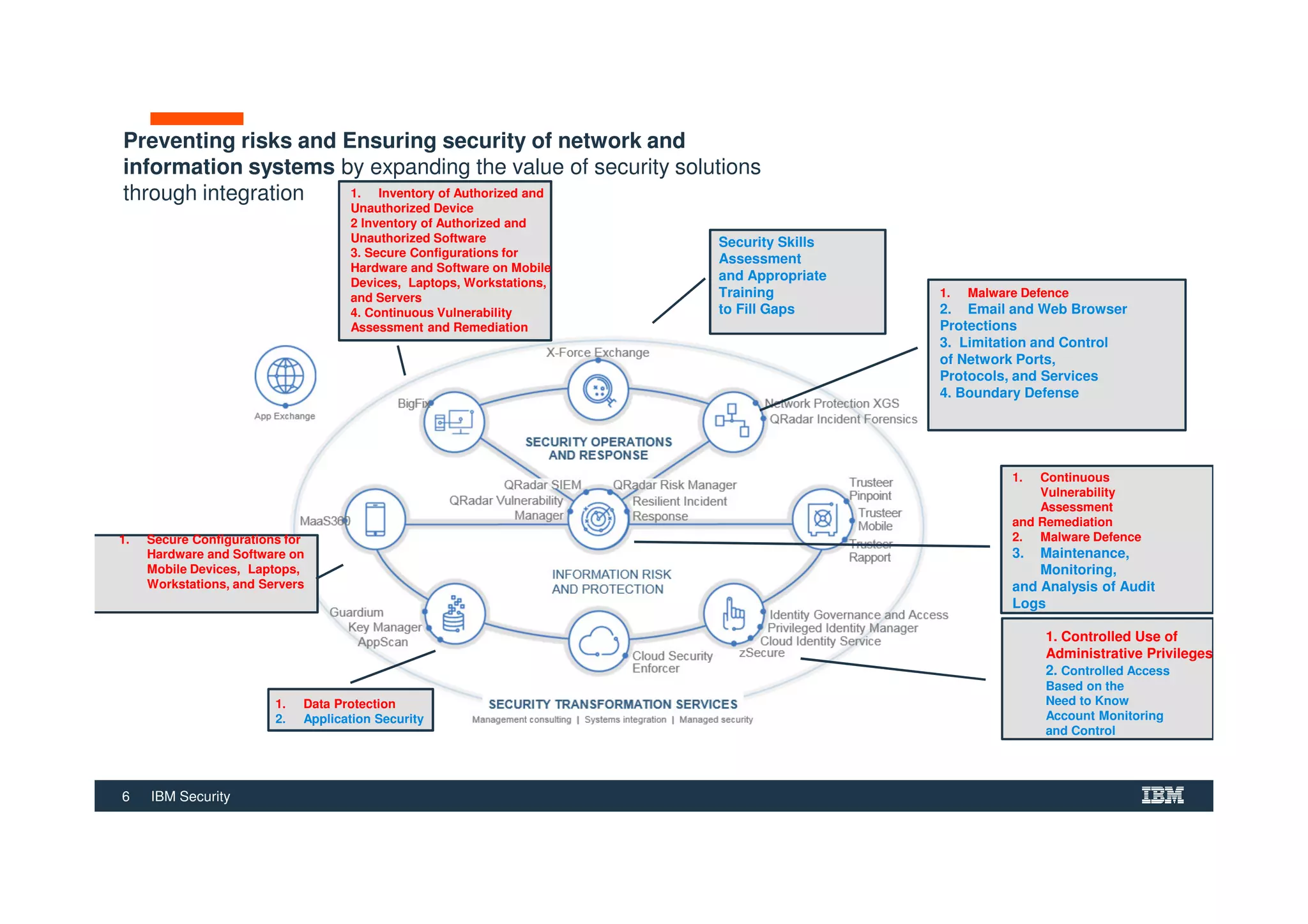
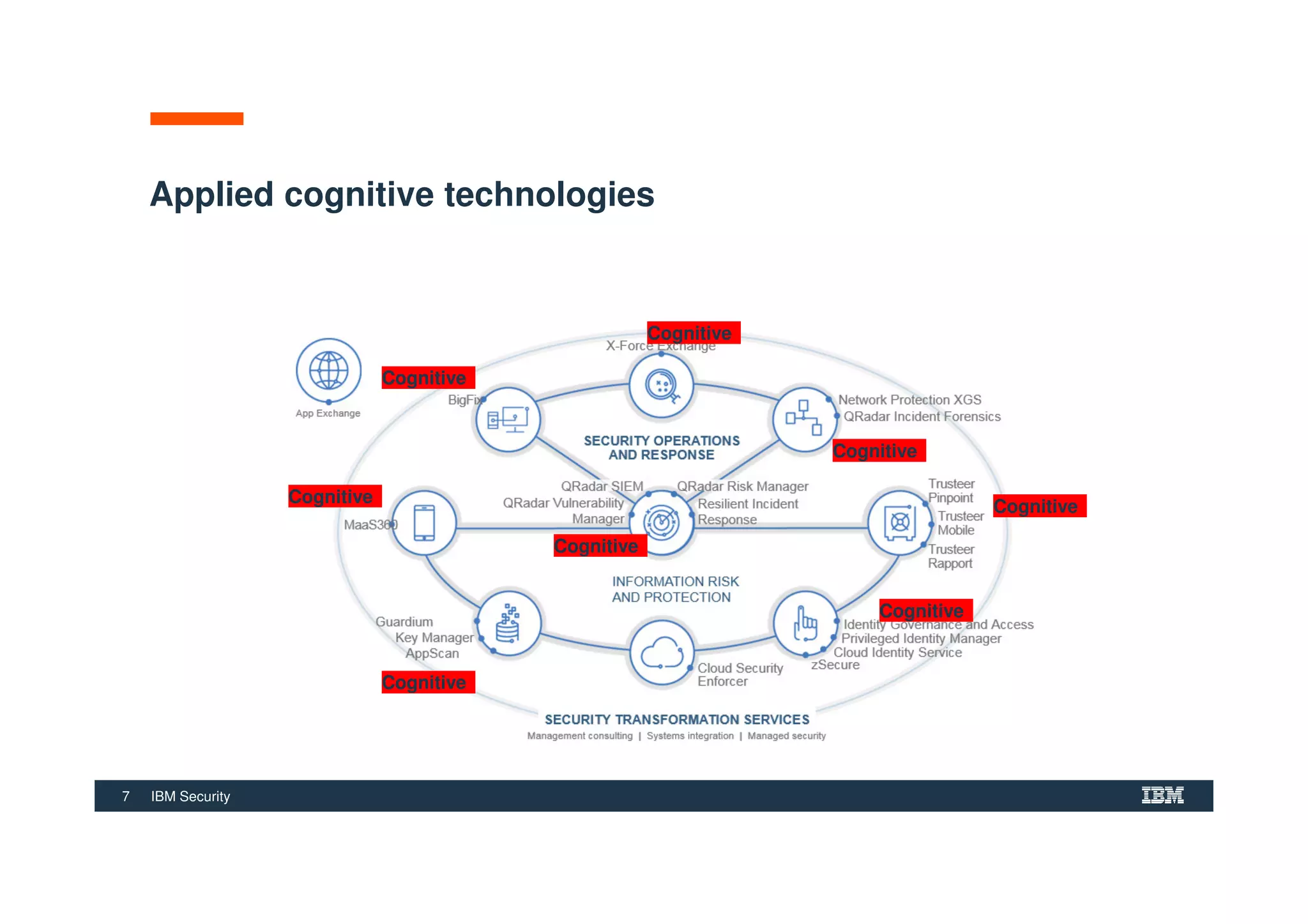
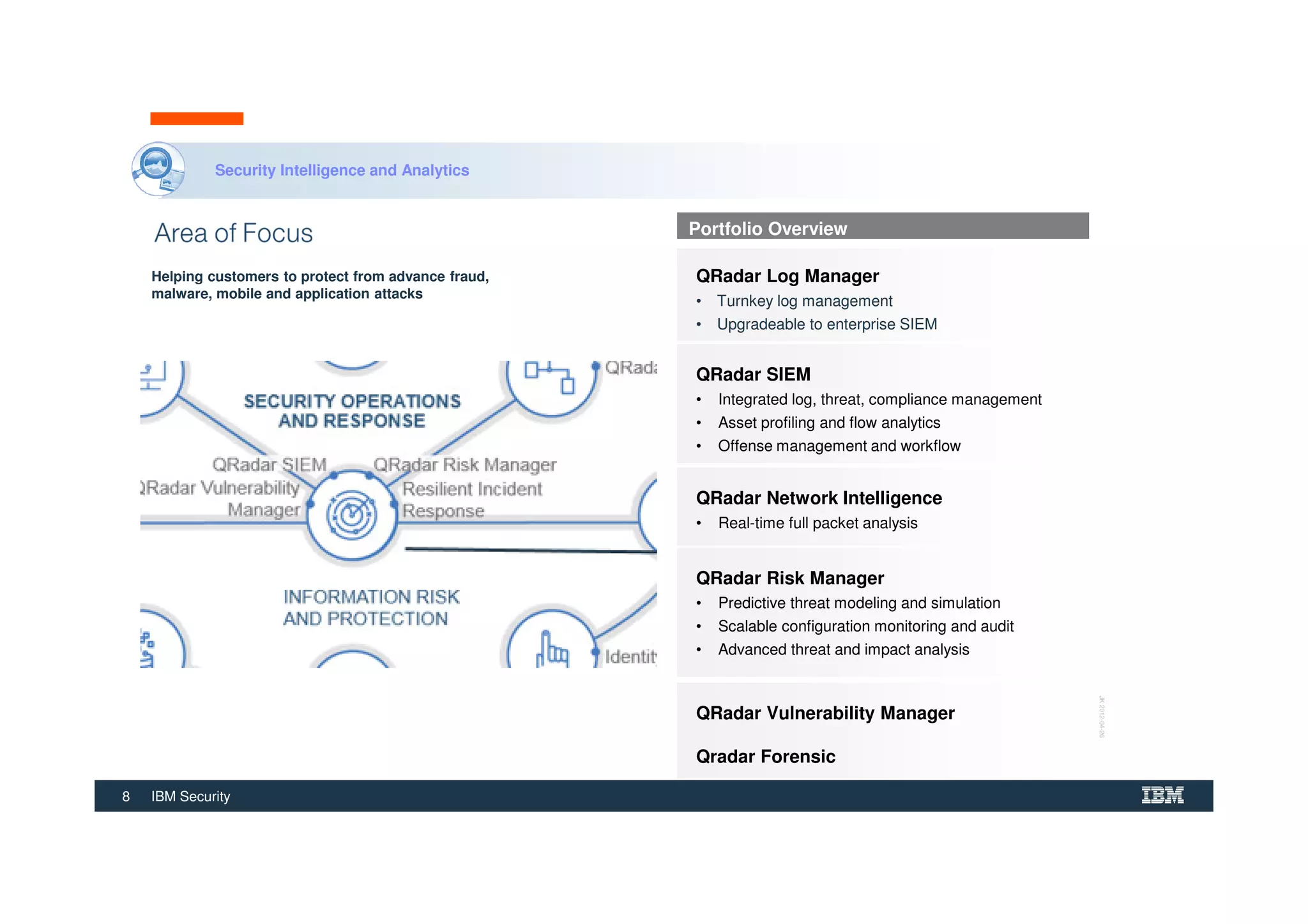
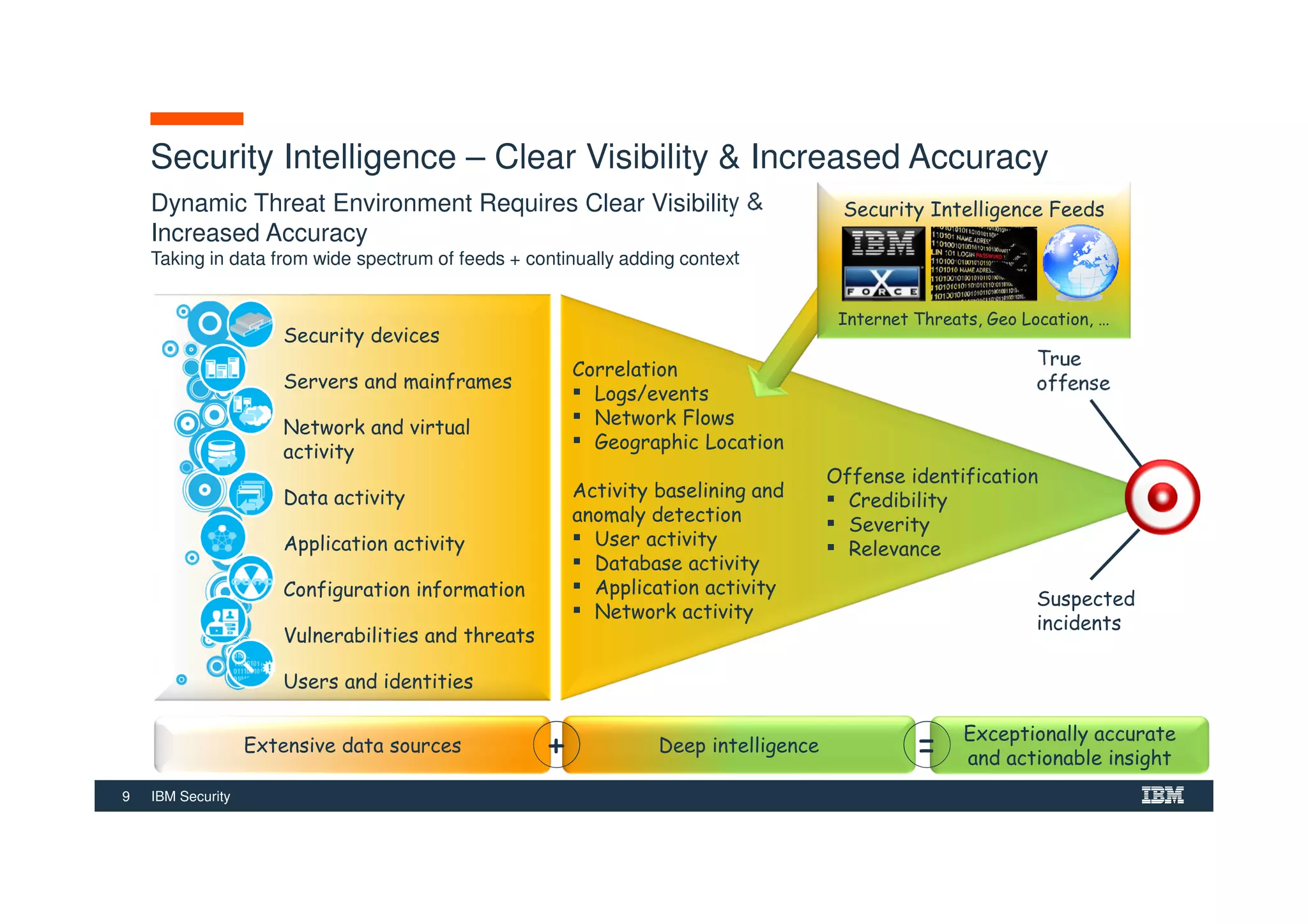
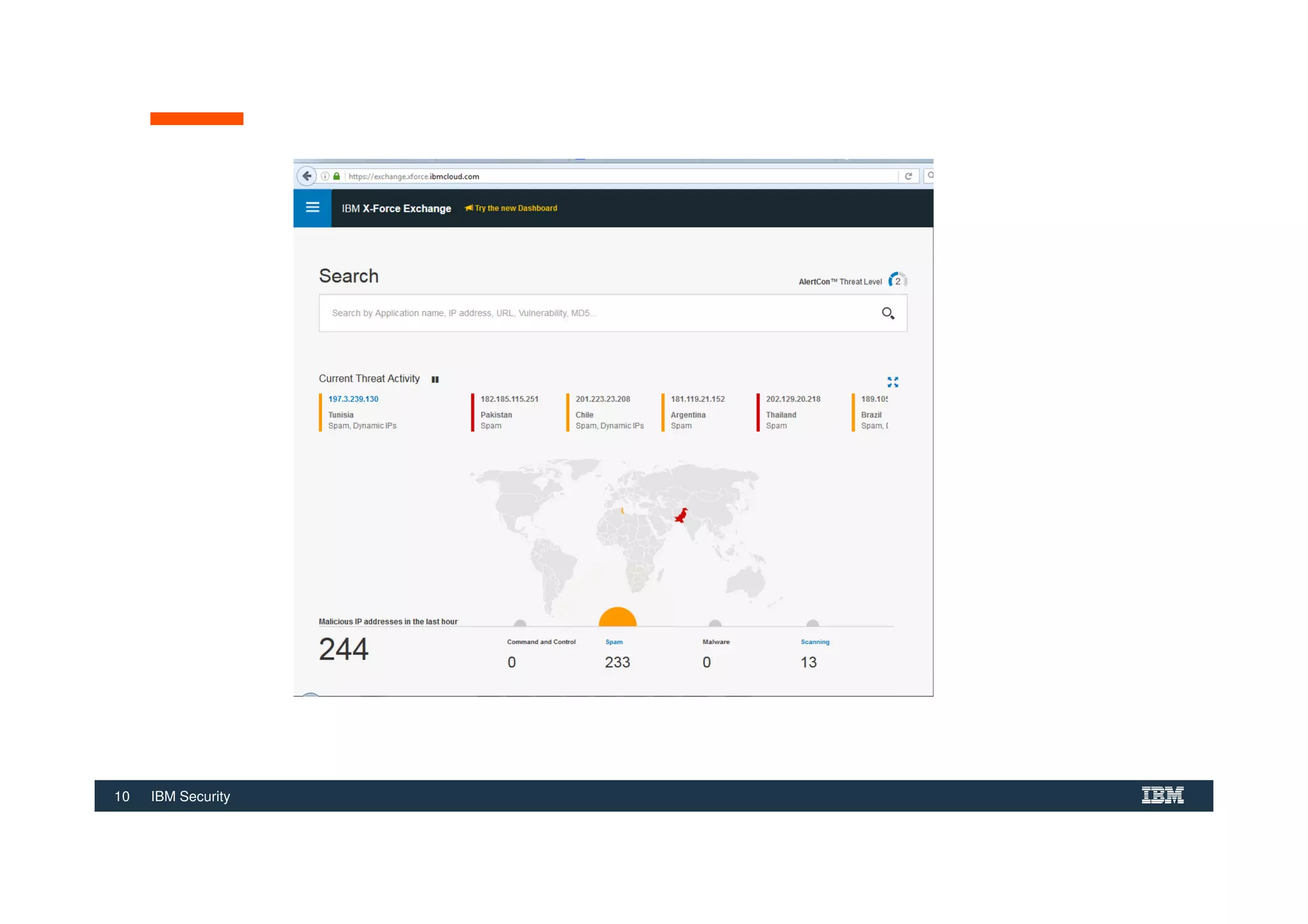
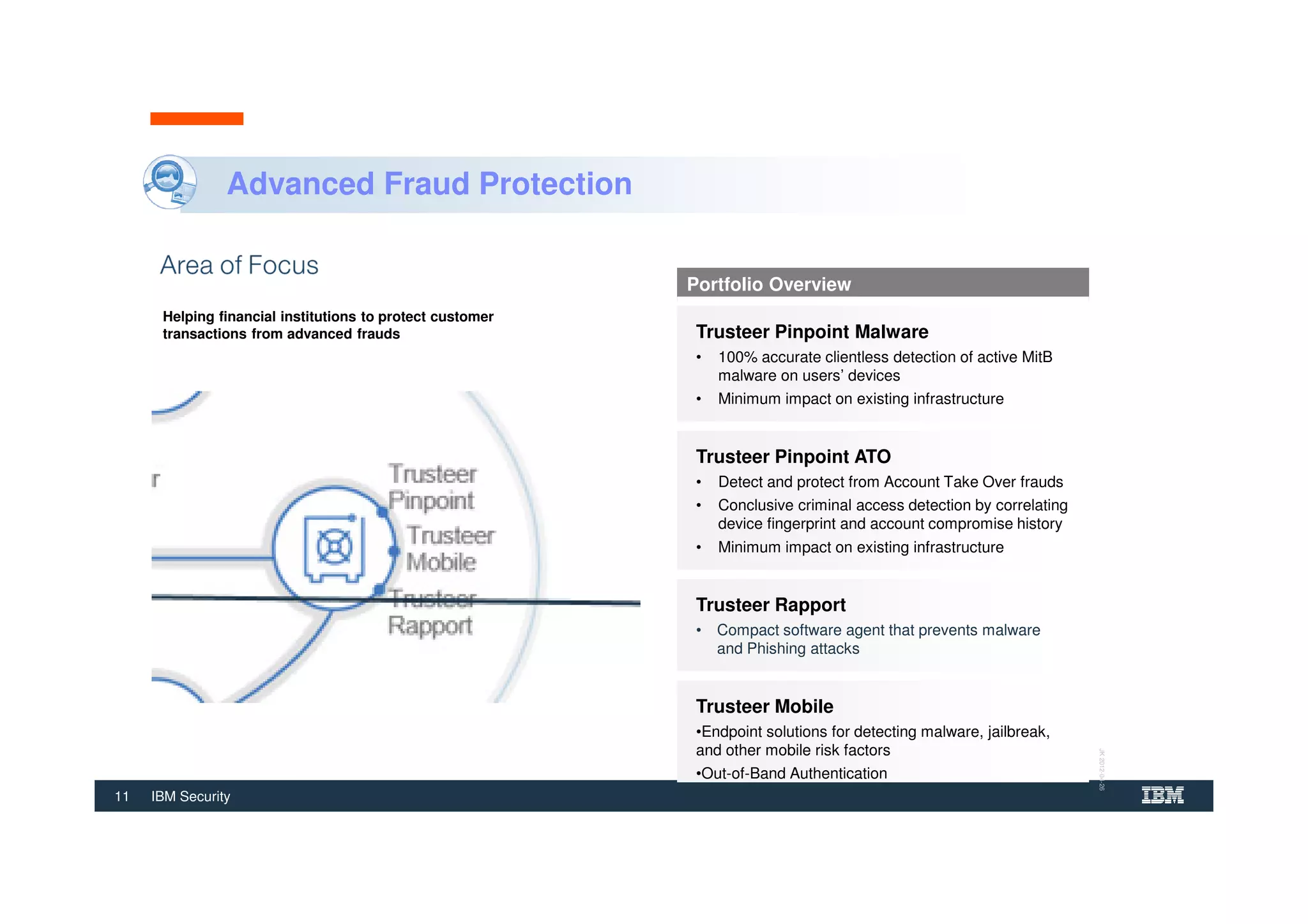
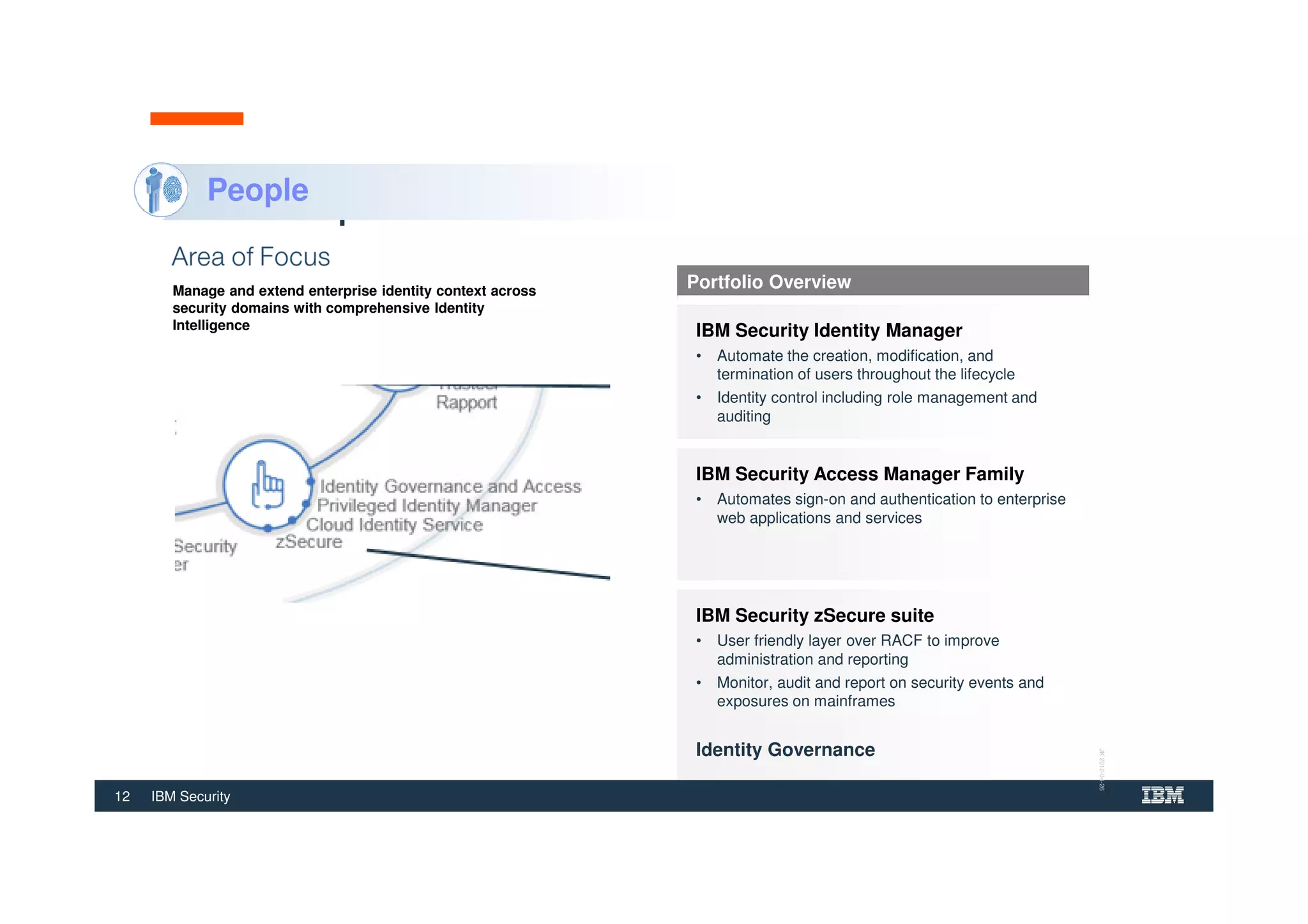
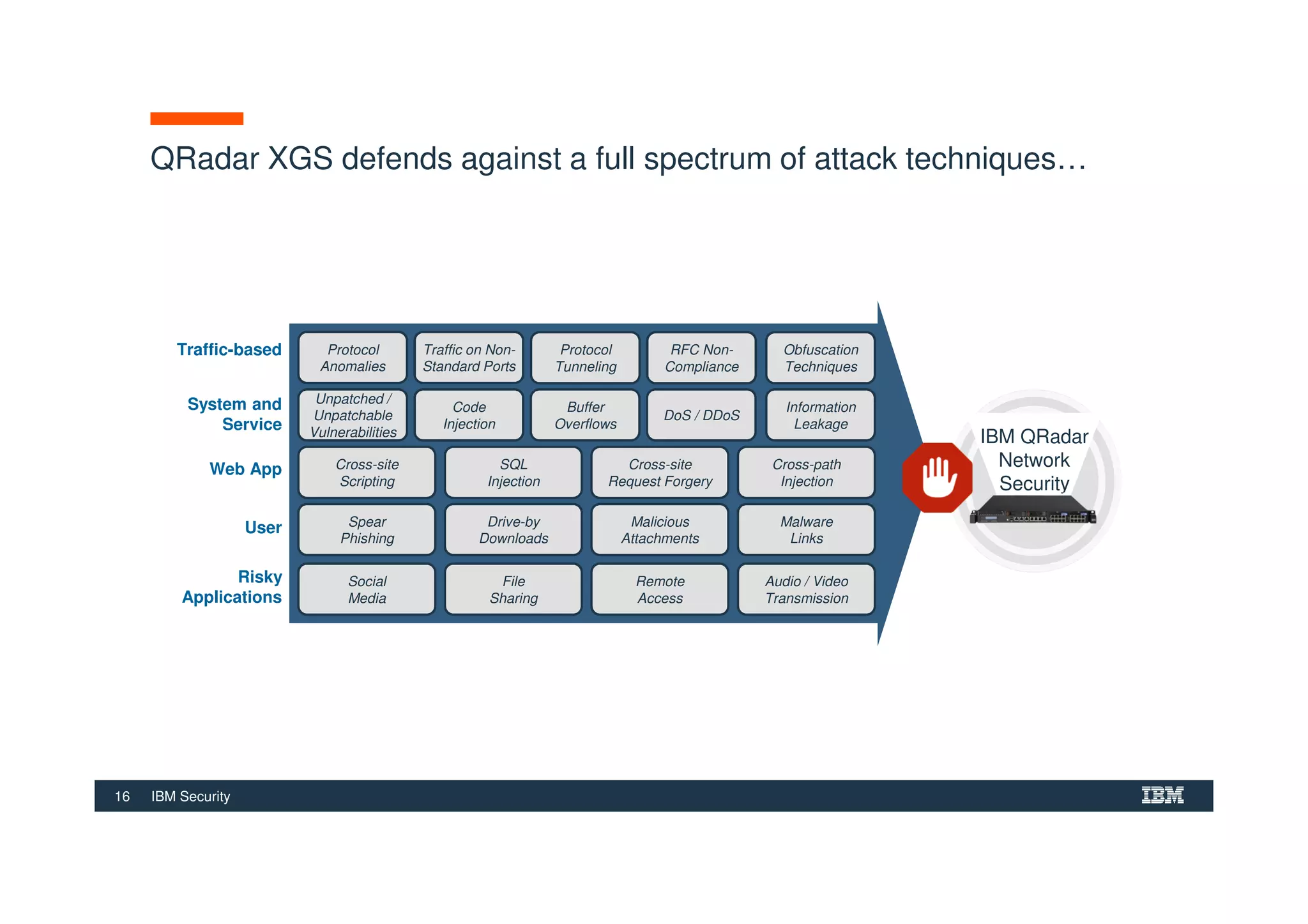
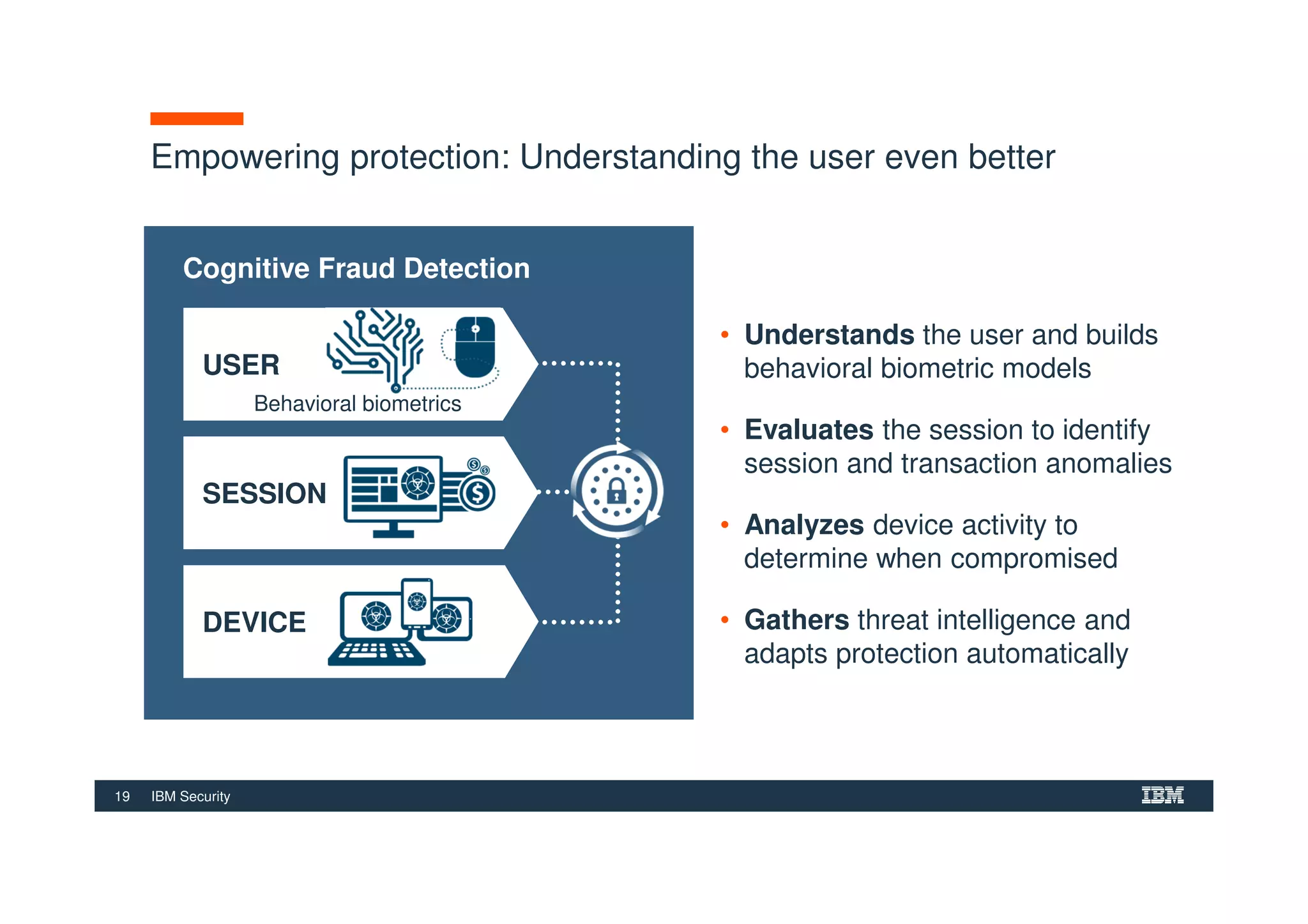
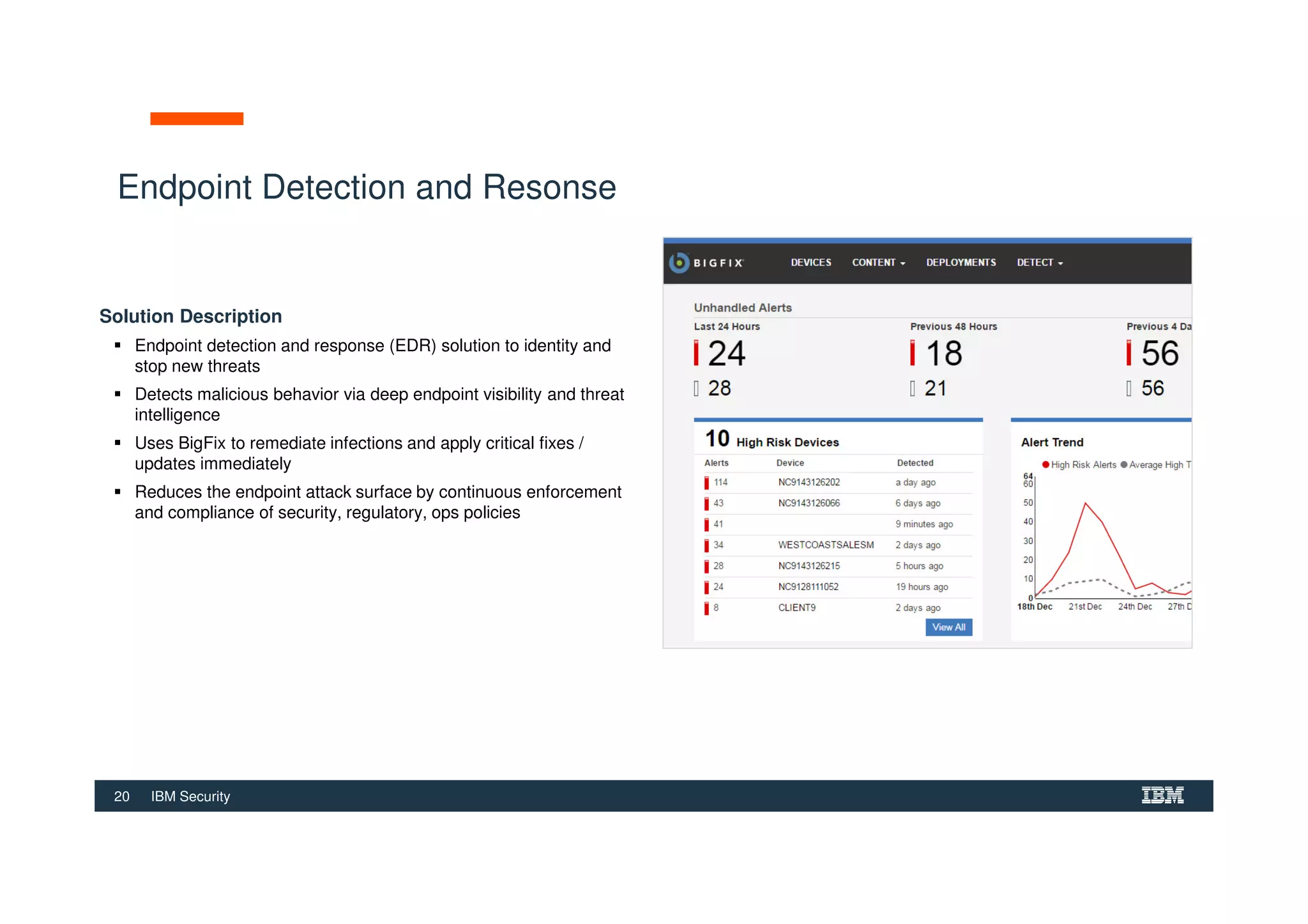
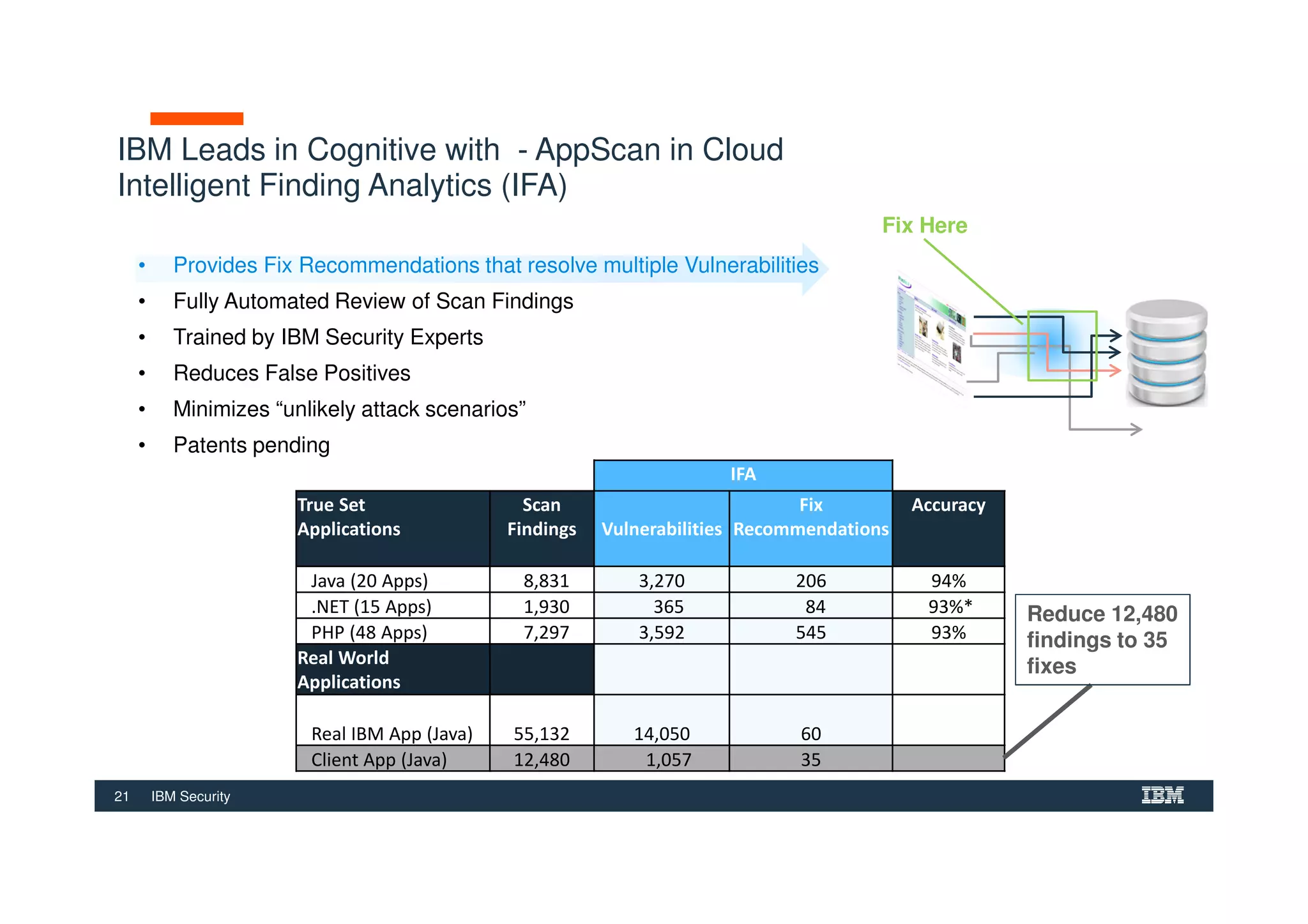
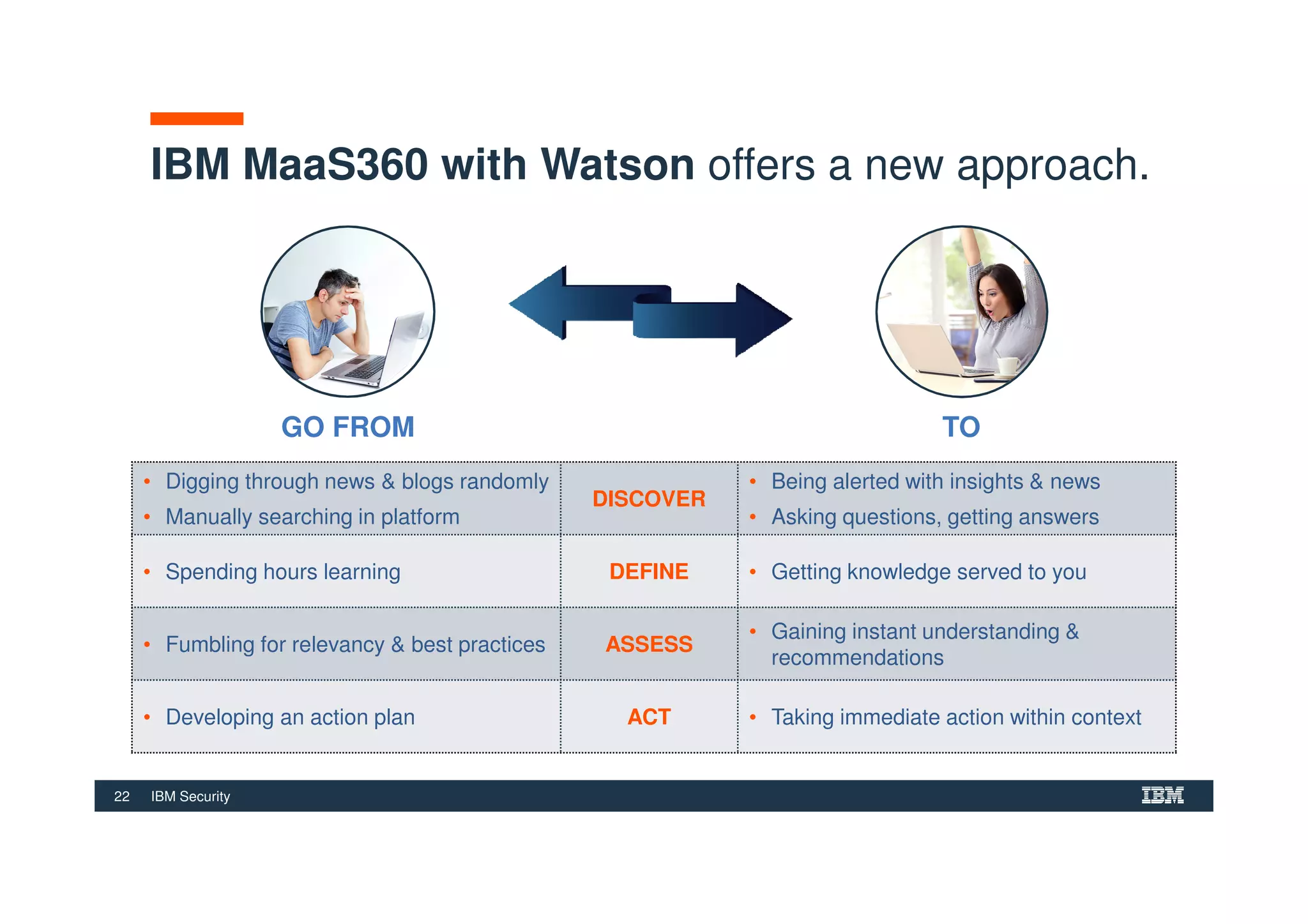
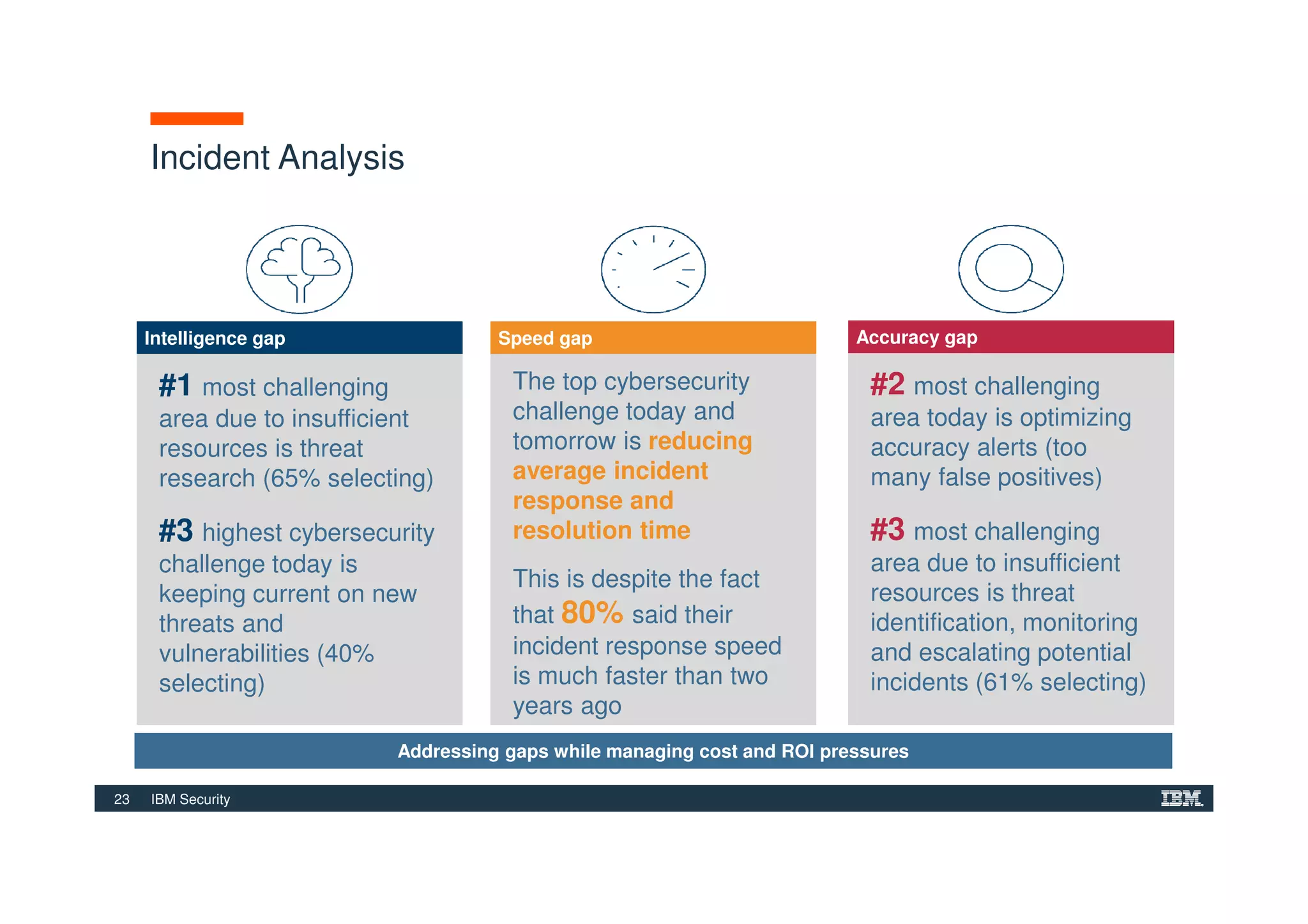
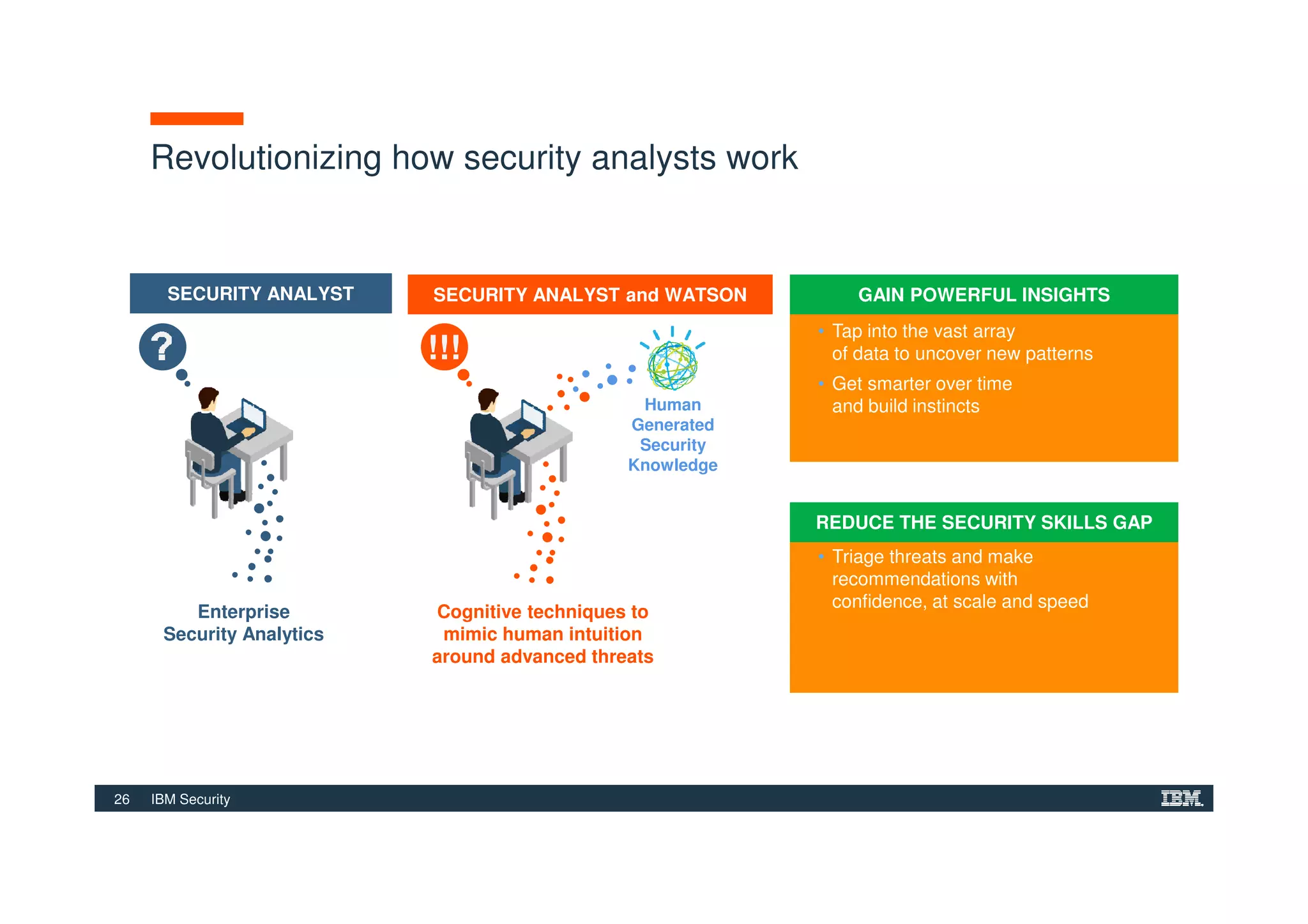
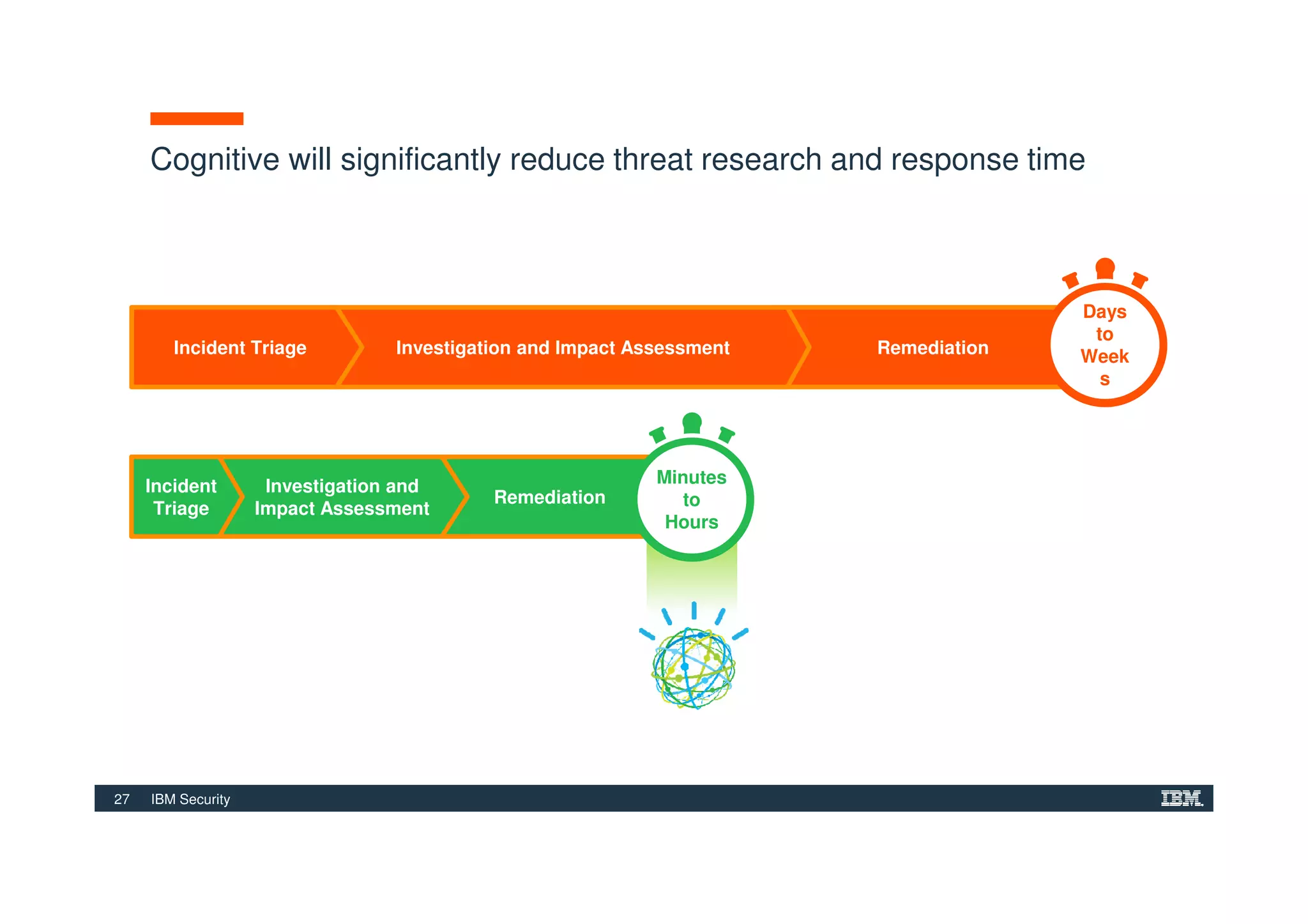
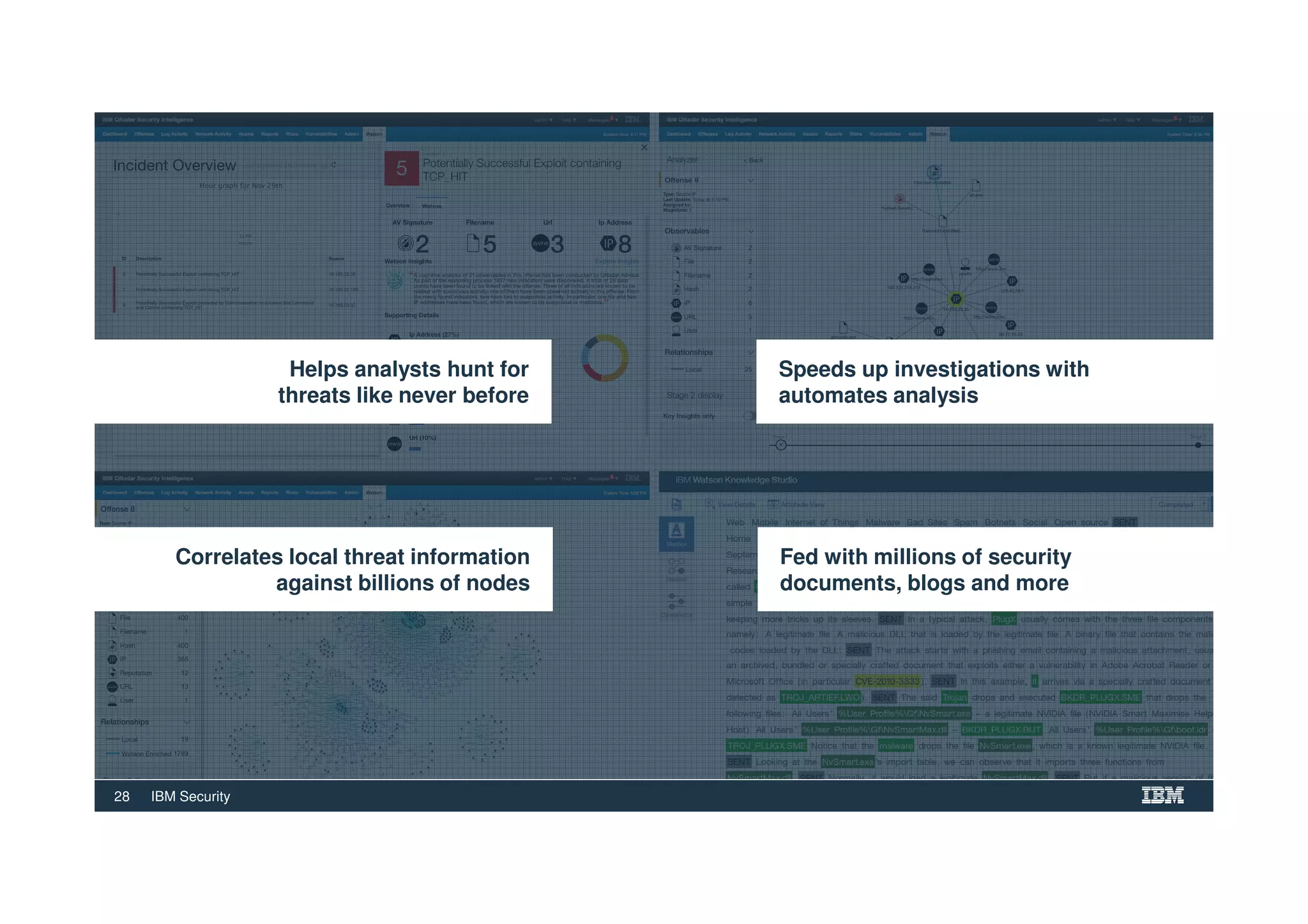
The document outlines various security technologies and strategies provided by IBM to help clients comply with legal and regulatory requirements, particularly in the context of cybersecurity threats such as WannaCry. It details several security controls and products aimed at protecting against malware, fraud, and data breaches, including inventory management, vulnerability assessments, and advanced incident response solutions. Additionally, it emphasizes the importance of integrating intelligent security solutions for better threat detection and compliance management.