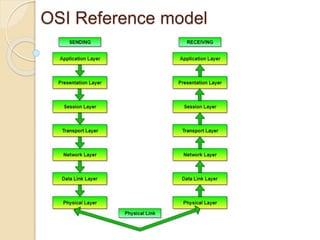
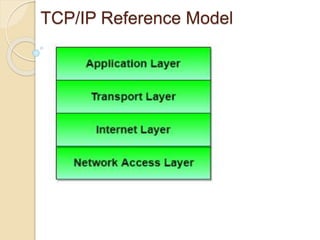
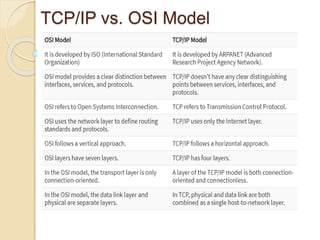
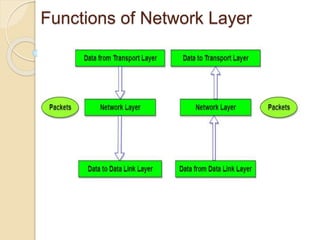
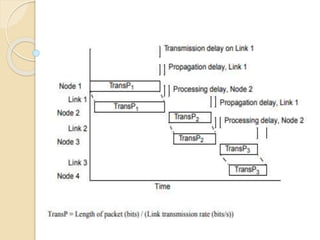
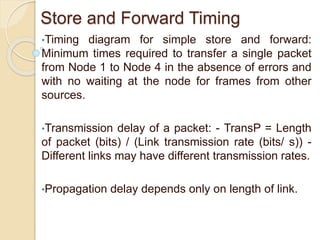
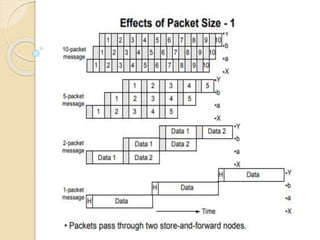
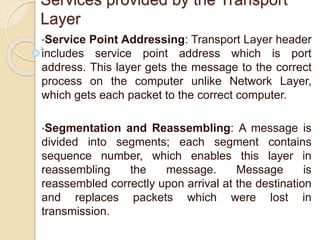
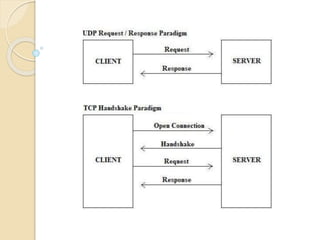
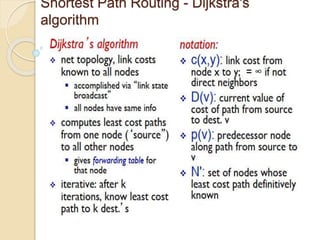
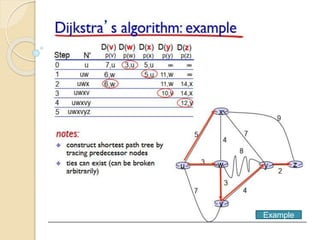
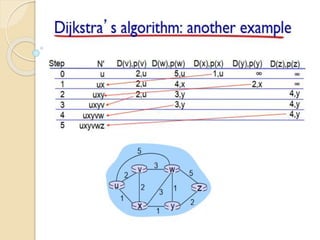
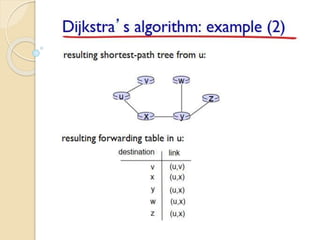
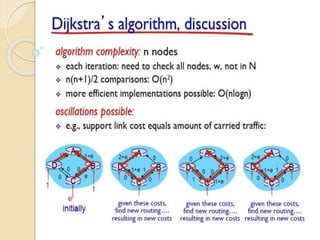
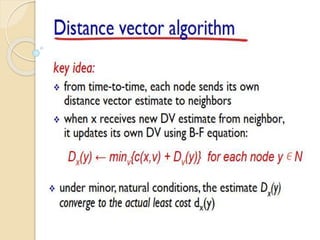
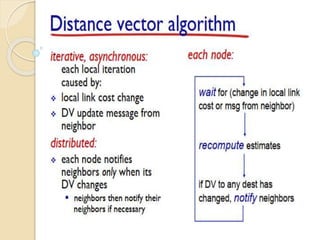
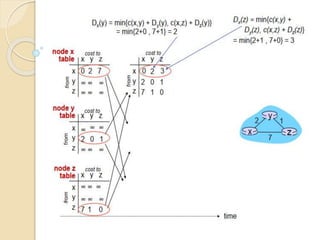
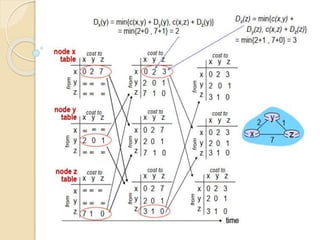
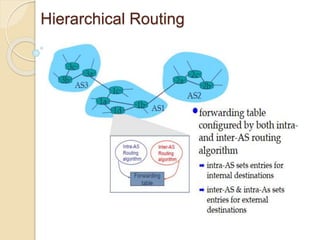
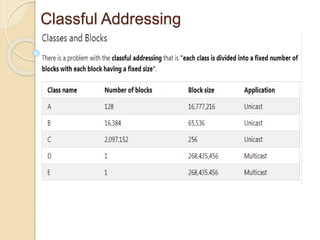
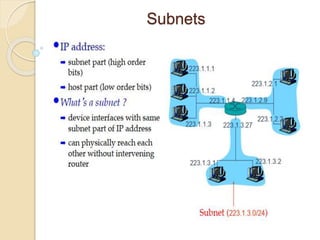
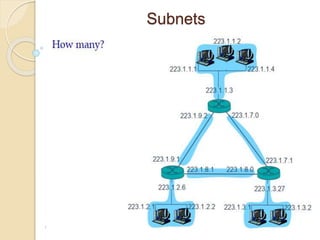
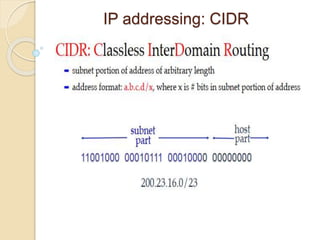
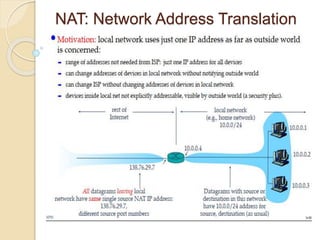
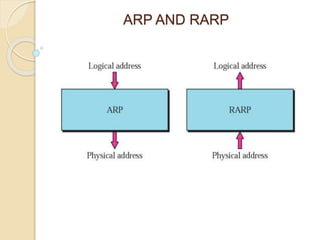
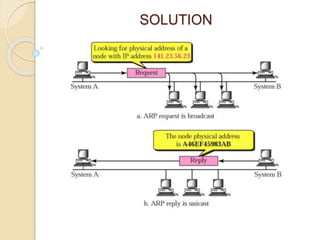
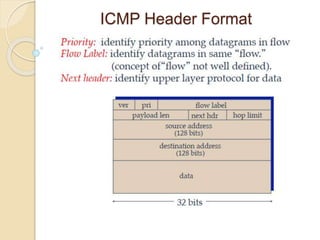
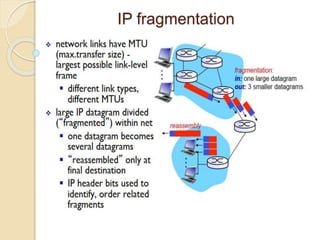
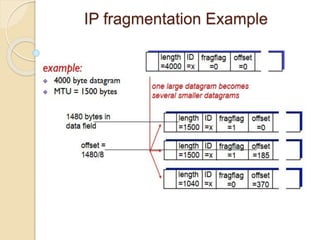
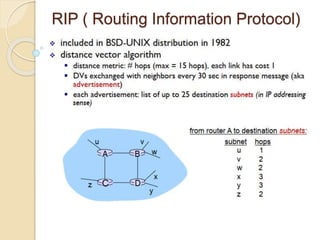
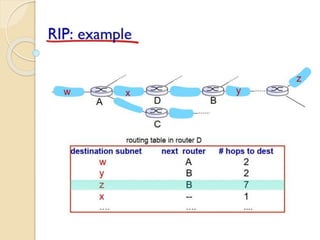
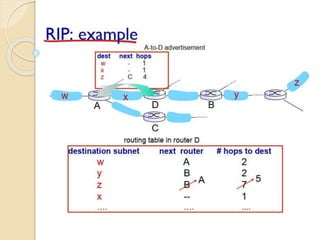
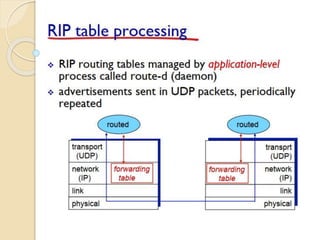
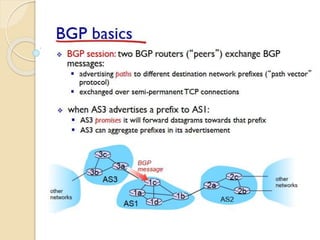
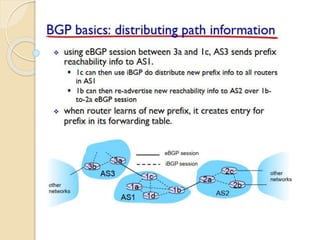
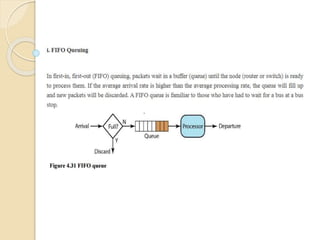
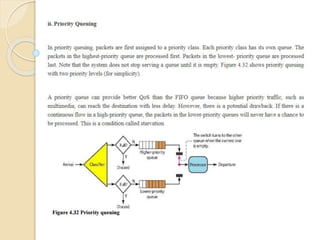
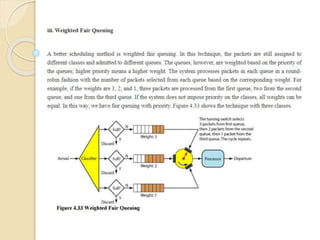
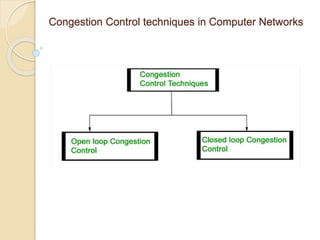
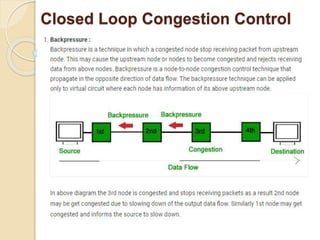
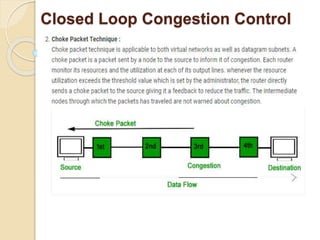
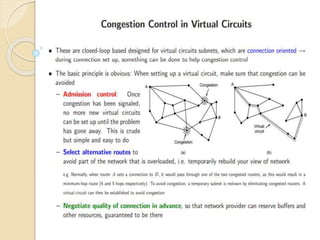
The document discusses several topics related to computer network models and protocols. It describes the OSI model which consists of seven layers and was developed by ISO to ensure worldwide data communication. It also discusses the TCP/IP model. The network layer is described in detail, covering functions like routing packets between networks and logical to physical address translation. Store-and-forward packet switching is explained. The transport layer provides services like port addressing, segmentation and reassembly, and connection-oriented and connectionless transmission. IP addressing schemes like classful and classless are summarized. Network protocols such as ARP, DHCP, ICMP, and RIP are also mentioned briefly.