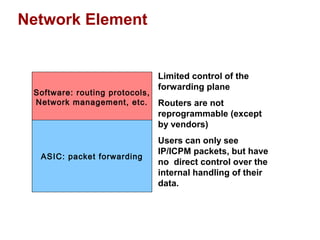
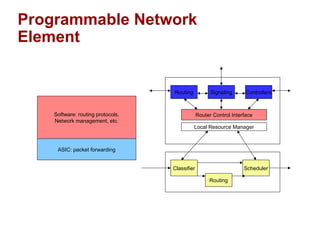
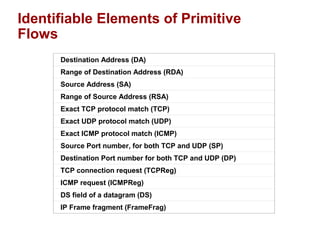
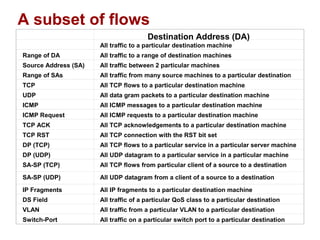
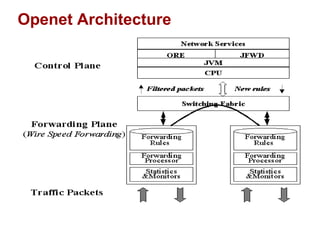
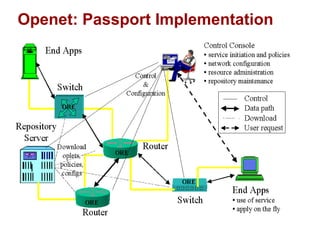
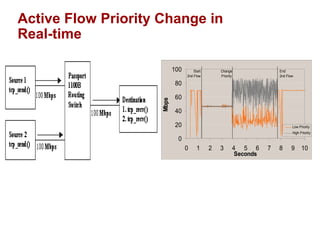
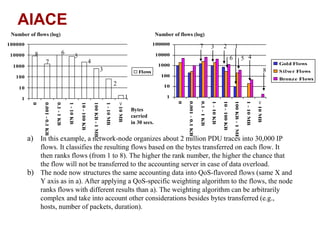
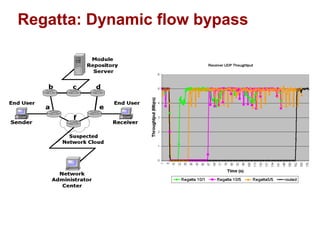
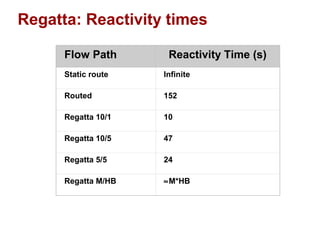
The document discusses intelligent network services through active flow manipulation (AFM) to enhance programmability and control in network devices. It outlines the limitations of current network elements and introduces a framework for dynamic service introduction and real-time traffic management. Key benefits of AFM include improved response to traffic changes and the ability to enhance router functionality via collaborative control elements.