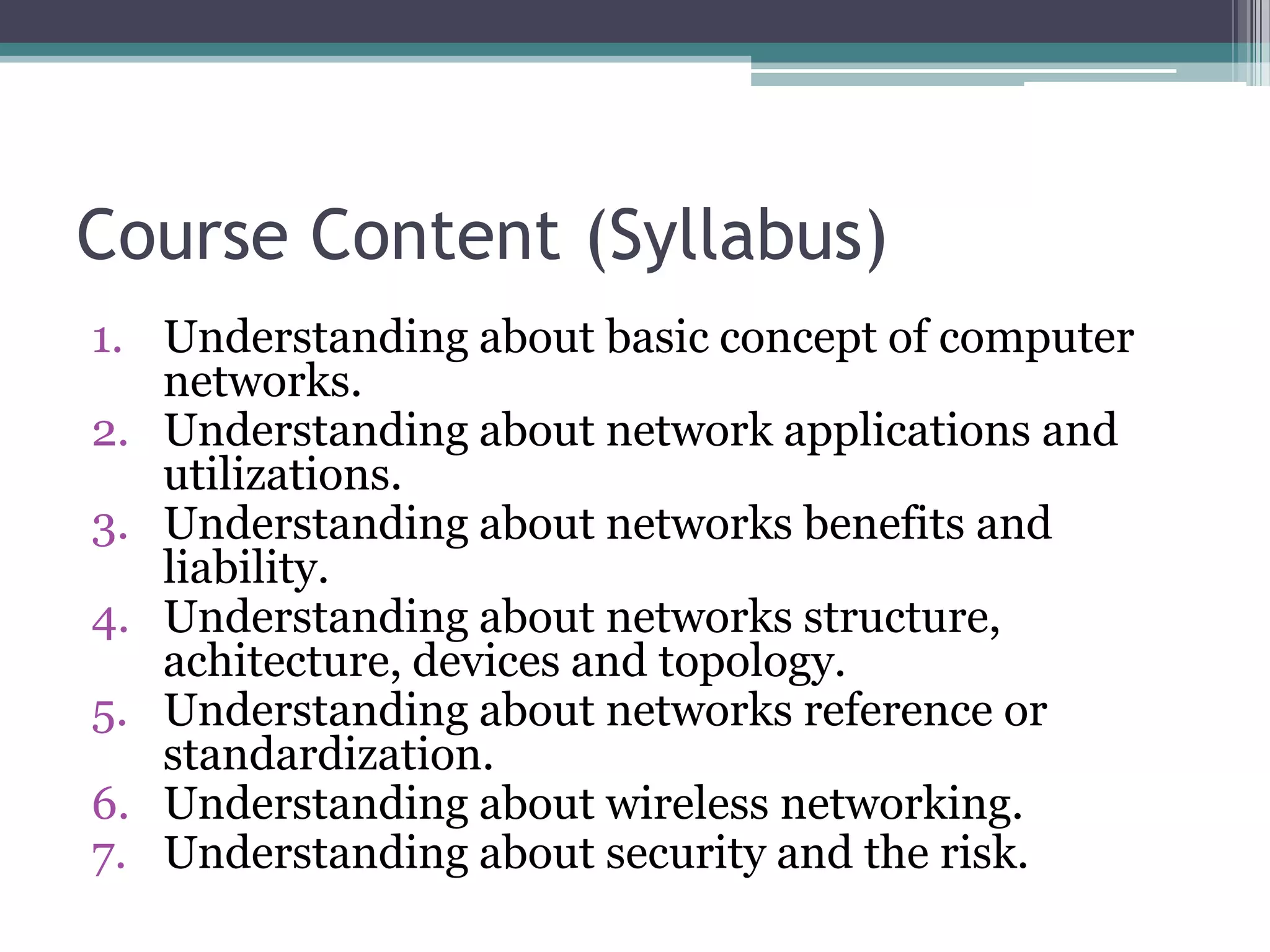
This document provides an overview of the syllabus for a basic computer networks course. The syllabus covers 7 topics: 1) basic network concepts, 2) network applications and uses, 3) network benefits and risks, 4) network structure, architecture, devices and topologies, 5) network standards and reference models, 6) wireless networking, and 7) network security and risks. The course will use two textbooks as references and student performance will be evaluated based on a midterm exam, final exam, individual and group assignments, and potential projects.