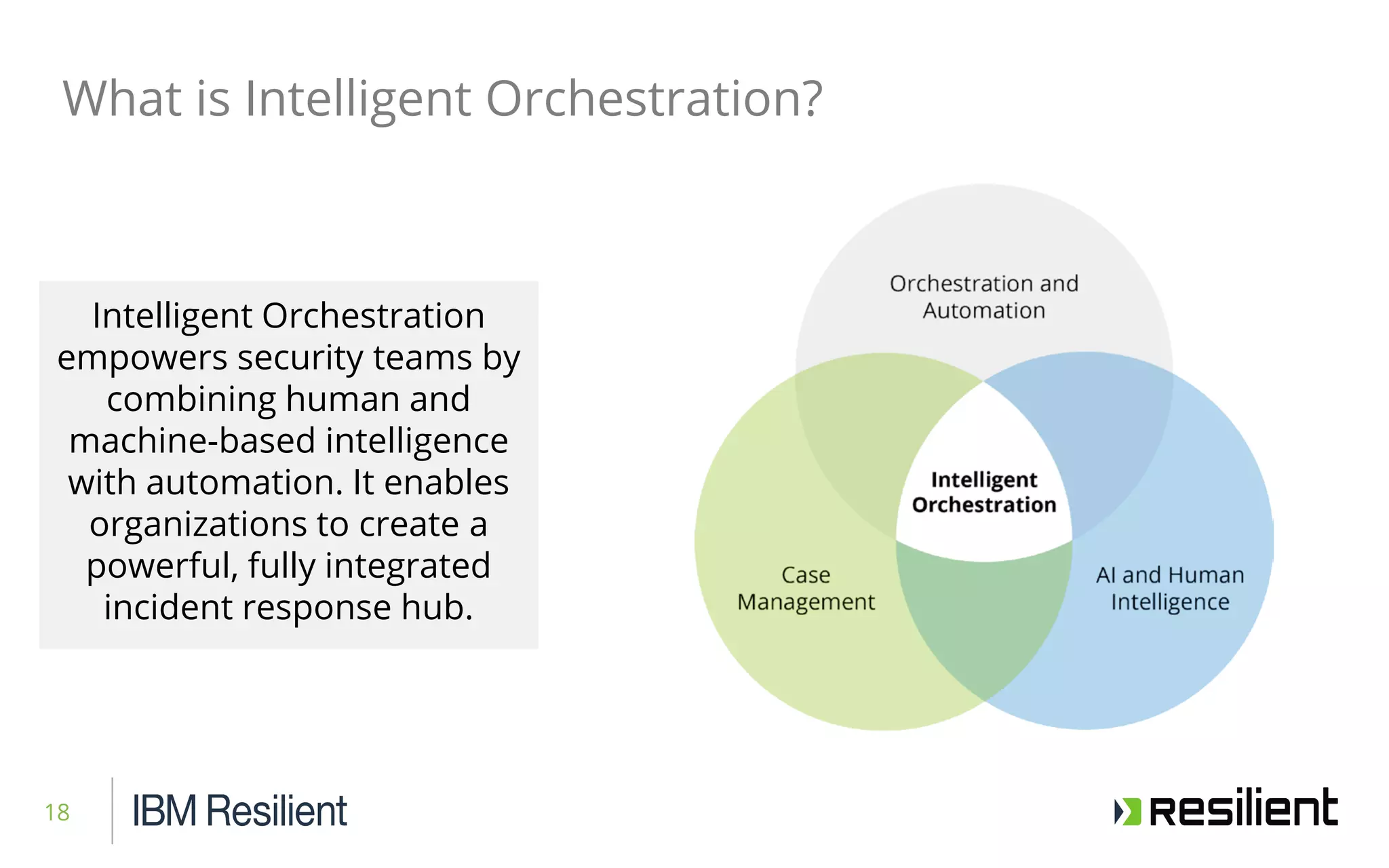
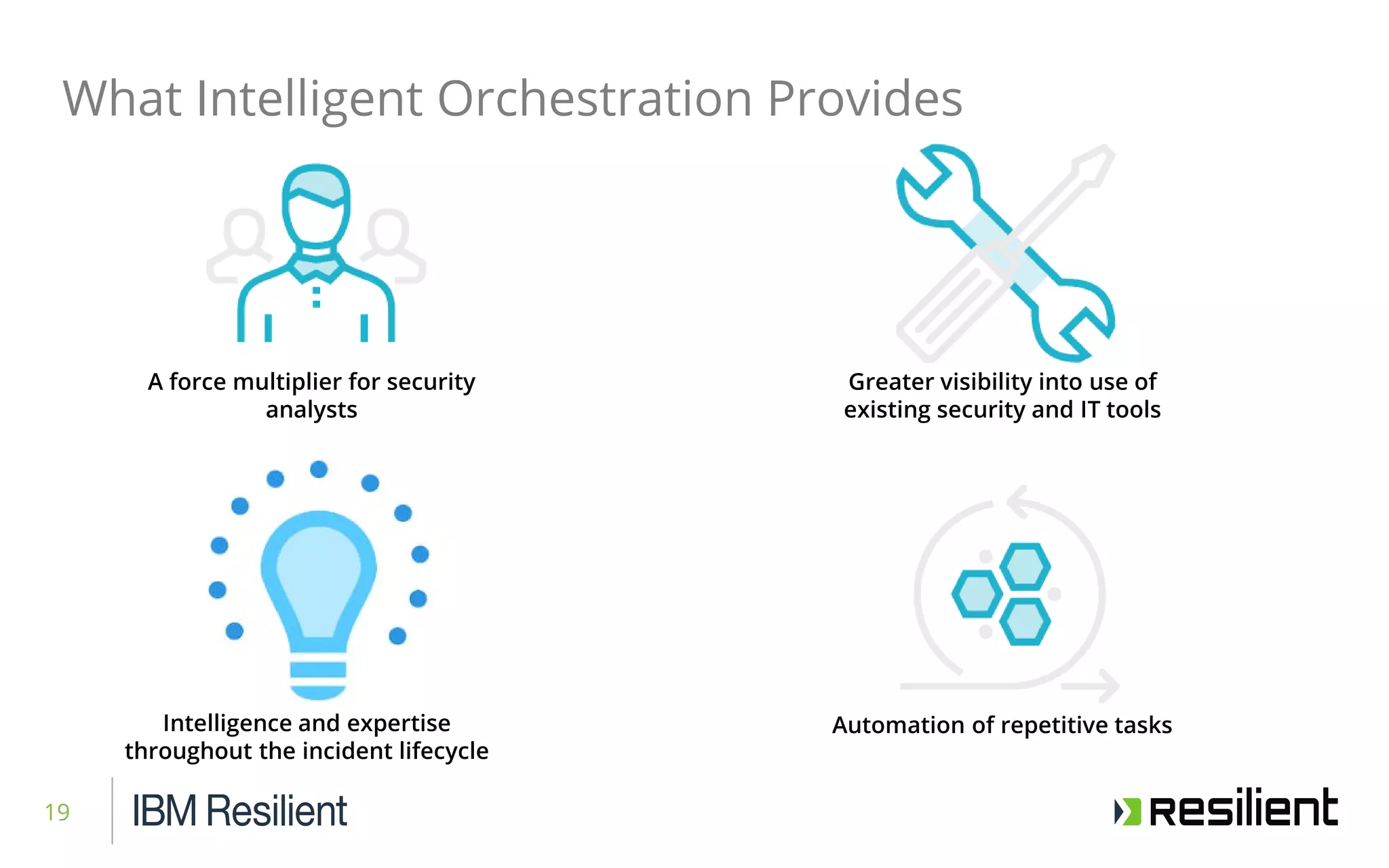
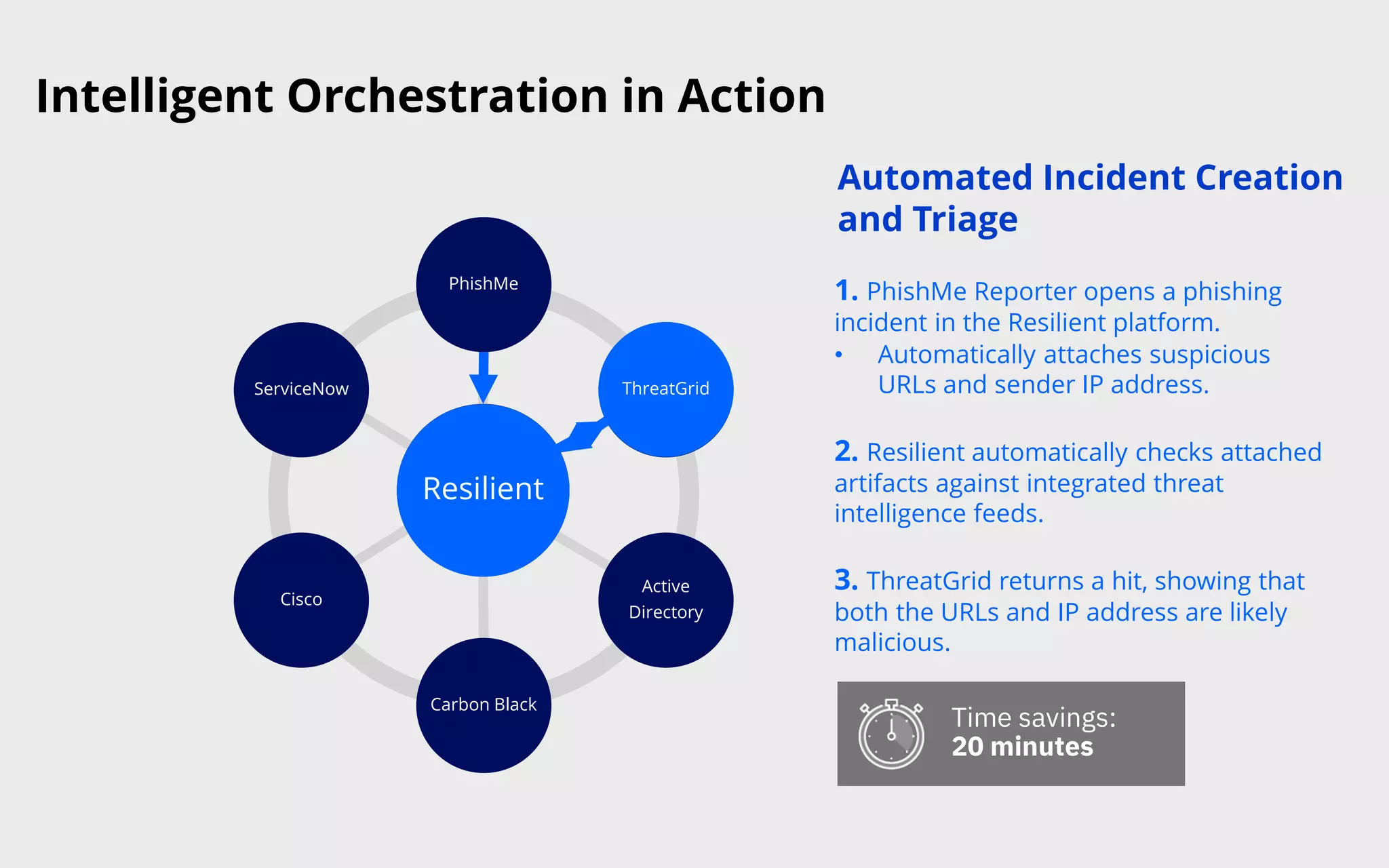
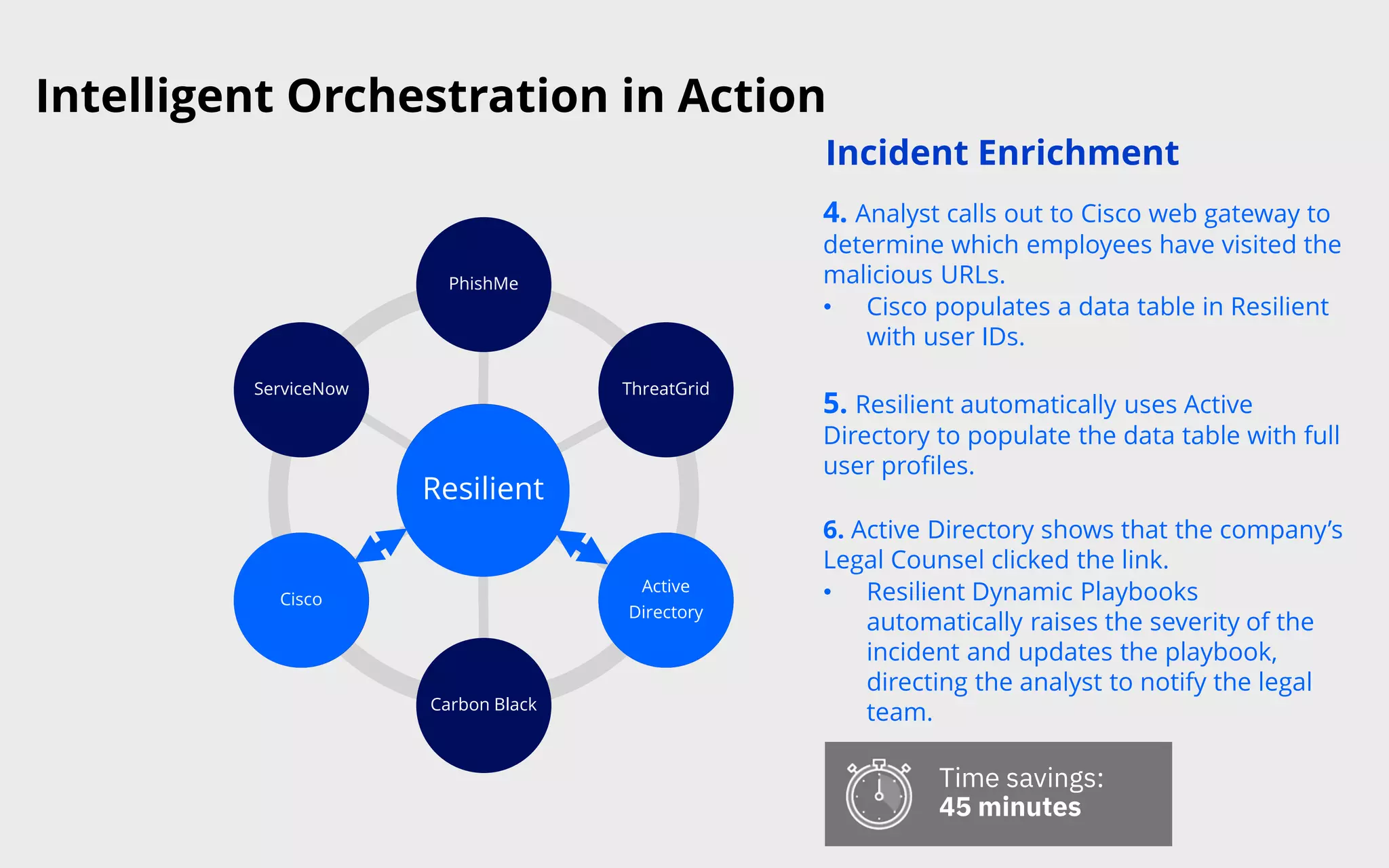
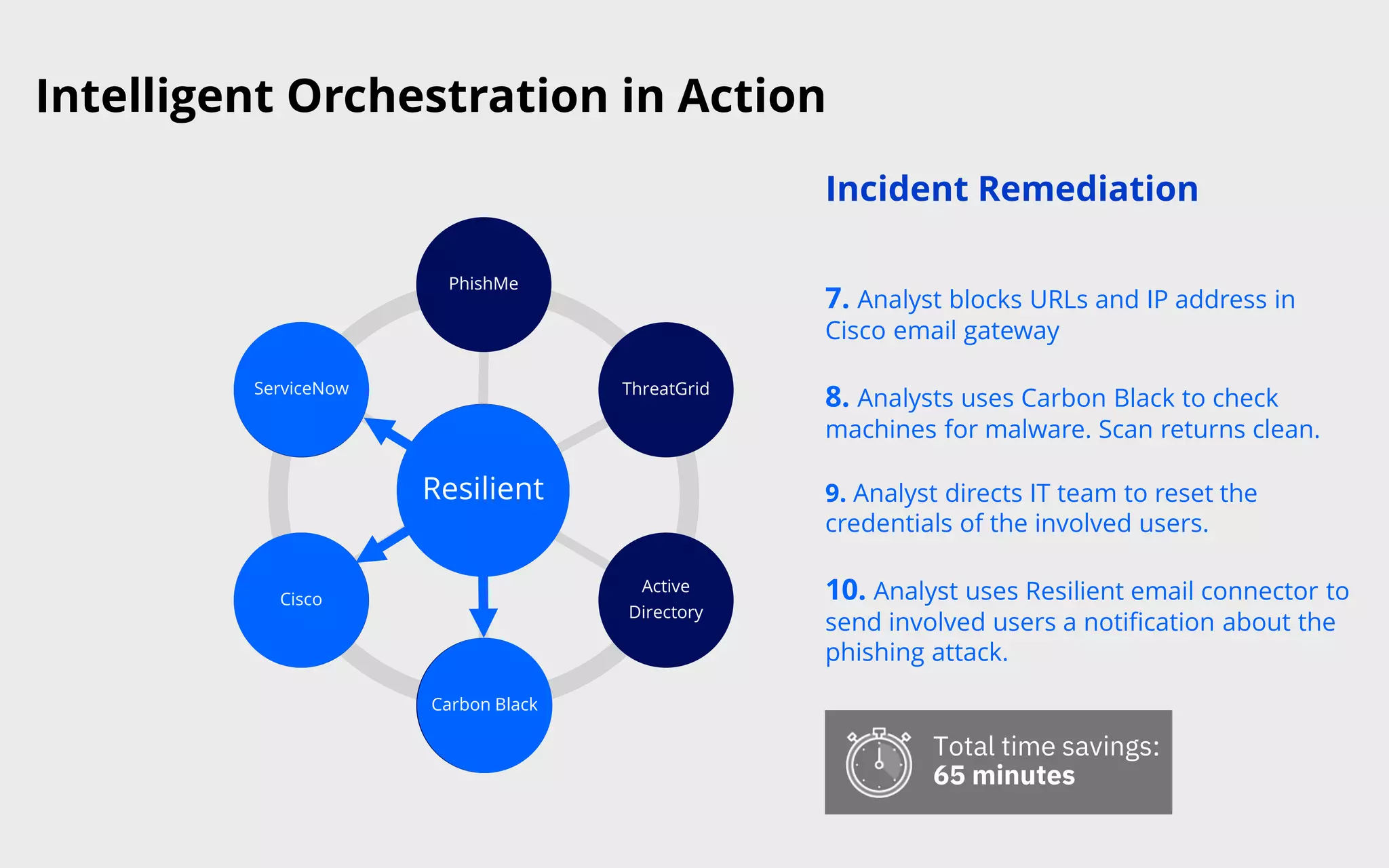
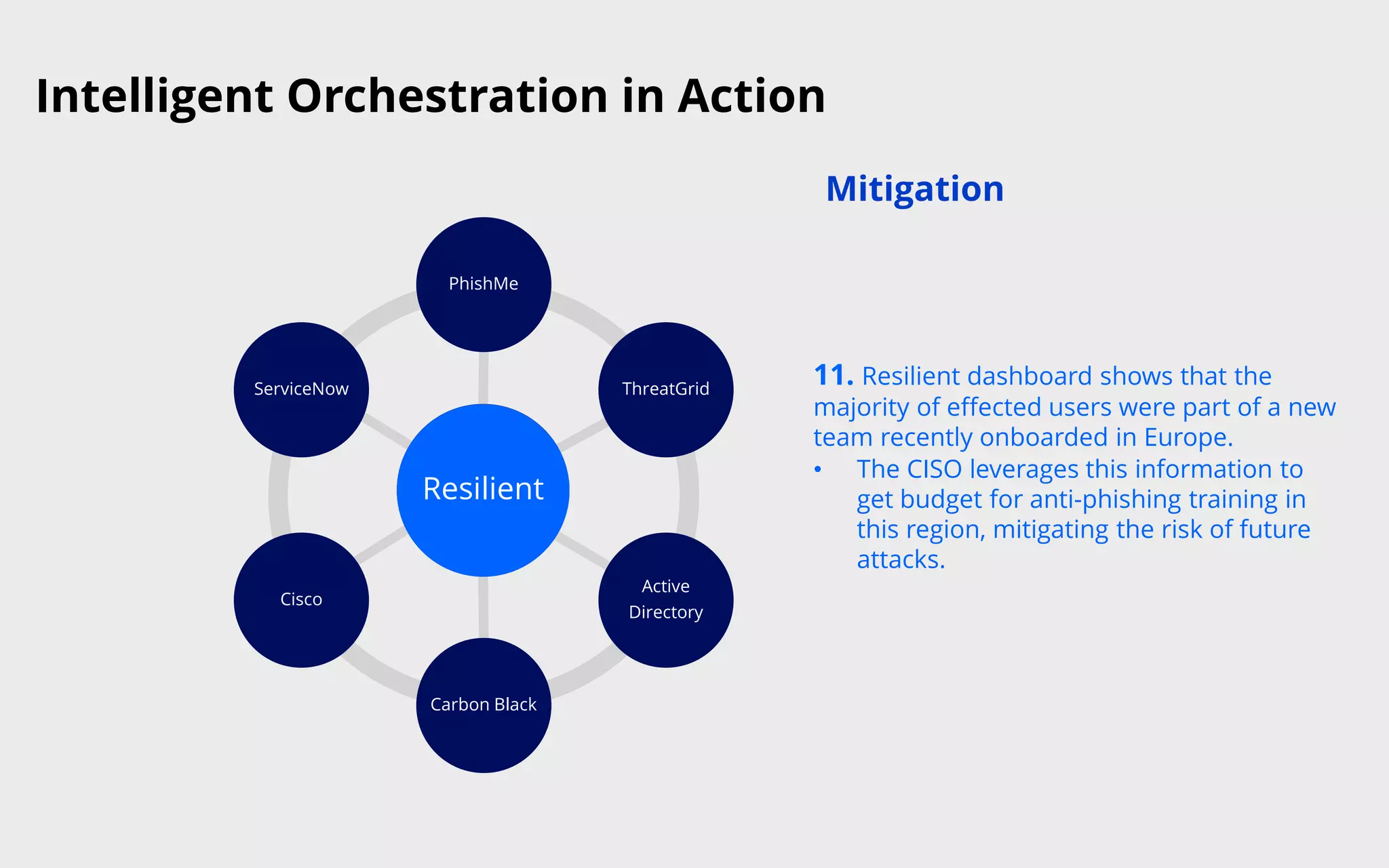
This document discusses intelligent orchestration for security operations centers. It begins with an overview of the challenges facing SOCs and how intelligent orchestration can help by combining human and machine intelligence with automation. It then provides an example use case of how intelligent orchestration allows a SOC to quickly investigate and remediate a phishing incident through automated tools and dynamic playbooks. The document emphasizes that intelligent orchestration acts as a force multiplier for analysts by automating repetitive tasks and providing greater visibility into security tools. It estimates the example incident response was completed in around 65 minutes faster due to intelligent orchestration capabilities.