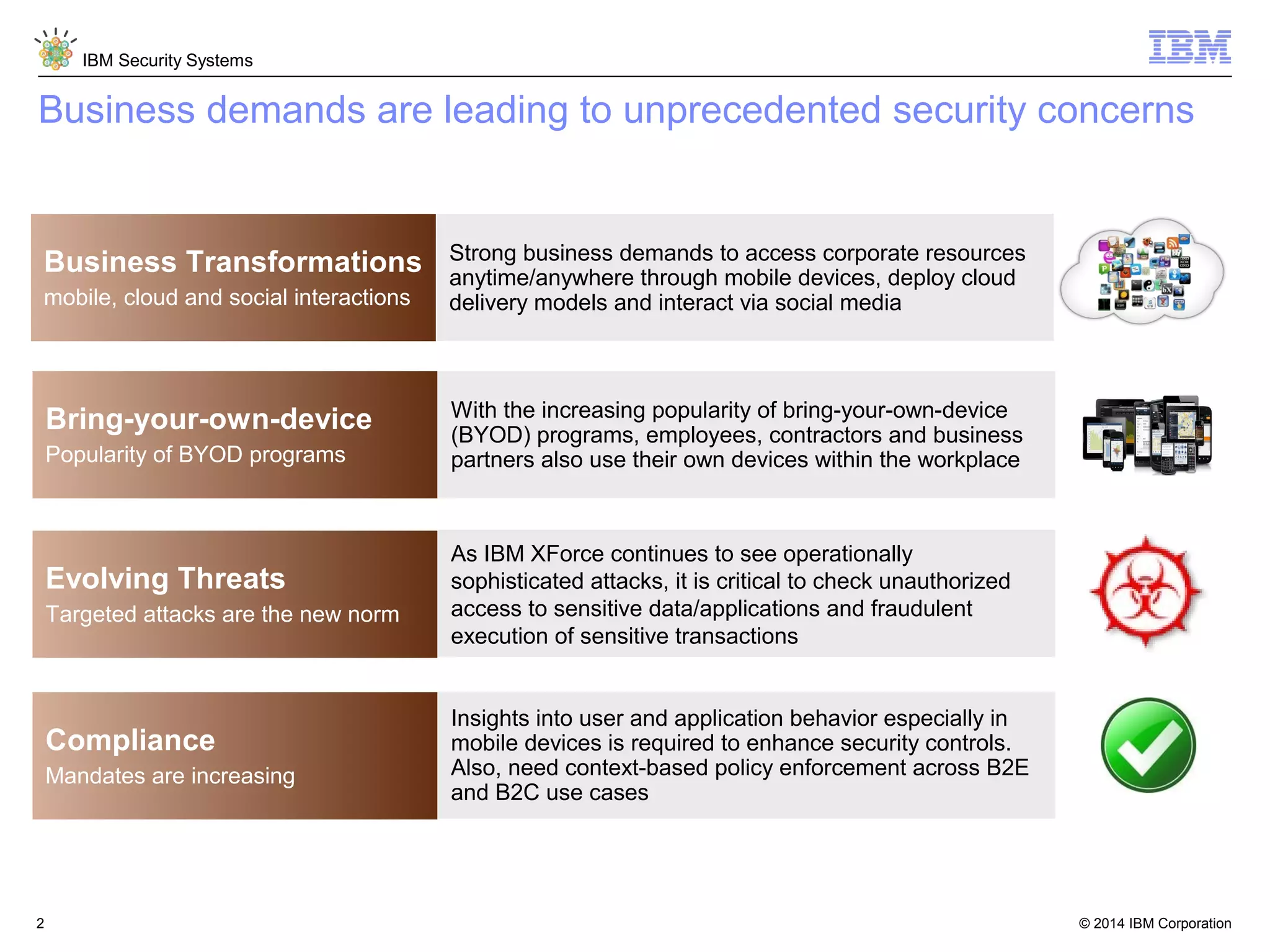
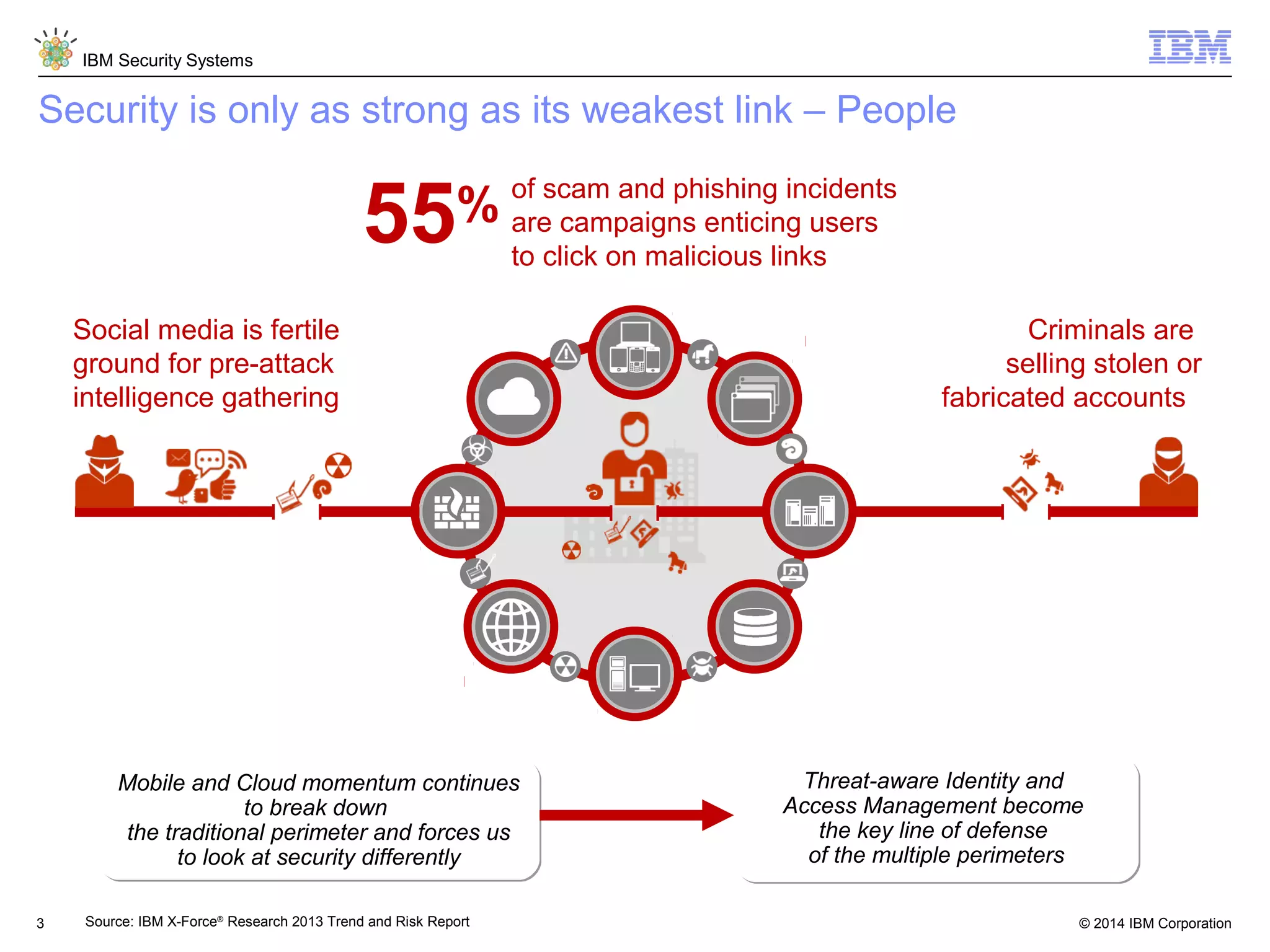
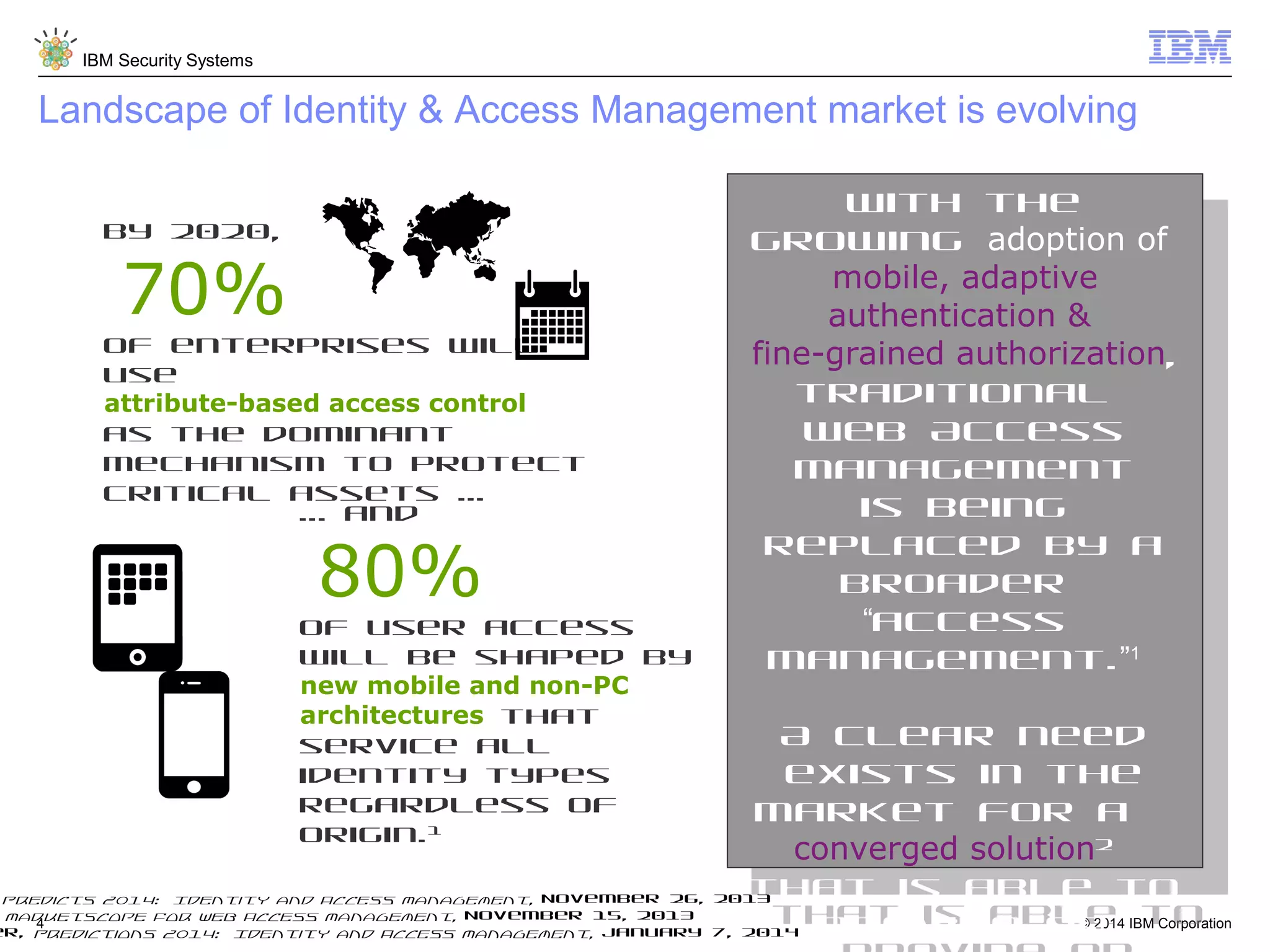
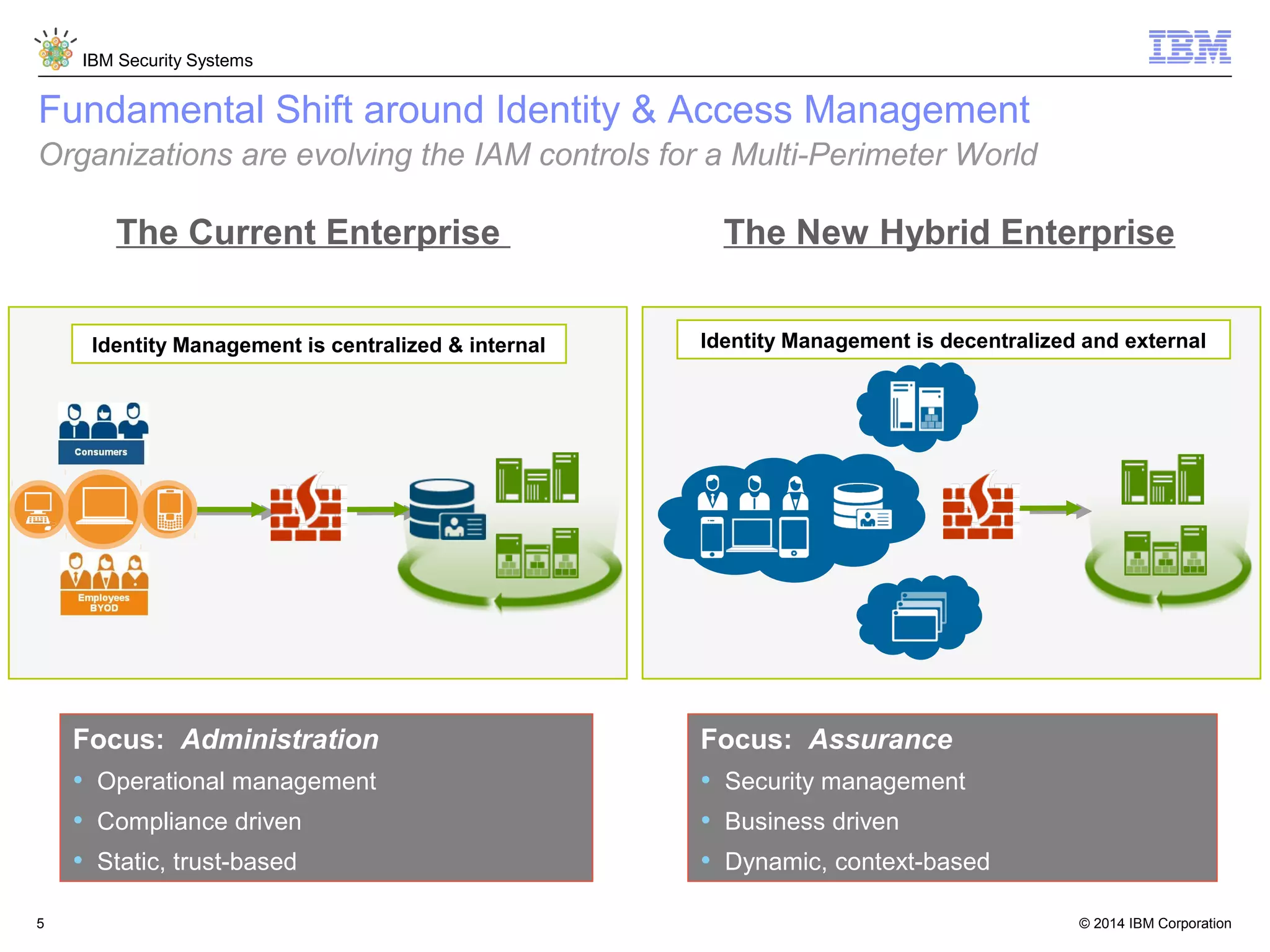
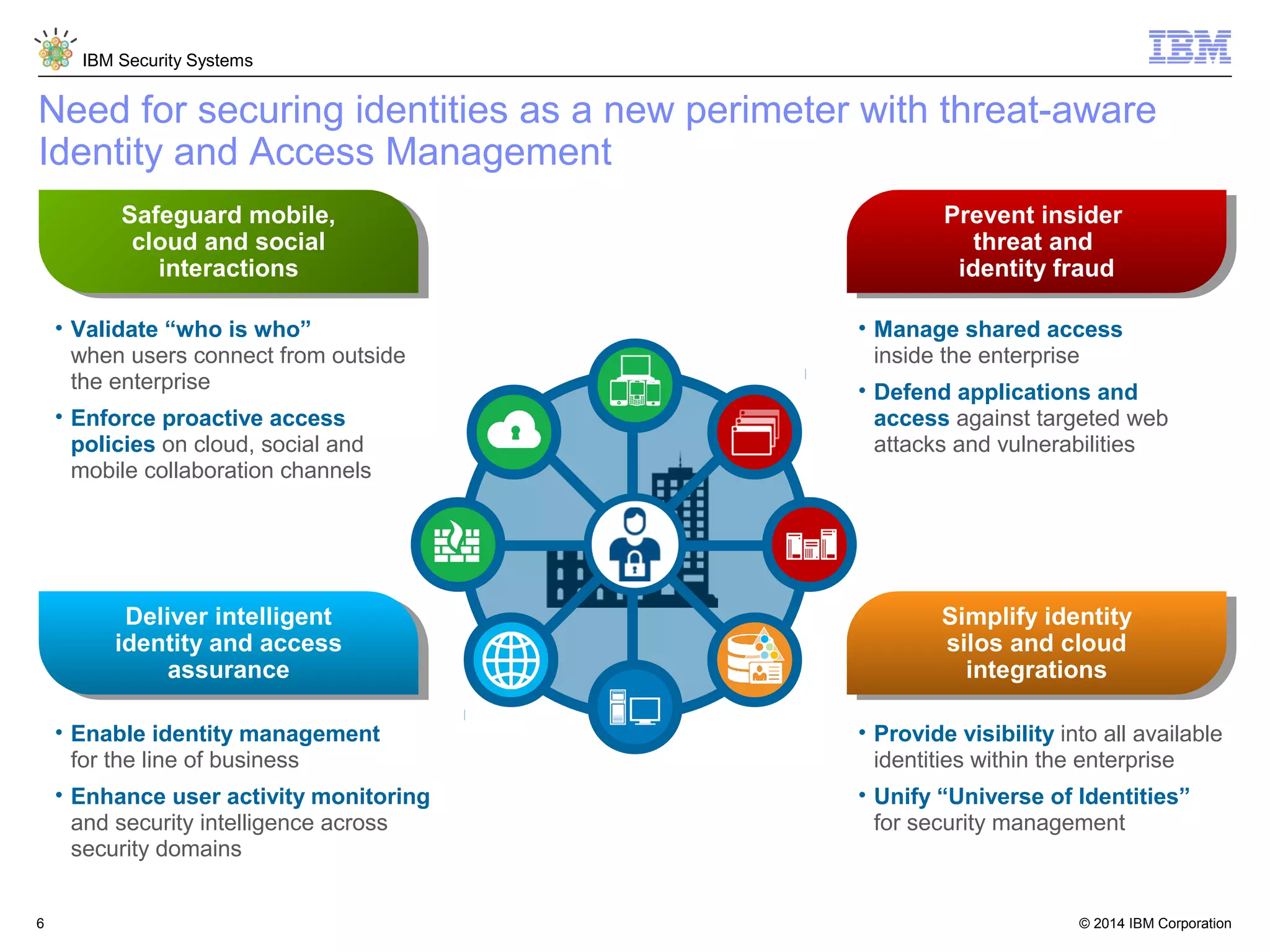
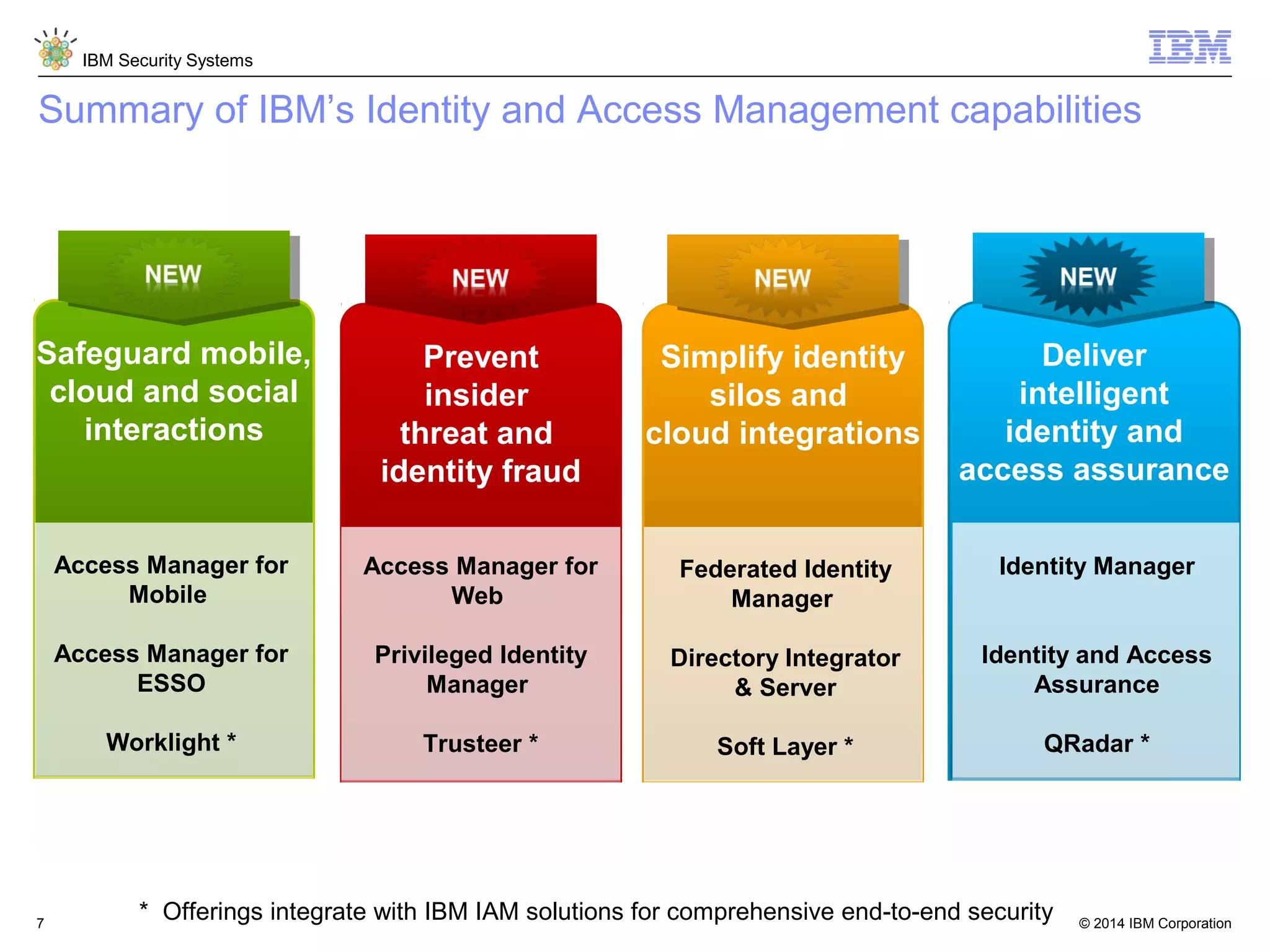
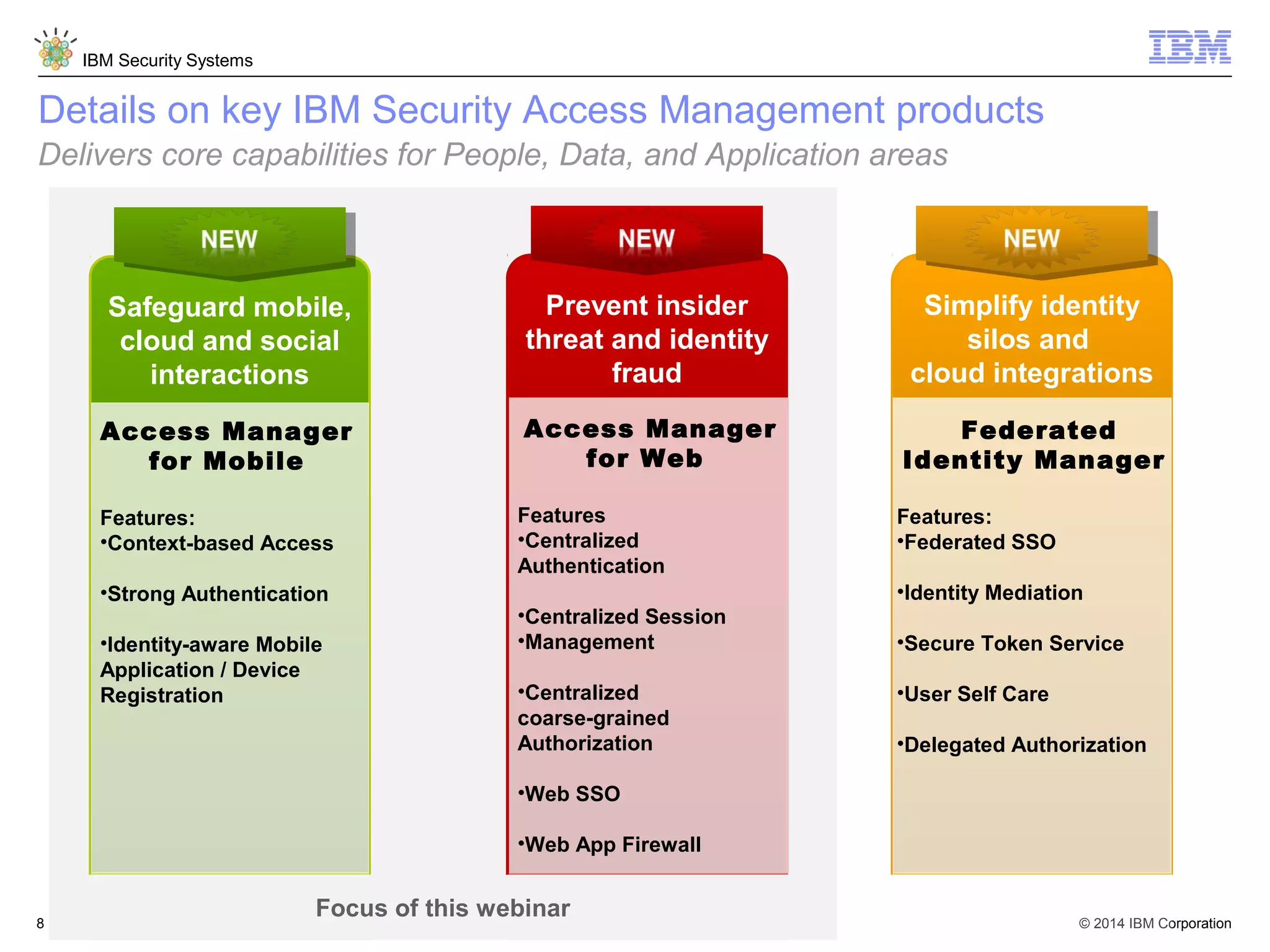
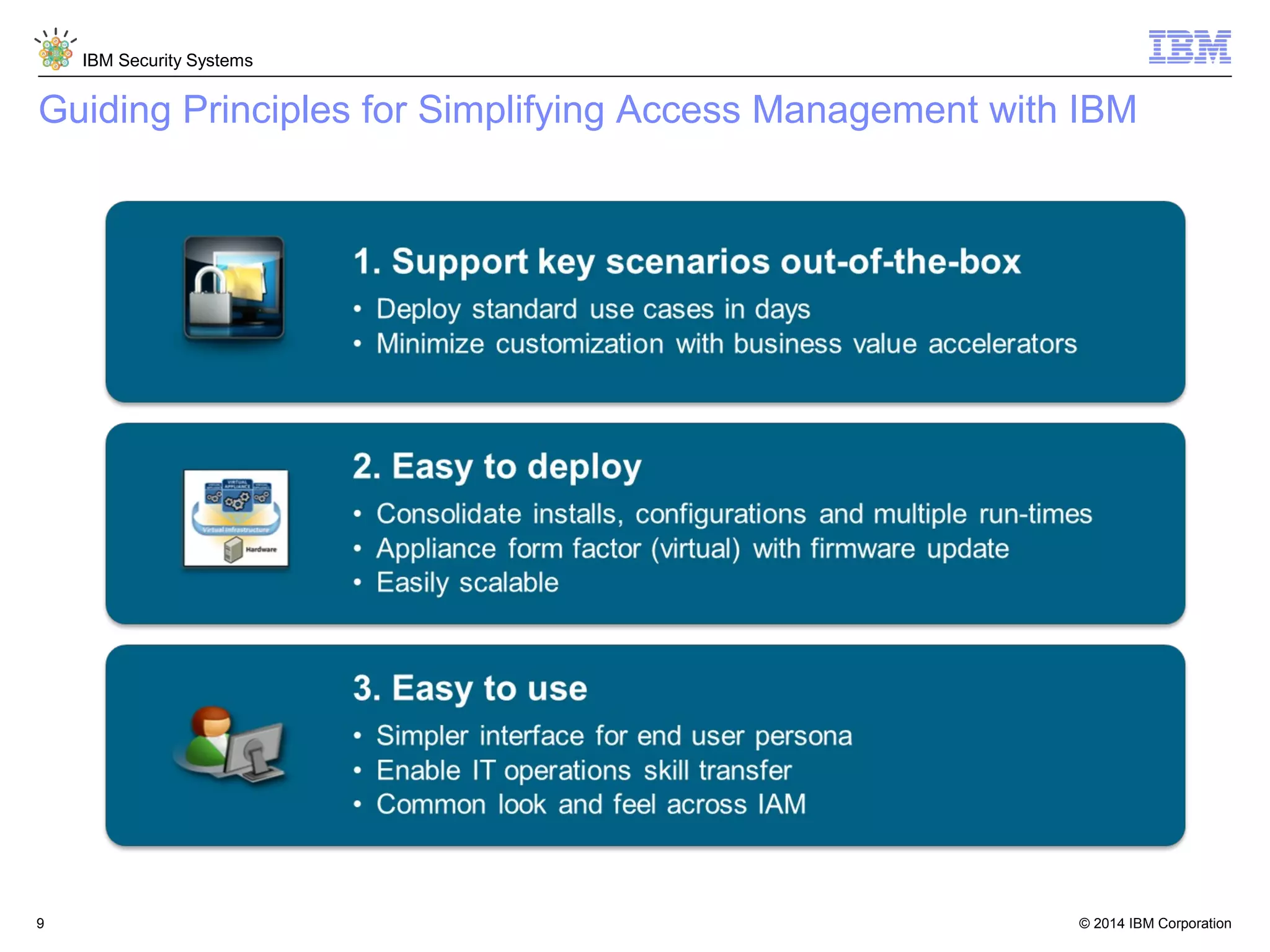
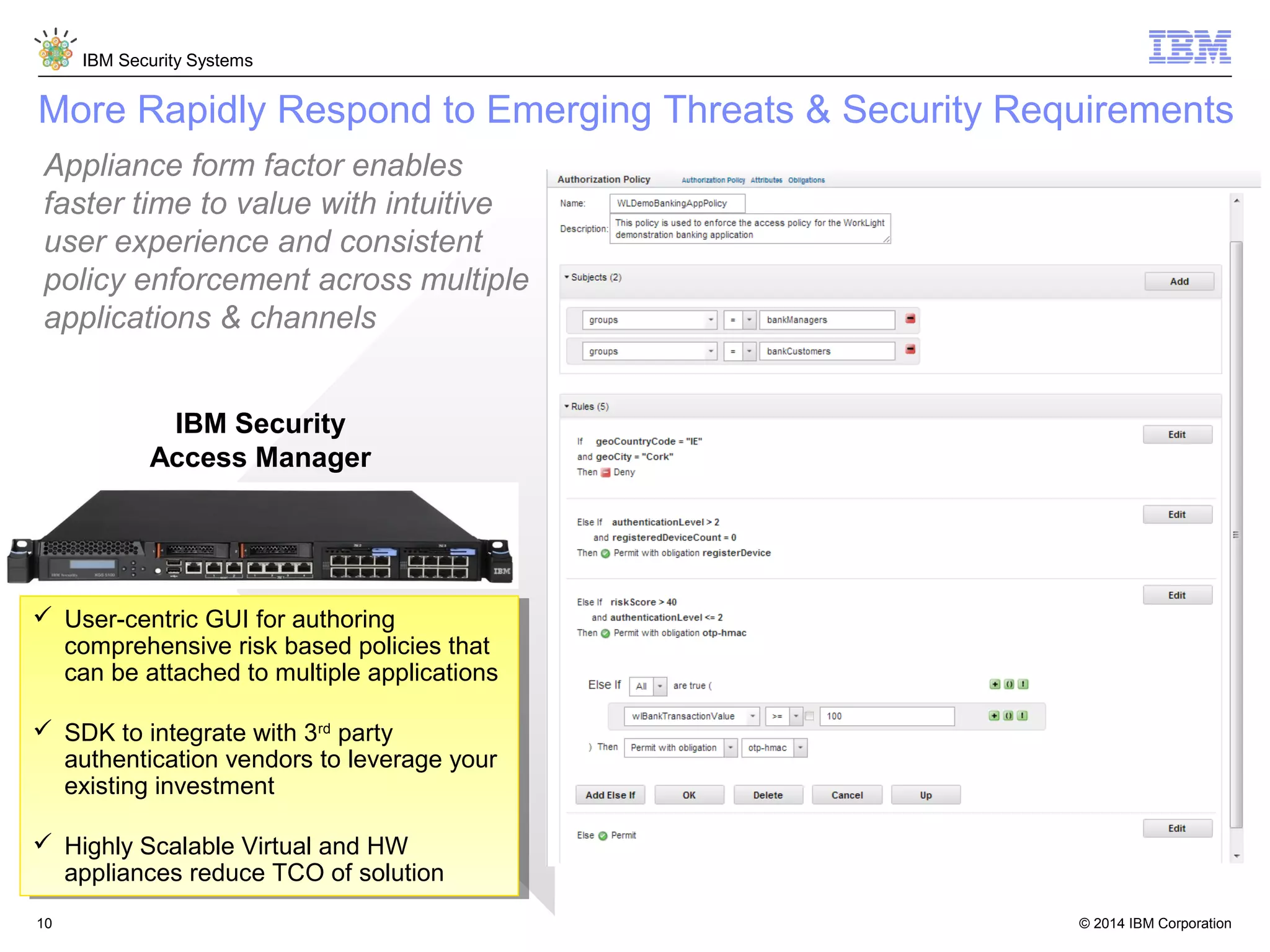
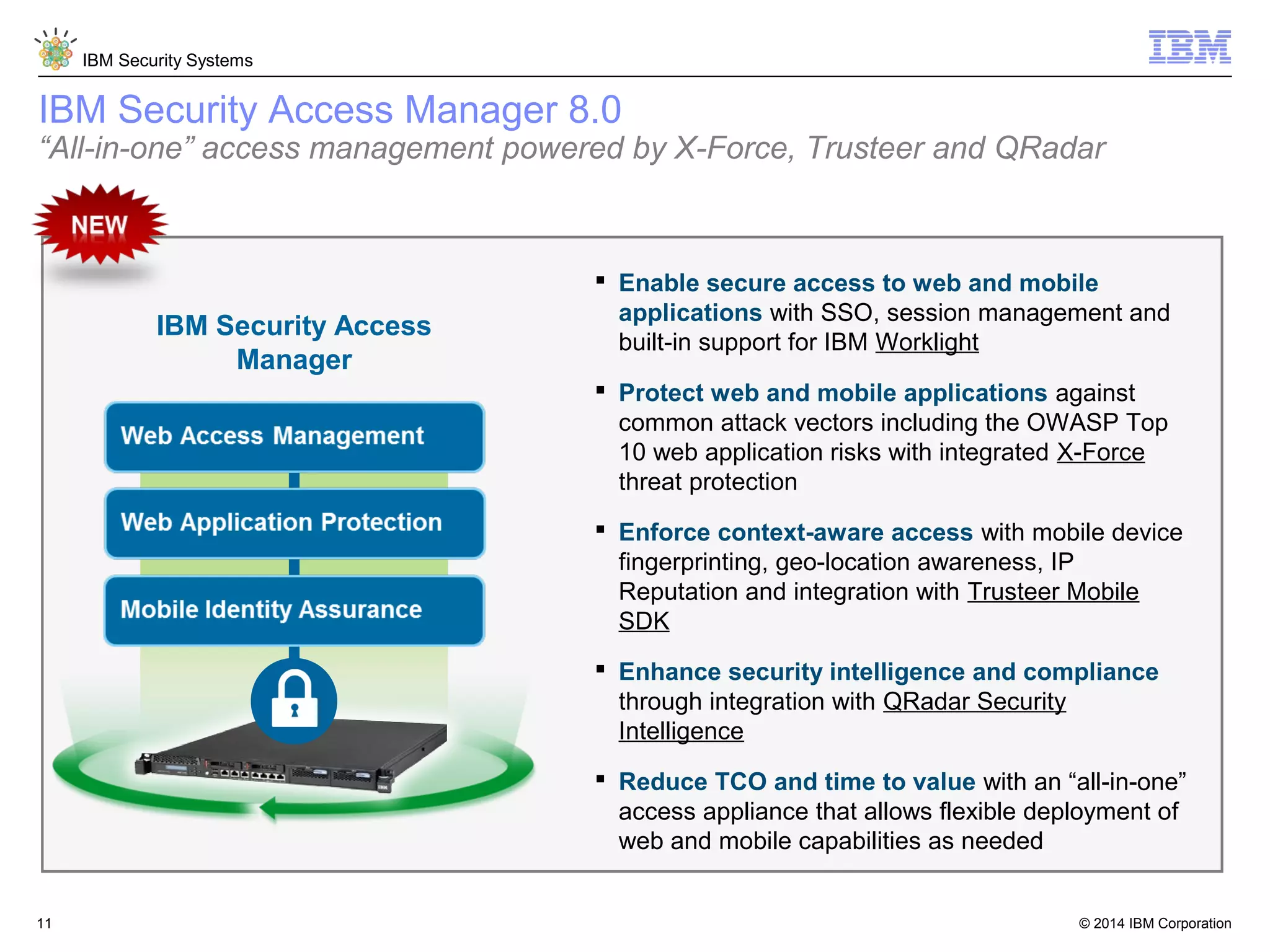
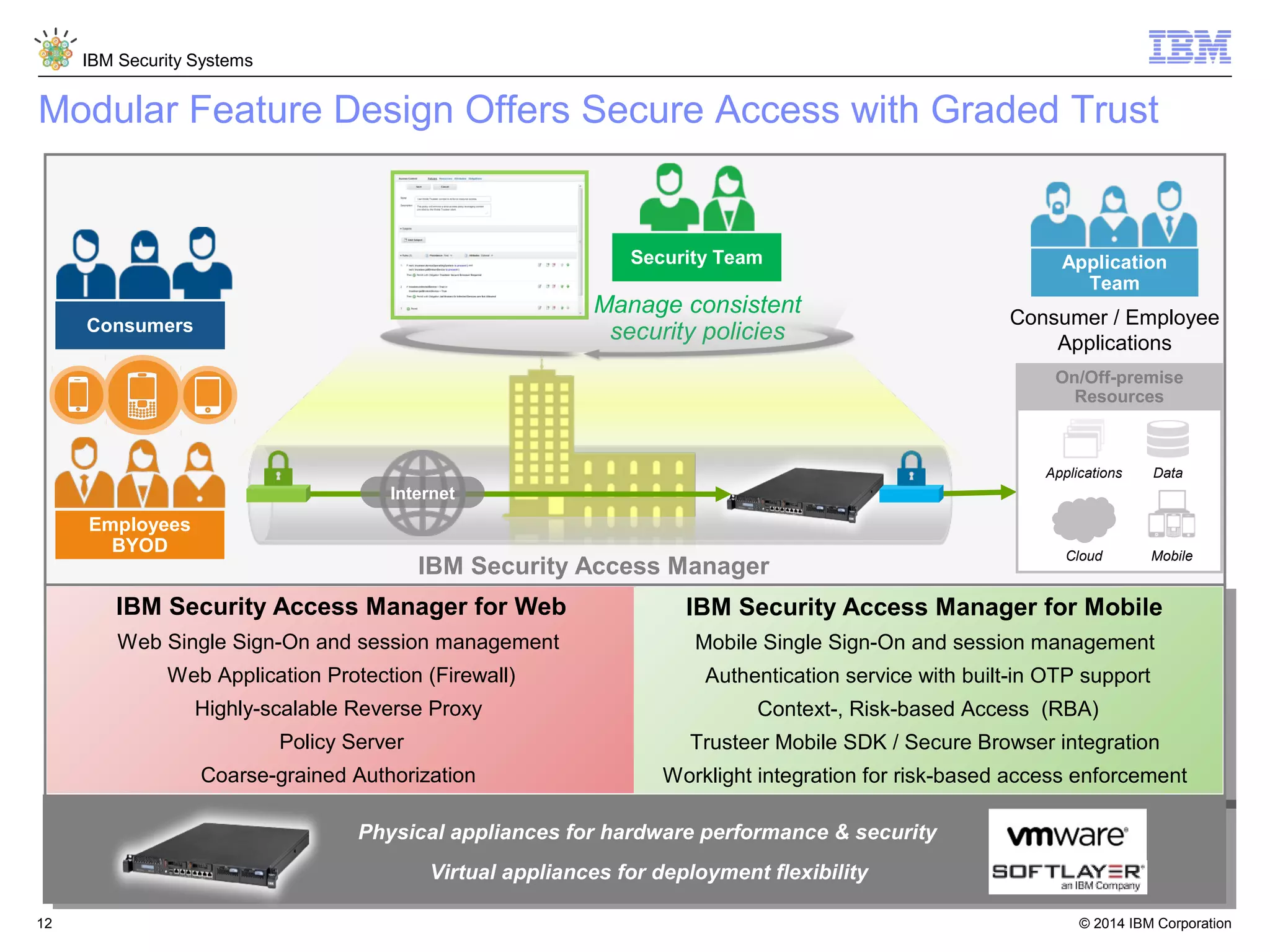
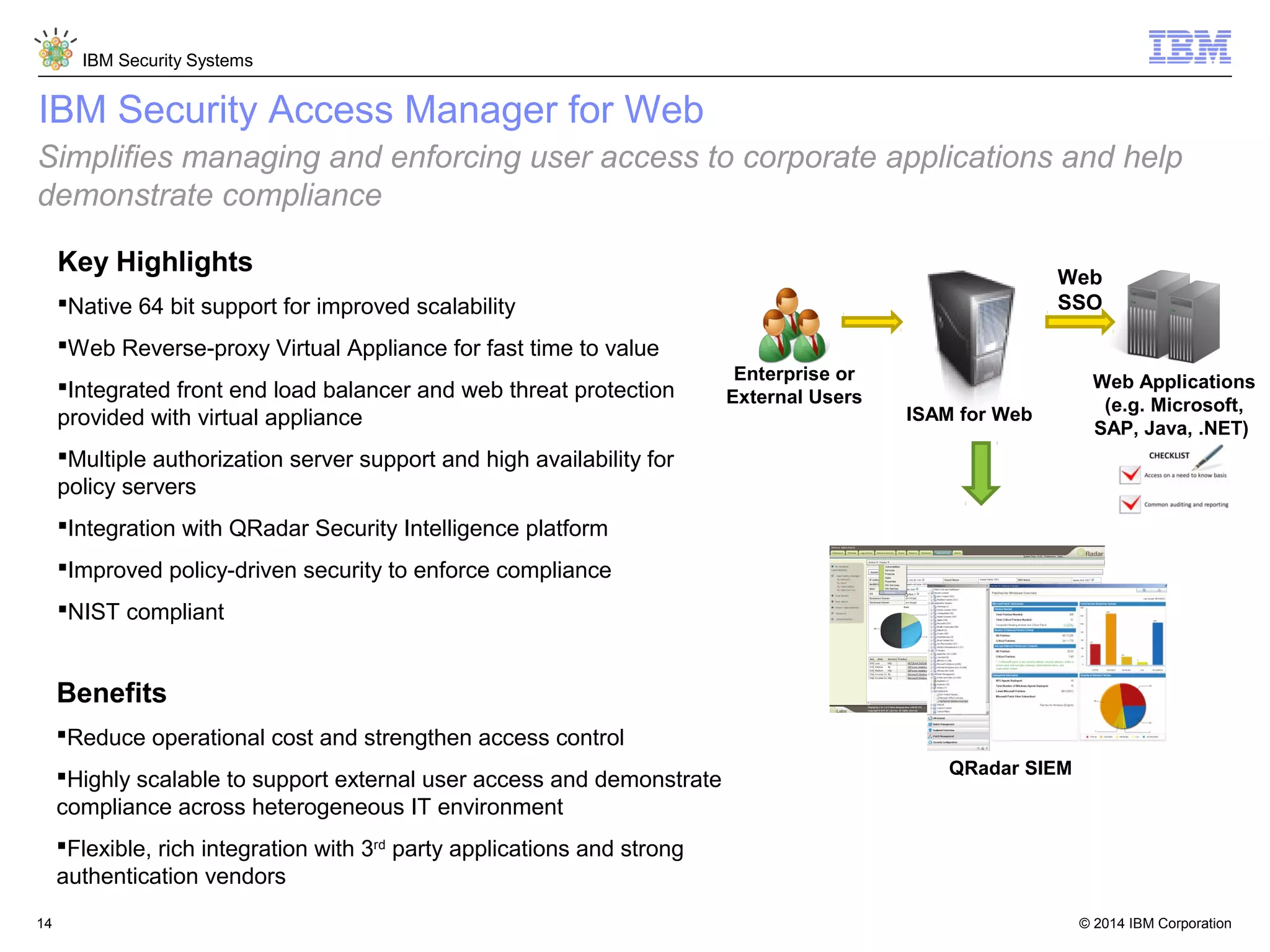
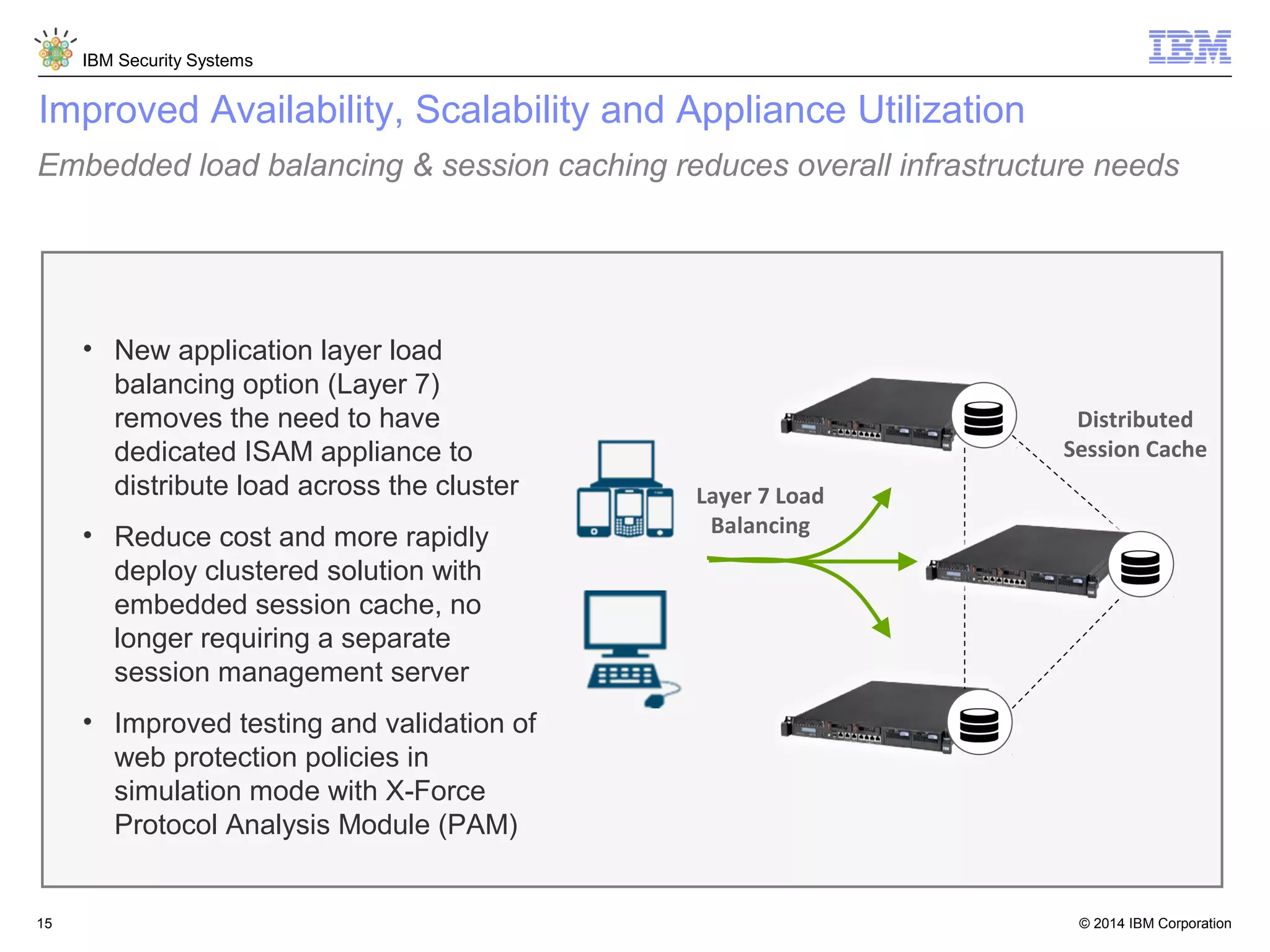
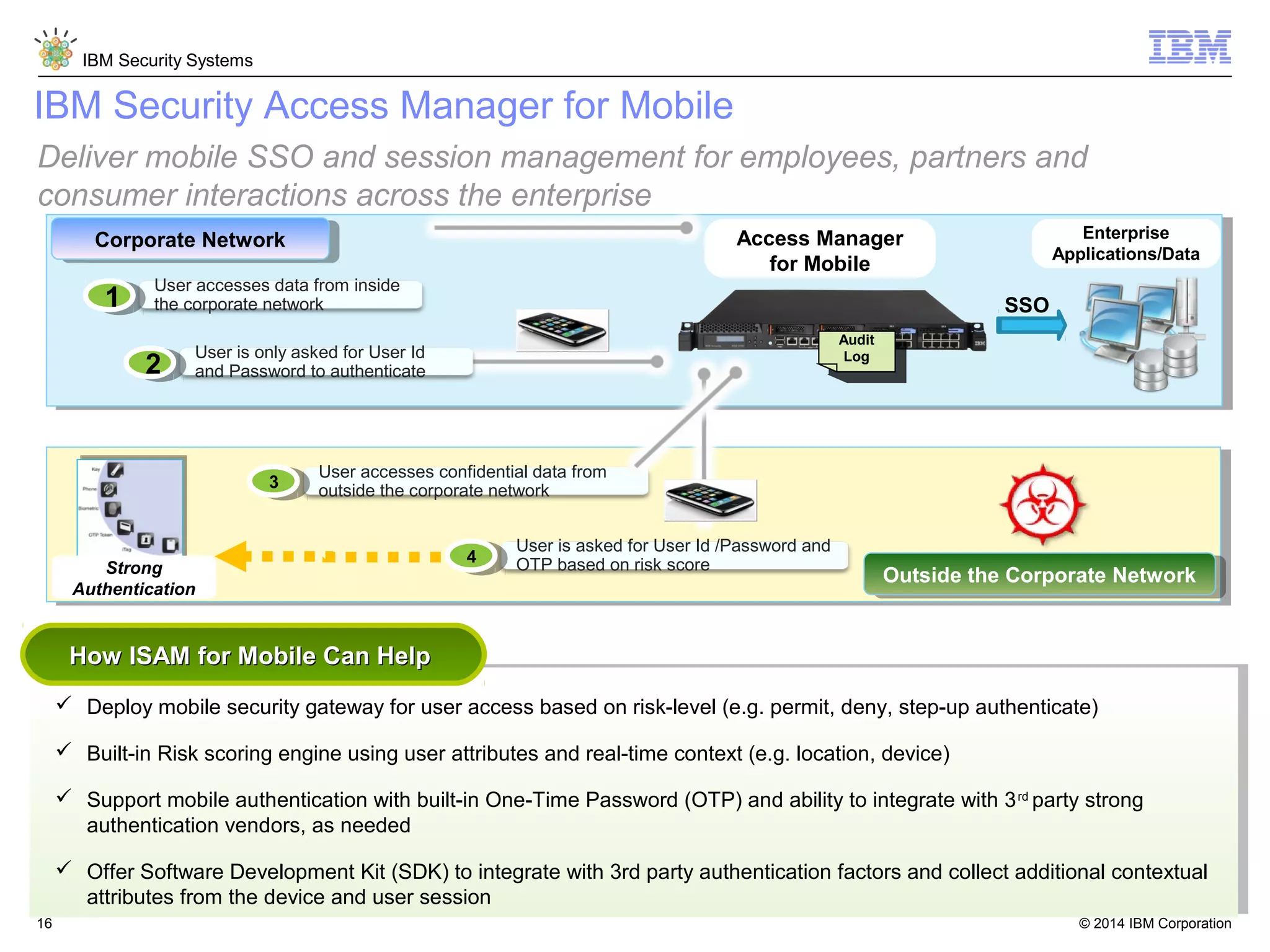
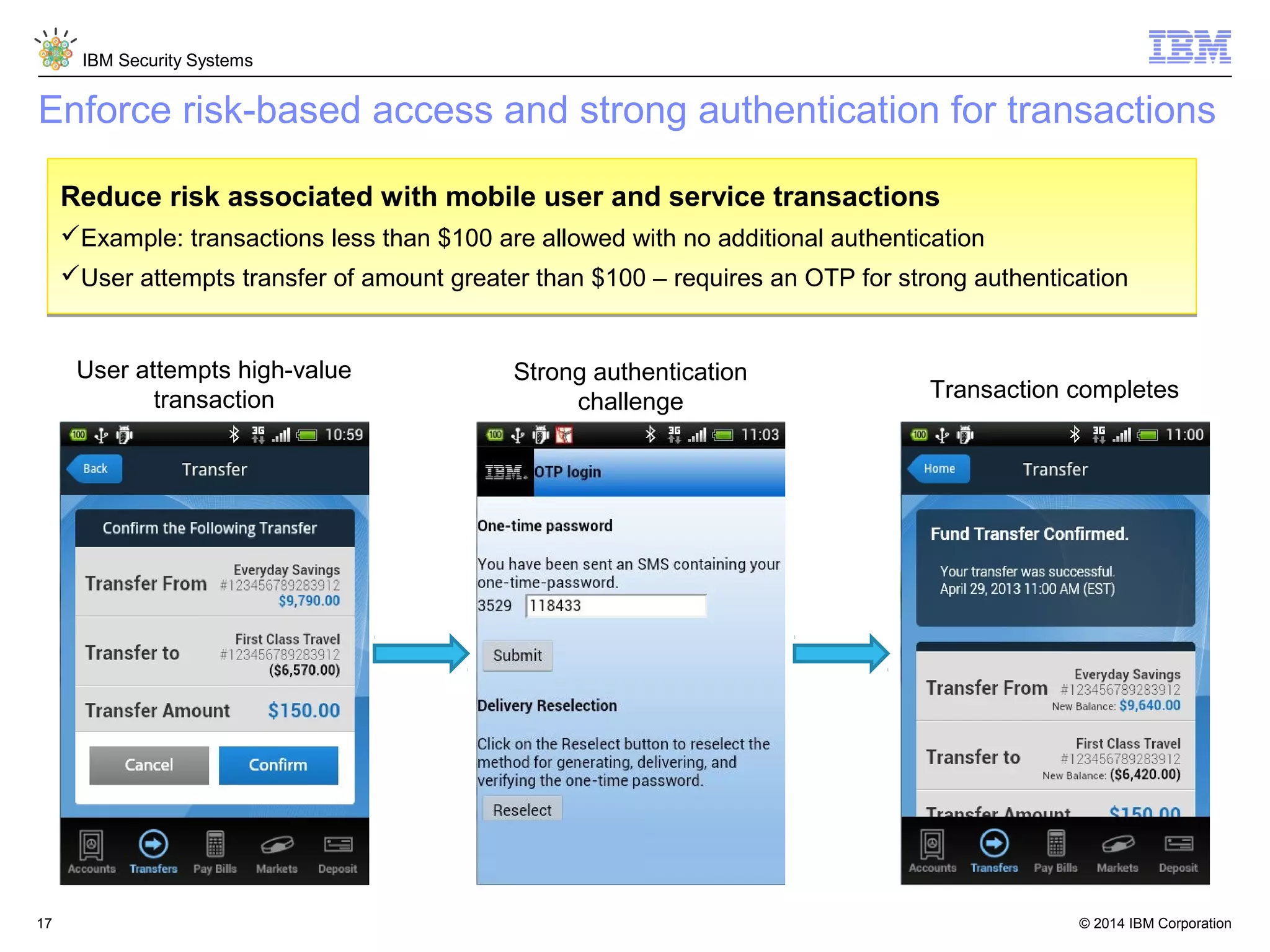
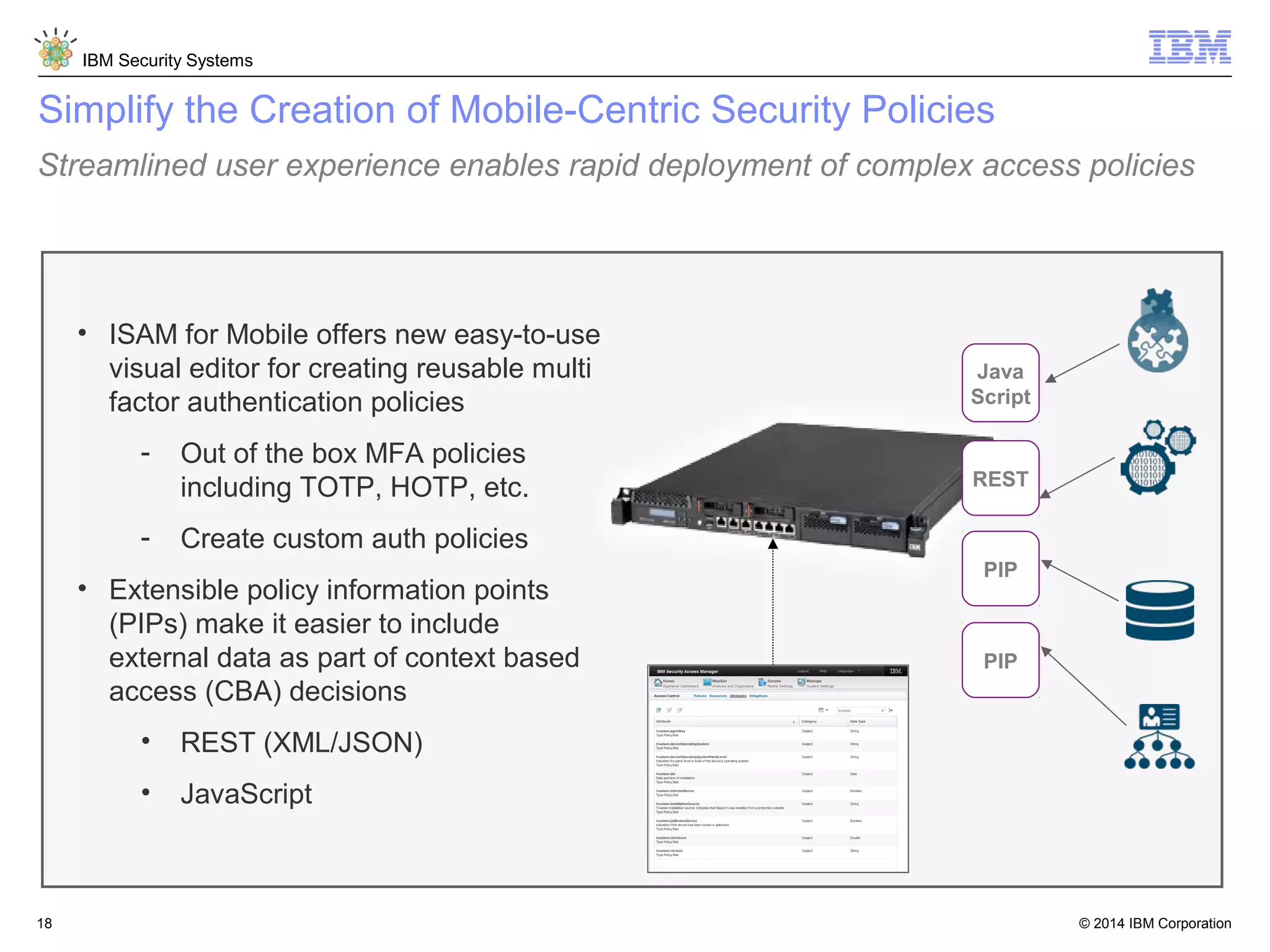
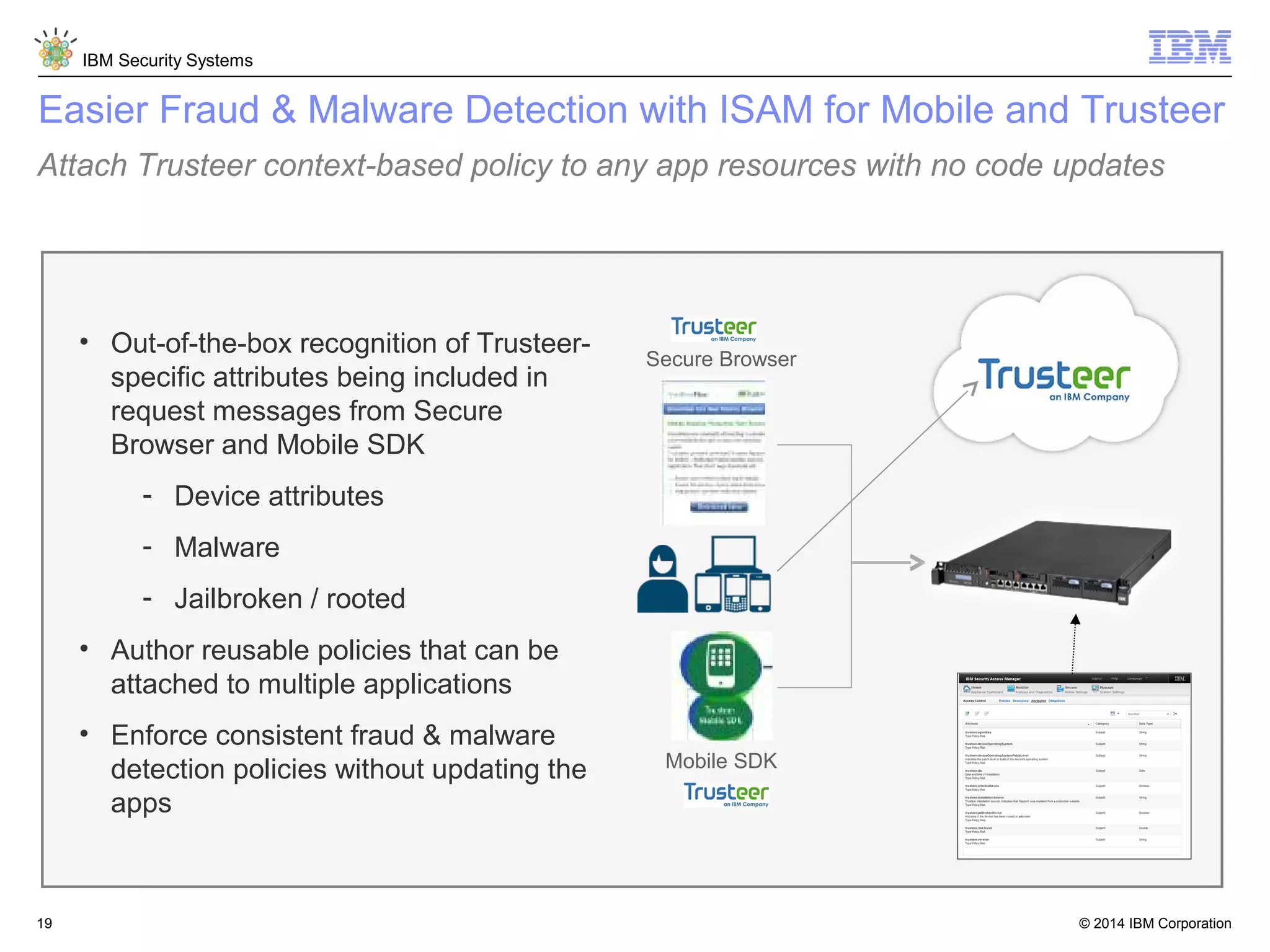
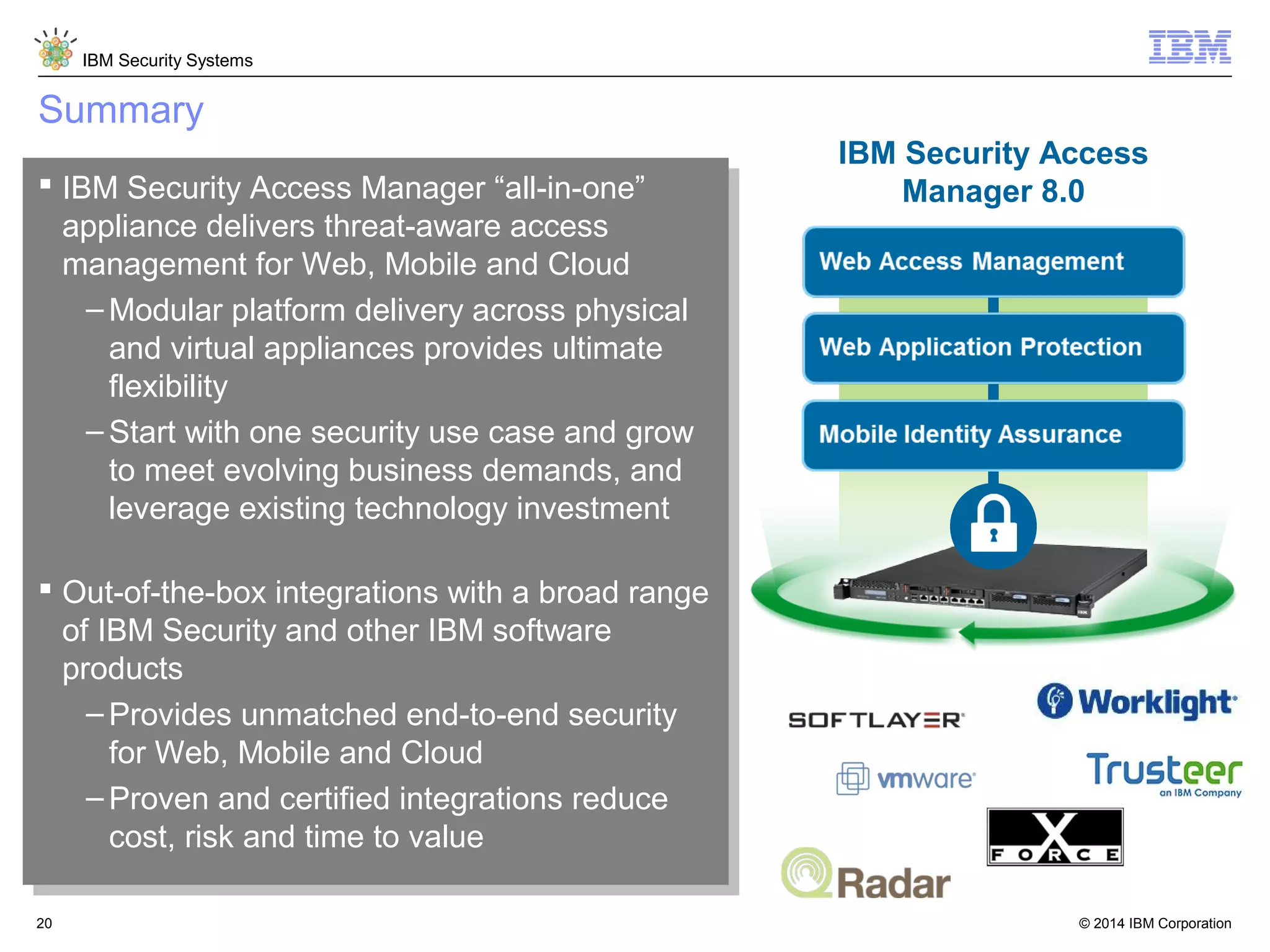
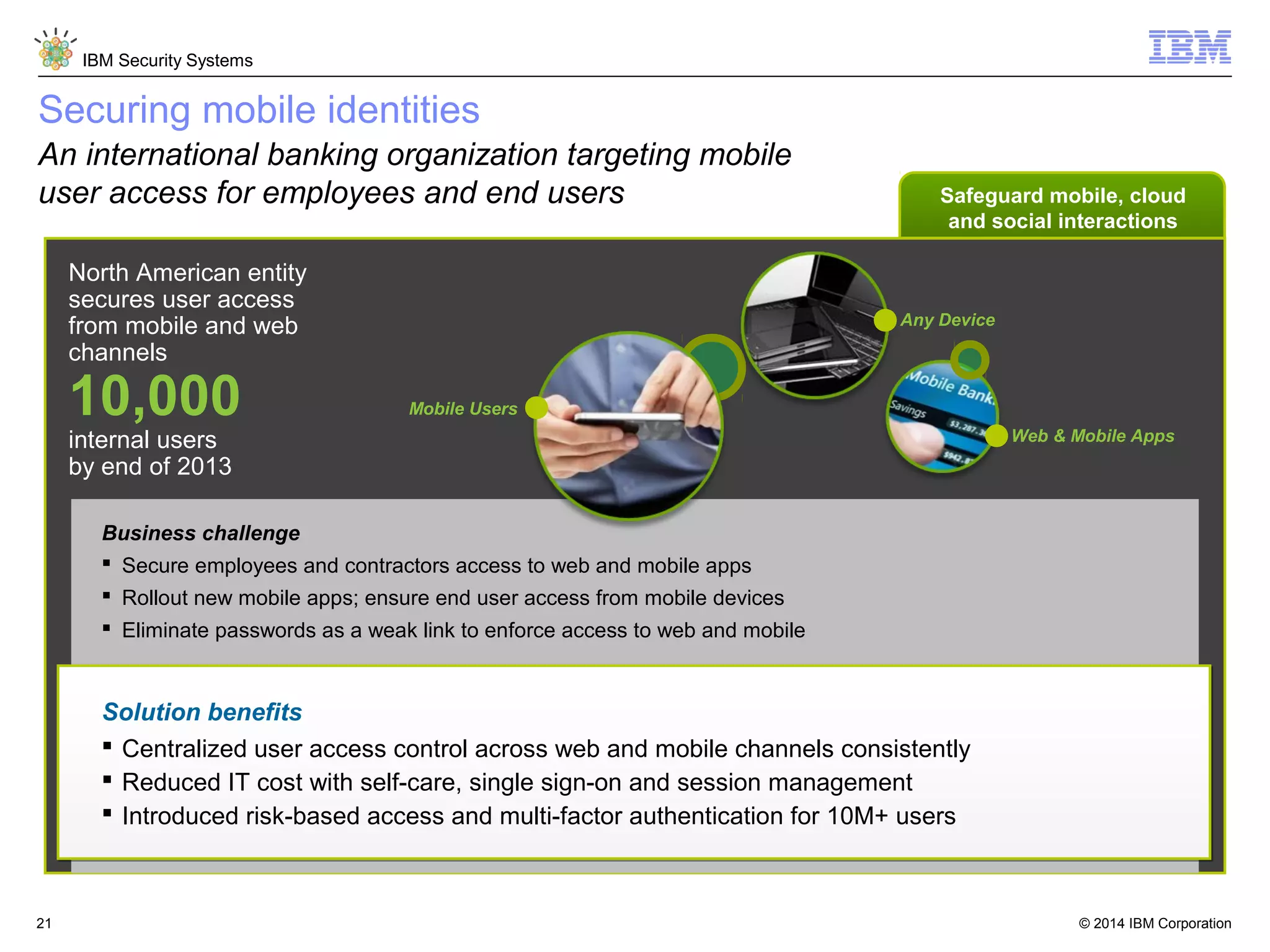
IBM Security Access Manager provides threat-aware identity and access management for securing access across multiple perimeters. It delivers intelligent identity and access assurance, safeguards mobile, cloud, and social interactions, and simplifies identity silos and cloud integrations. The solution uses risk-based adaptive authentication and authorization, integrated threat protection, and identity and access assurance capabilities to prevent insider threats and identity fraud in a multi-perimeter environment.