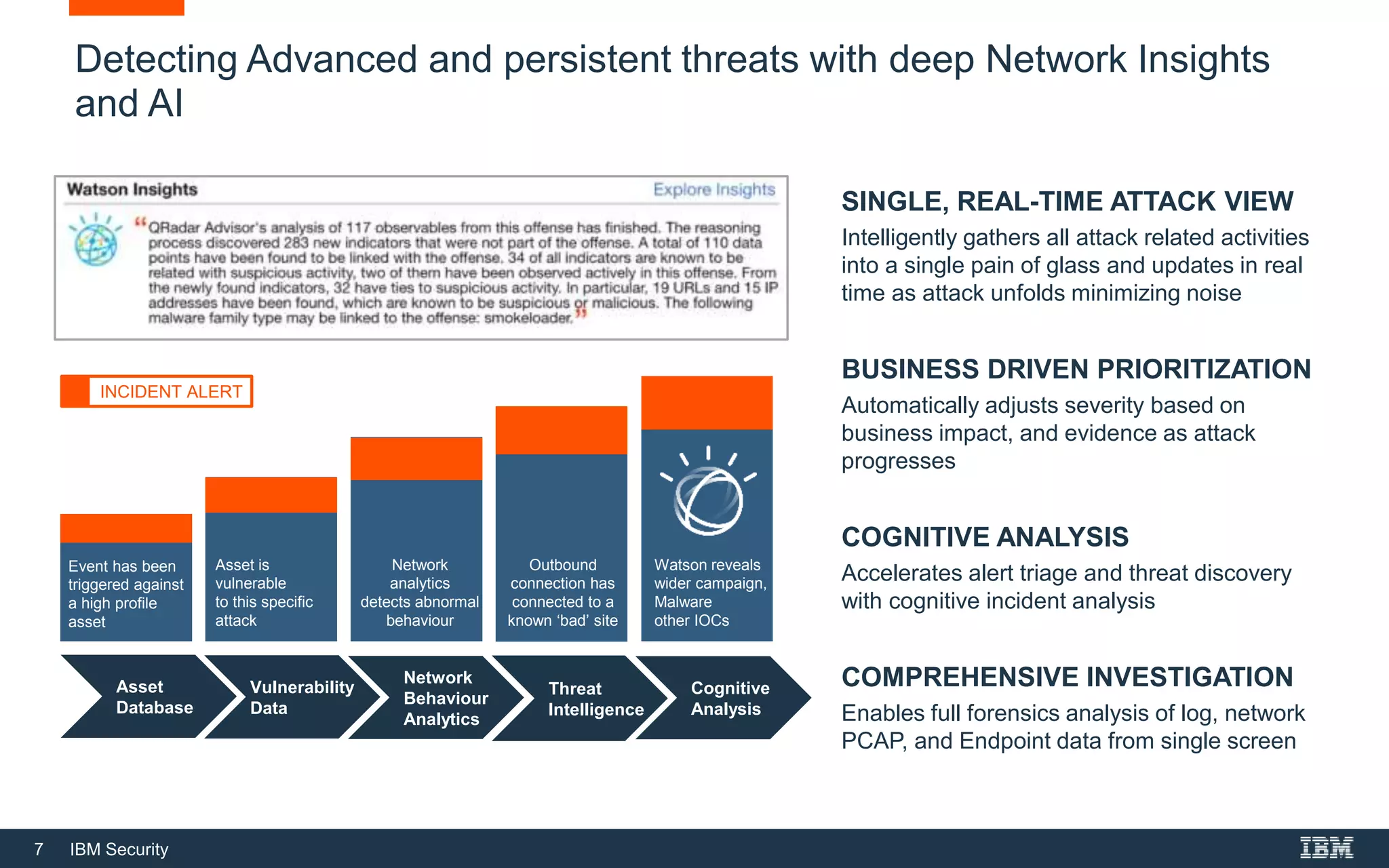
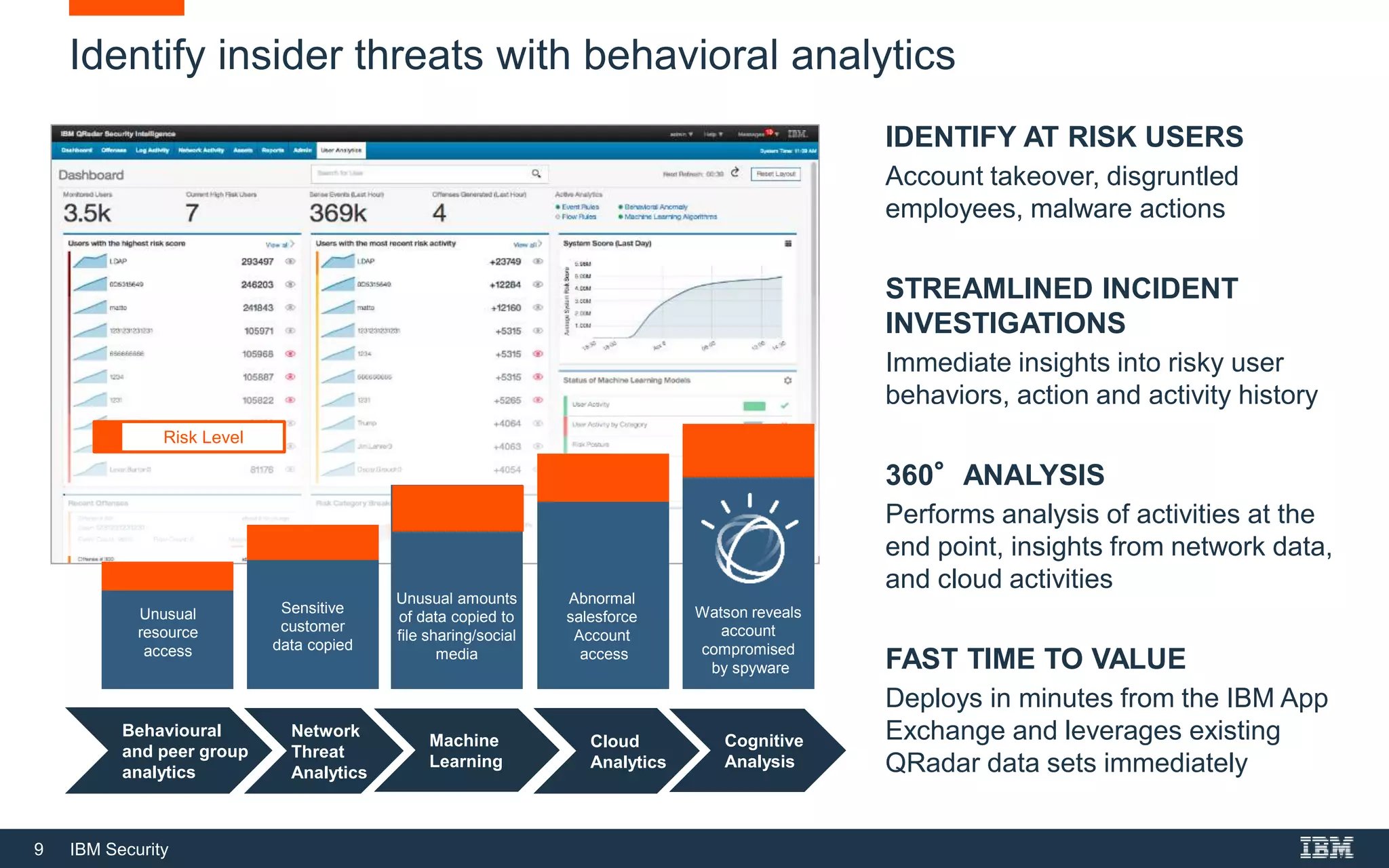
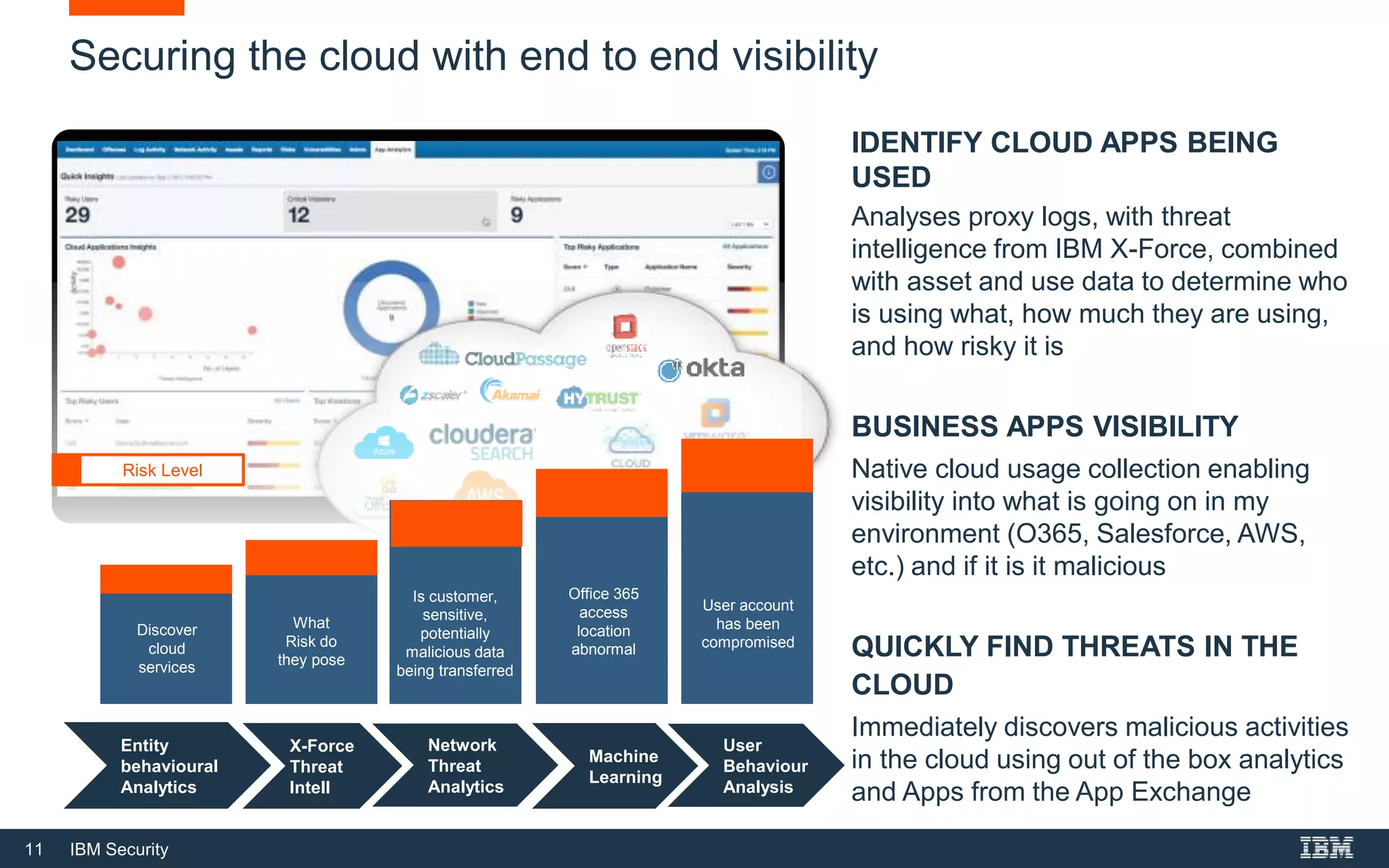
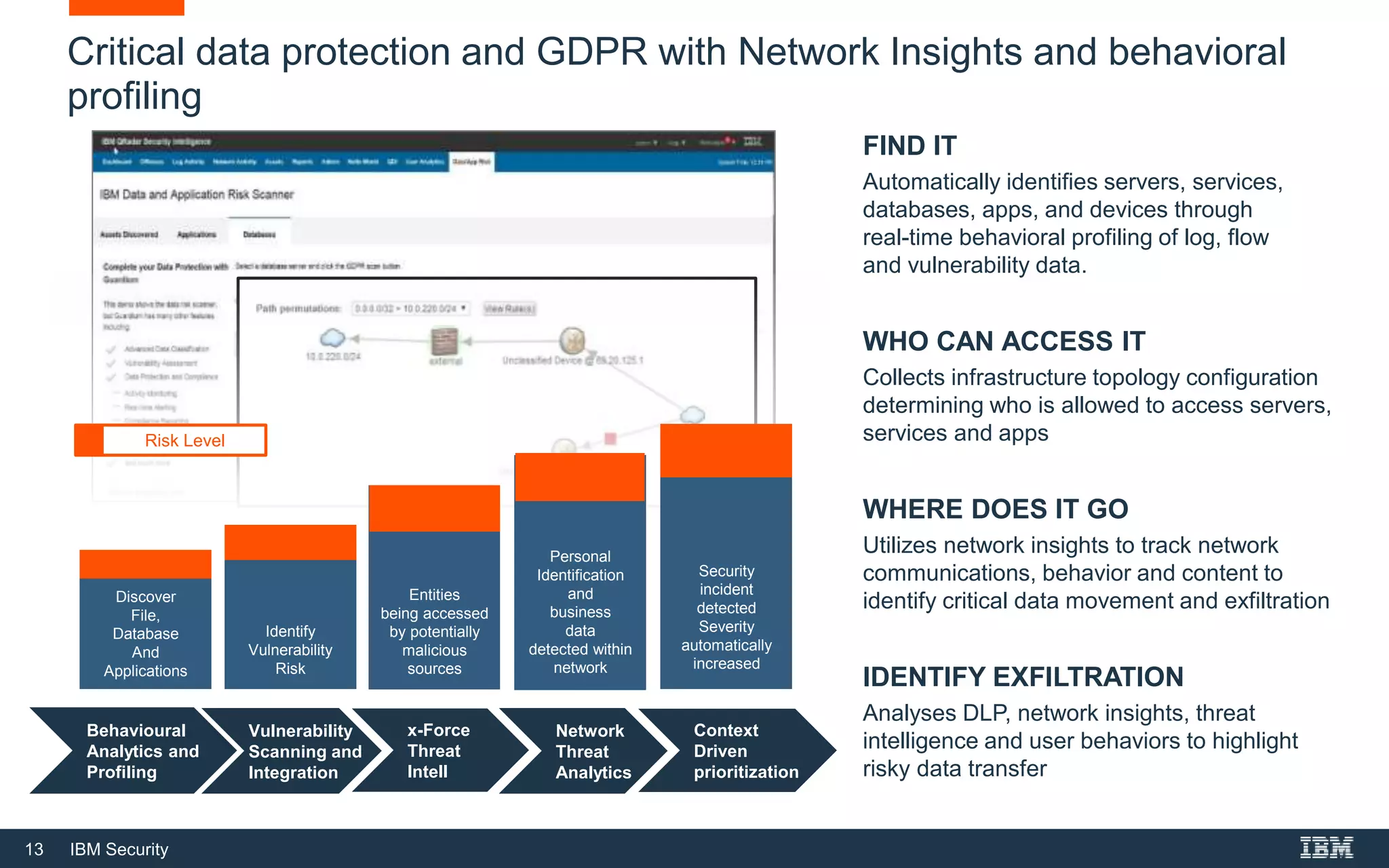
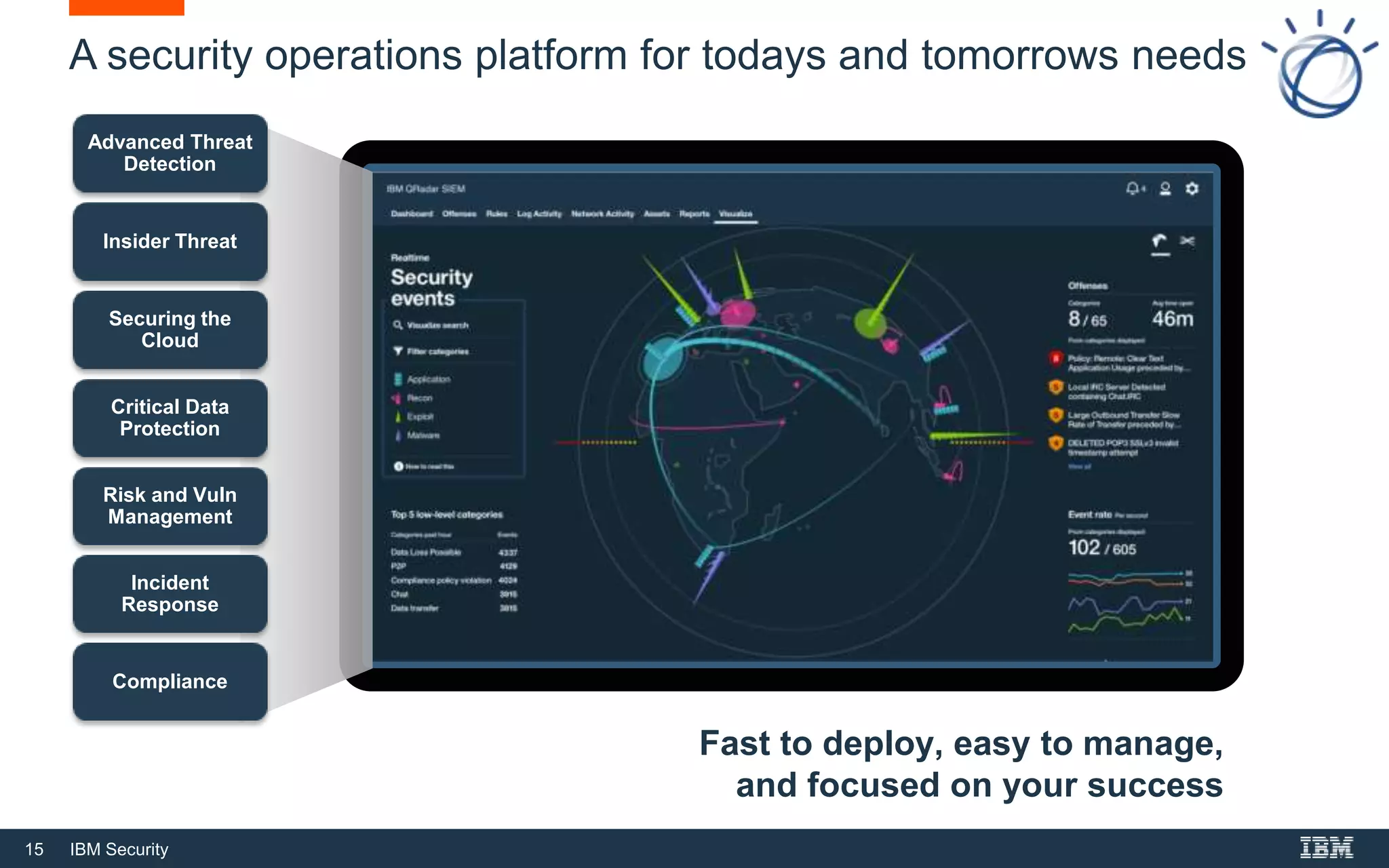
The document outlines IBM Security's solutions for modern security operations, emphasizing the importance of advanced threat detection, insider threat identification, and cloud security. It highlights the need for real-time threat identification, risk management, and compliance, addressing challenges such as alert fatigue and user behavior analysis. Additionally, it promotes IBM's Qradar as an integrated solution for managing security operations effectively and efficiently.