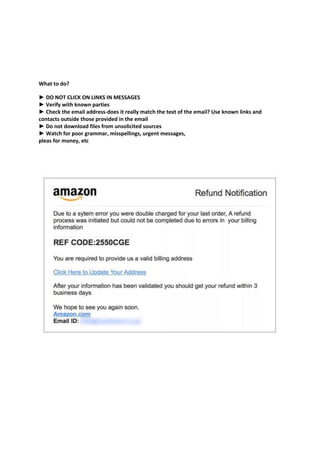
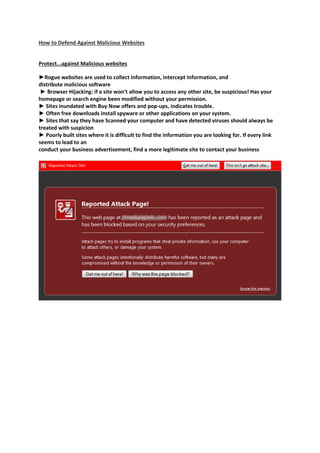
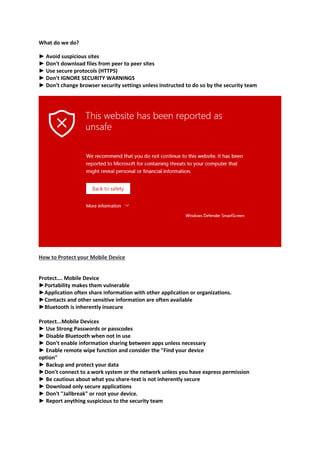
The document provides an introduction to information security and cybersecurity. It discusses the importance of protecting the confidentiality, integrity and availability of data and systems. It outlines various cyber threats such as organized crime, terrorists, foreign nations, and insiders. It provides tips for securing facilities, networks, personal information, mobile devices and general security practices. These include using strong passwords, encryption, firewalls, being wary of social engineering and phishing attempts, and reporting any potential security incidents. The overall message is the importance of protecting assets from various cyber threats through technical and physical security measures.