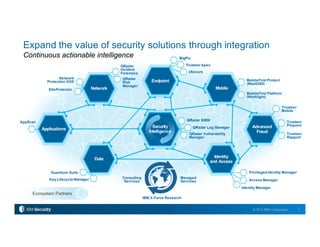
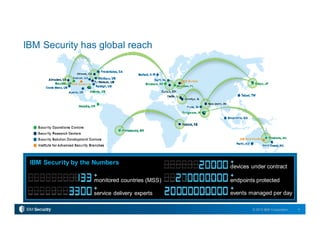
IBM Security provides a comprehensive portfolio of security solutions including IBM MobileFirst Protect (MaaS360), an enterprise mobility management platform. MaaS360 offers mobile device, application, and content management capabilities to secure devices and data across mobile platforms. It integrates threat protection and provides a single console for centralized visibility and control. MaaS360 delivers a unified experience for secure productivity and seamless access to enterprise systems and cloud services.