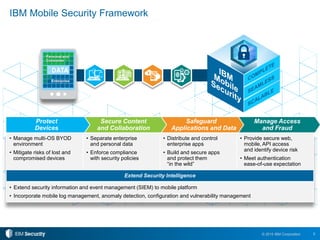
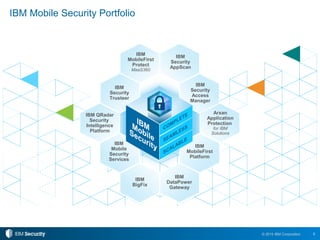
The document discusses the increasing importance of mobile security as mobile device usage within enterprises continues to grow, leading to heightened security threats. It highlights the need for robust mobile management strategies, including protecting sensitive corporate data, managing device access, and ensuring compliance with security policies. Furthermore, it outlines IBM's mobile security solutions, including tools for managing multi-OS environments, securing applications, and empowering users through self-service portals.