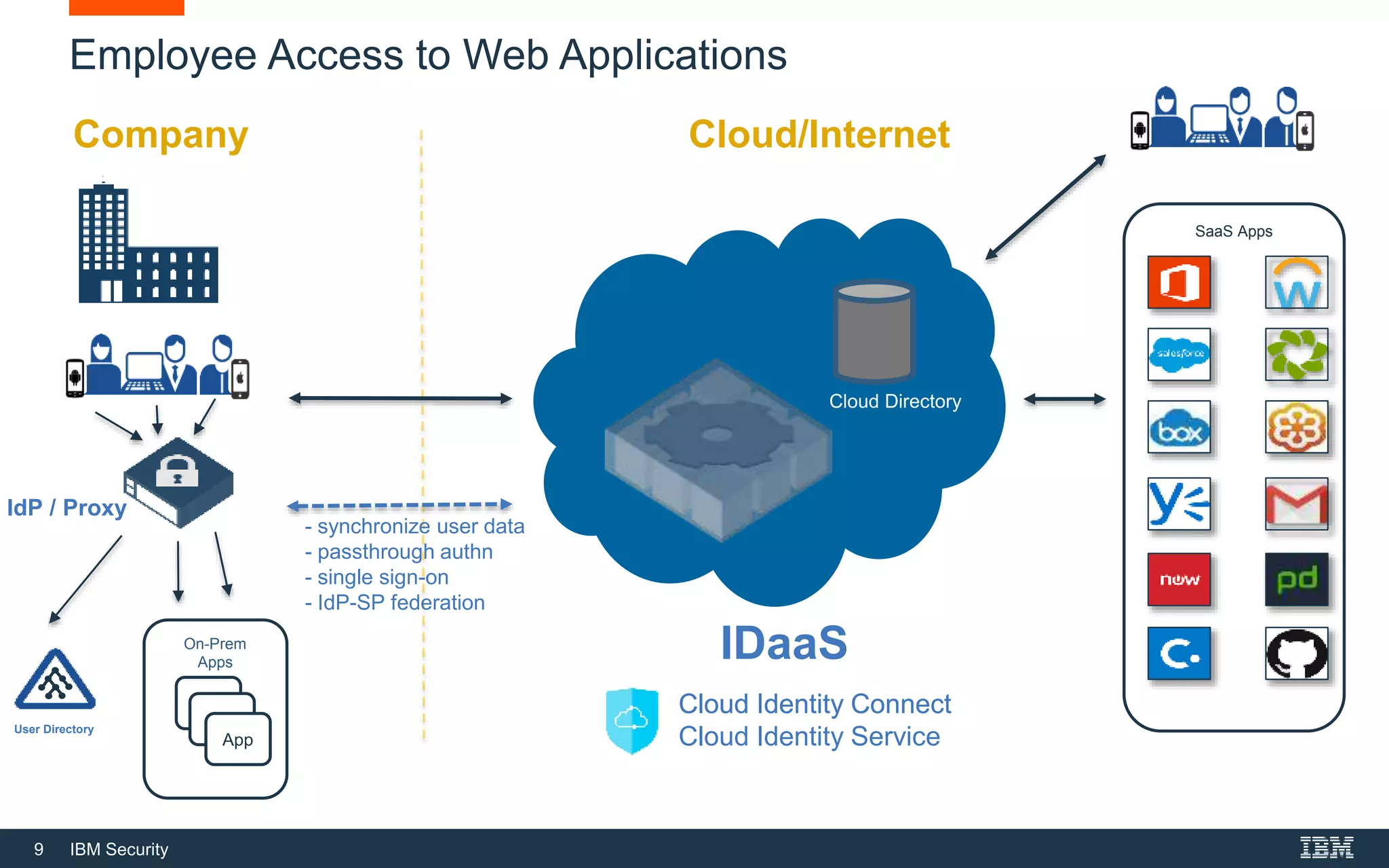
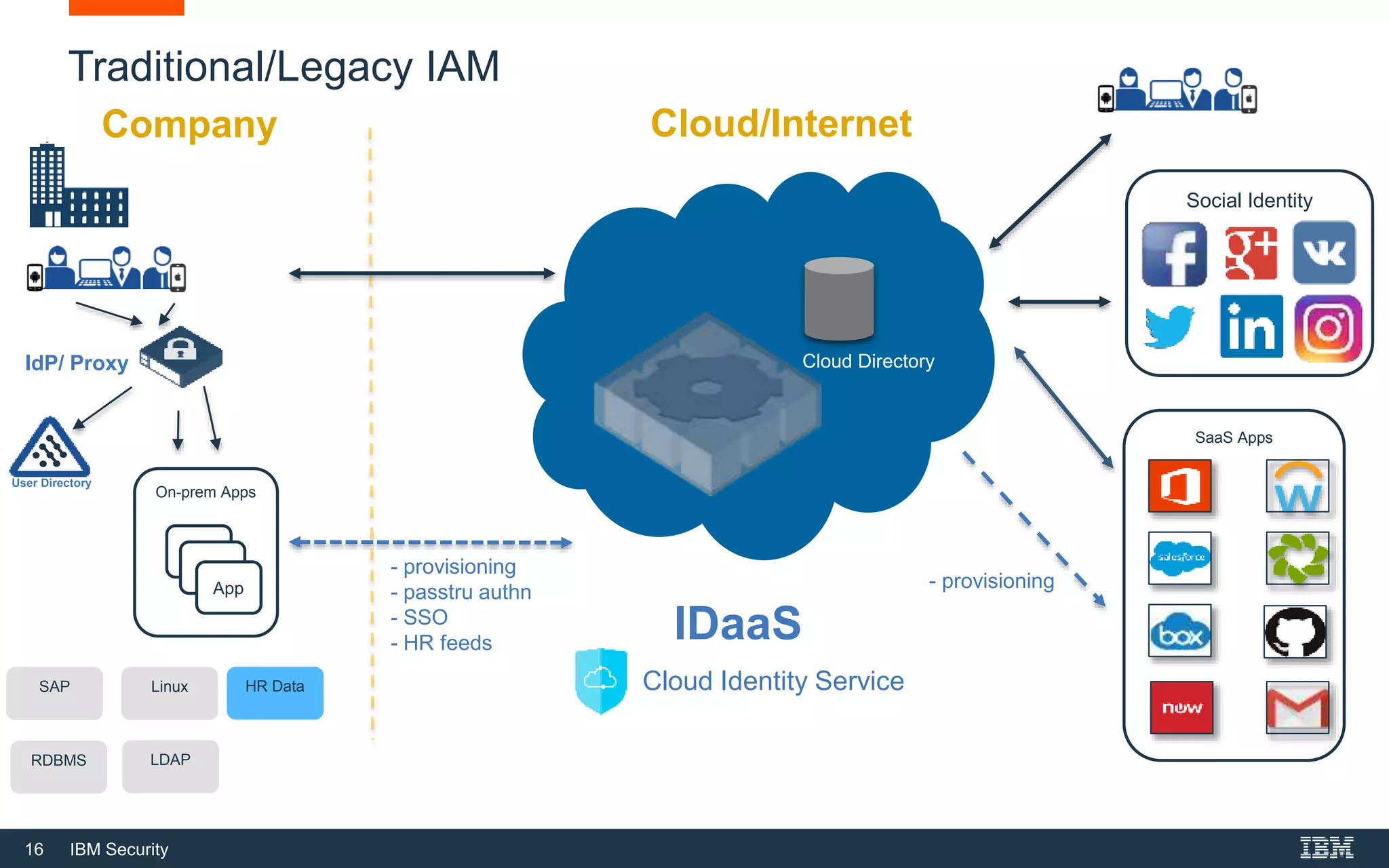
The webinar on February 28, 2018, led by IBM Security experts, discussed the concept of Identity as a Service (IDaaS) and its use cases, highlighting employee and consumer access management. It explored the differences between adopting IDaaS versus on-premises solutions and the responsibilities of organizations in managing IAM programs. Additionally, resources for further information on cloud identity were provided.