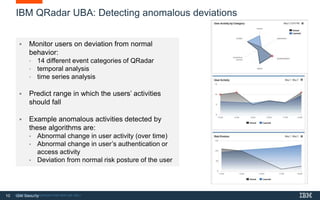
This document discusses IBM's QRadar User Behavior Analytics product for detecting insider threats and risks. It provides an agenda for the presentation which includes discussing challenges around insider threats, IBM UBA capabilities using machine learning, and IBM's integrated approach to insider threat protection. It also includes a case study example of how IBM implemented its solution for a global pharma client to help address concerns around the impact of a major reorganization on employee morale.