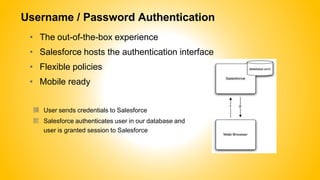
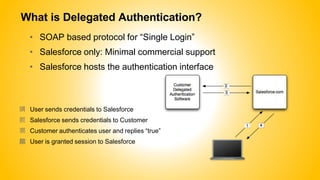
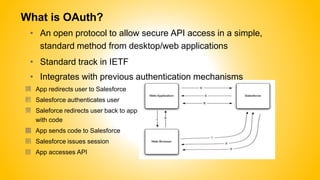
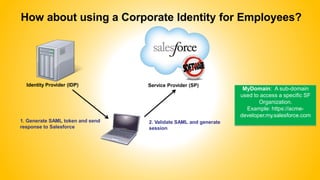
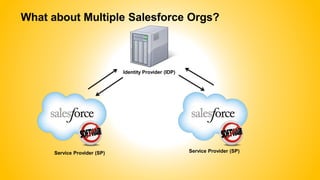
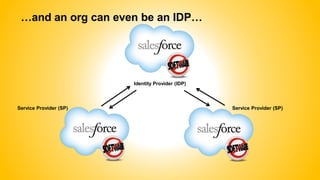
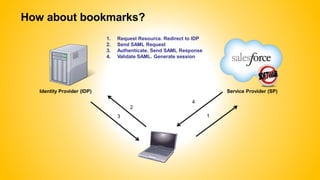
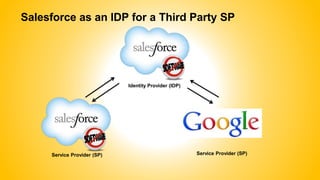
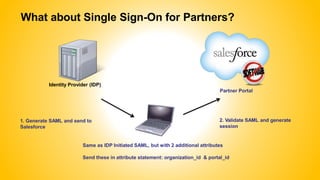
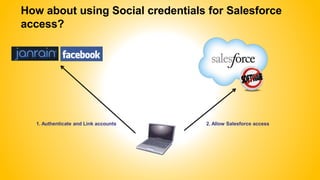
Single sign-on (SSO) allows users to access multiple systems after one authentication. Common SSO protocols discussed include SAML, OAuth, and username/password. SAML is best for single sign-on across websites while OAuth is for secure API access. Best practices include high availability, proactive certificate management, custom error pages, and testing. The document provides an overview of SSO concepts and recommendations for implementation and troubleshooting.