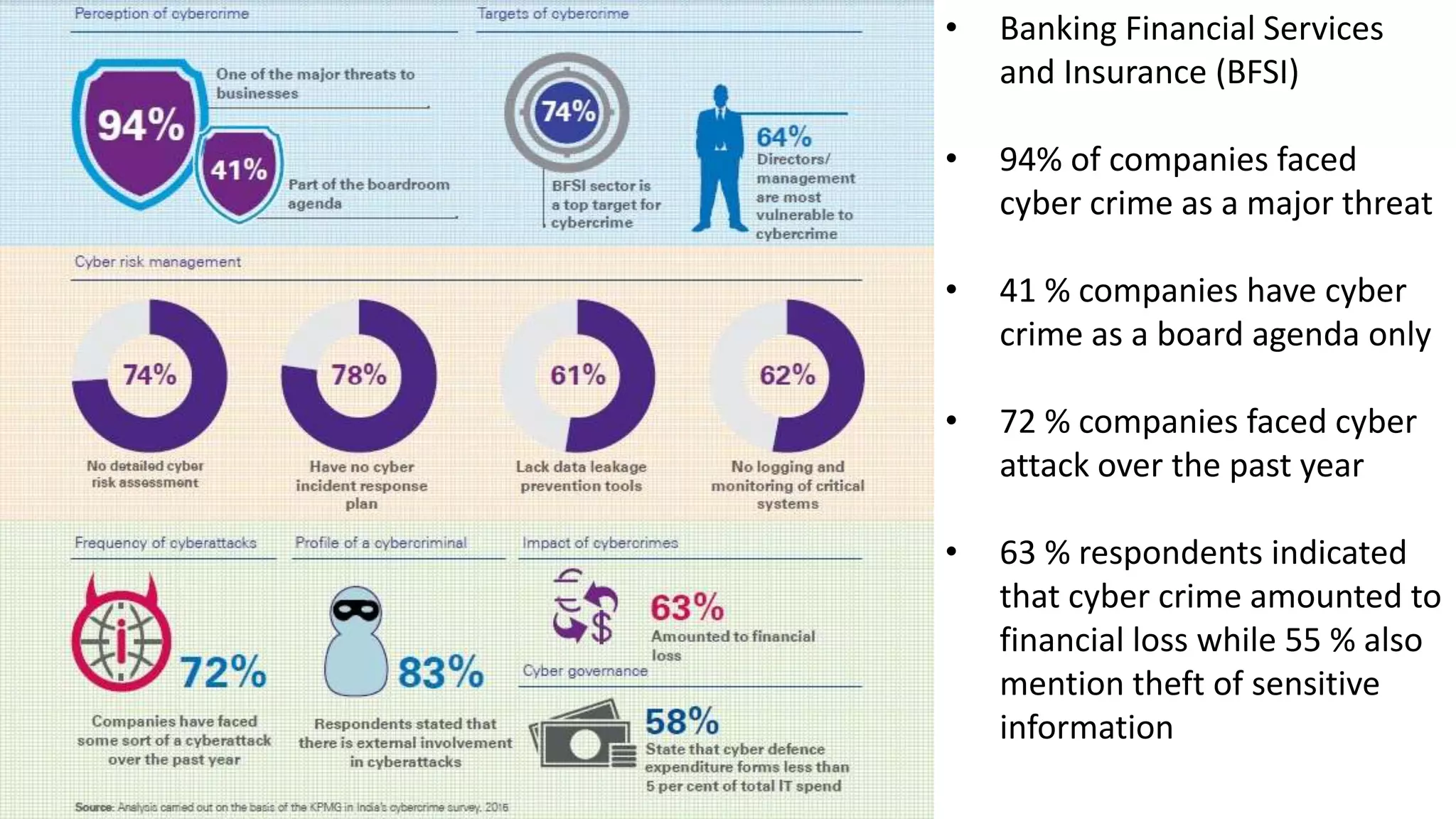
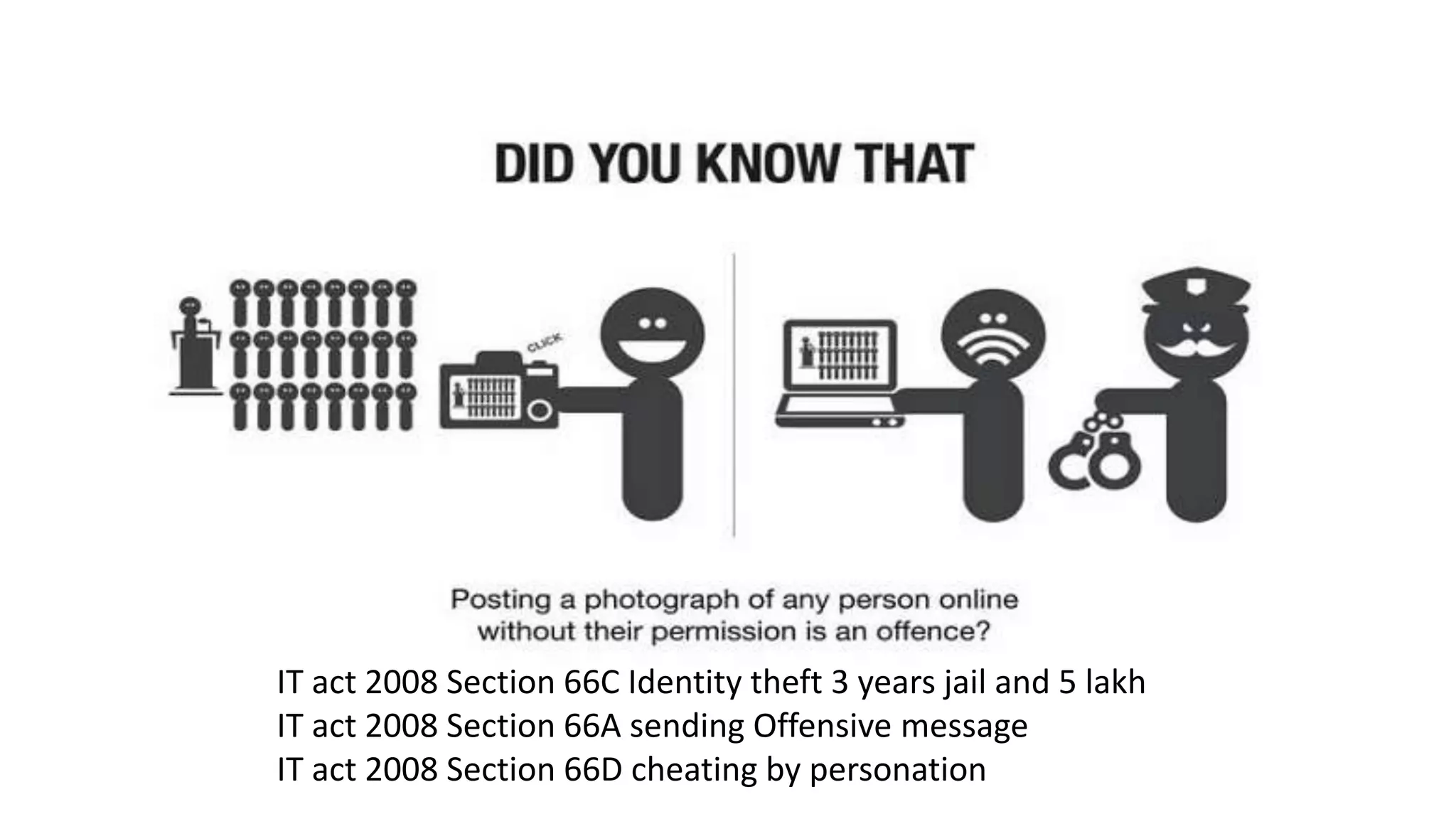
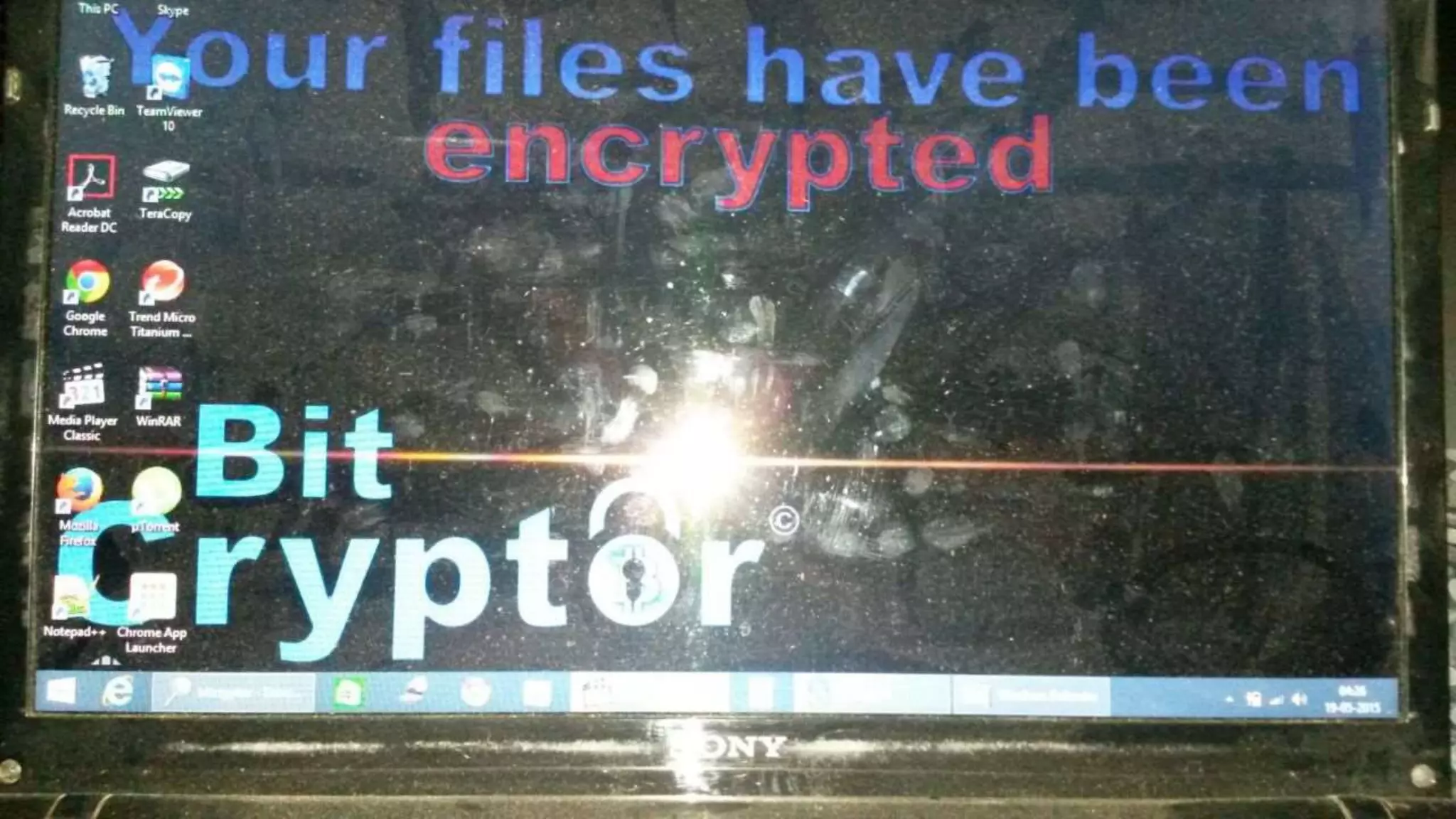
Viral Parmar is an ethical hacker, cyber security consultant, and researcher who has given seminars to over 20 colleges. He discusses cyber crime statistics showing India's high rates of attacks and vulnerabilities. He recommends protecting your identity by not sharing personal details online and using secure communication tools like VPNs, encrypted messaging apps, and verified websites. Always be cautious of downloading software from untrusted sources or clicking links in emails.