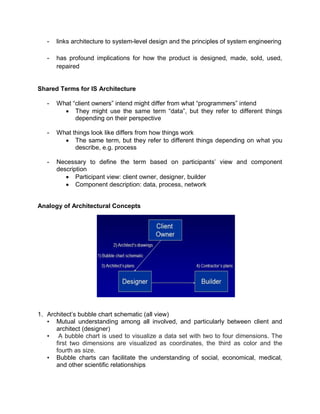
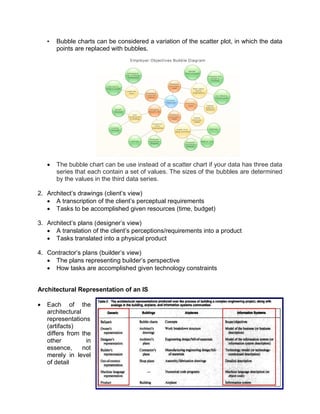
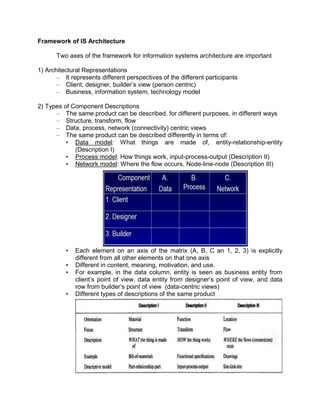
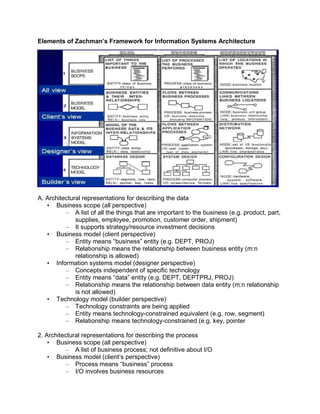
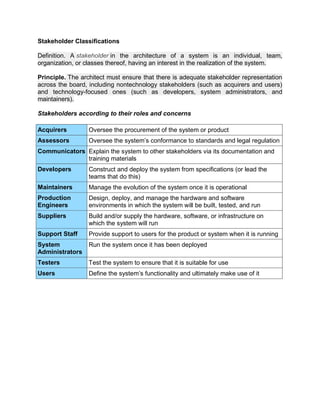
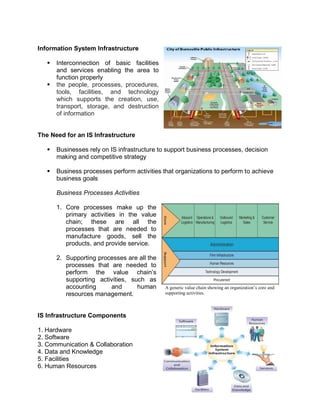
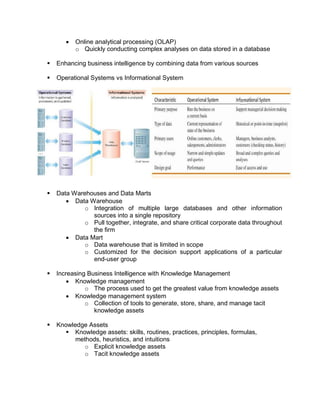
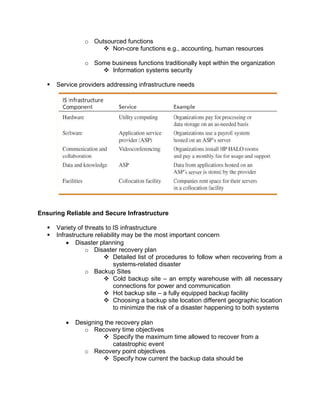
The document outlines the distinctions between information system architecture and infrastructure, detailing the components, layers, and stakeholder roles involved in managing these systems. It emphasizes the importance of effective information architecture in enhancing business processes and decision-making, while also discussing strategies for managing various infrastructures, including hardware, software, communication, data, and human resources. Additionally, it addresses the need for reliability, security, and adaptability in these infrastructures to support organizational goals.